Zero trust vs. defense in depth: What are the differences?
Security administrators don't have to choose between zero-trust and defense-in-depth cybersecurity methodologies. Learn how the two frameworks complement each other.
Cybersecurity teams have a number of security frameworks to choose from. In some cases, administrators must choose one framework or philosophy over another. In others, multiple frameworks that focus on different aspects of an enterprise's overall security posture can be used.
One situation where multiple methodologies can simultaneously be applied to the same enterprise involves defense in depth and zero trust.
What is defense in depth?
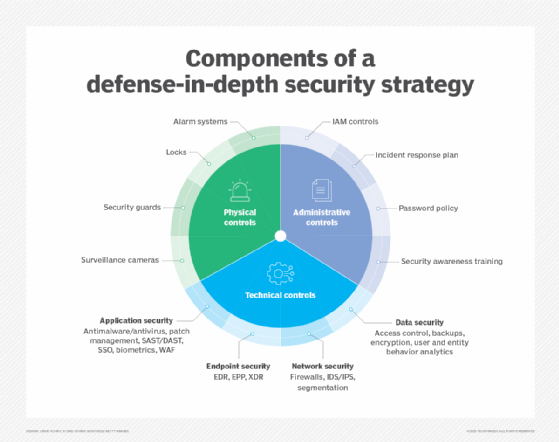
A defense-in-depth strategy involves the use of multiple security tools and mechanisms in unison. The idea is that, if one security tool fails or is bypassed by an attacker, other properly configured tools prevent unauthorized access.
This strategy has been popular over the past few decades for two main reasons:
- A layered security approach to tools helps ensure gaps between security policies are fewer and harder to find.
- Defense in depth helps protect against human errors that cause misconfiguration to a security tool.
Without a defense-in-depth strategy in place, gaps and misconfigurations can open the door to attackers probing for an easy way into the network.
Benefits of defense in depth
The top benefit of defense in depth over zero trust is that, if one part of the layered security fails, other layers in the security architecture are already in place to keep business-critical data safe from attackers.
Layering defenses can also slow down attackers, improving the chances they will be detected by security mechanisms or security teams.
Challenges of defense in depth
A downside of defense in depth is that attacks continue to change day by day. Techniques used and accounted for yesterday could fall out of favor, and a different or new technique used today could be able to get past multiple security layers.
Another challenge is integrating the layers, which hinders collaboration and can delay threat detection. Having multiple layers in defense in depth also means that management becomes more complex for security teams.
What is zero trust?
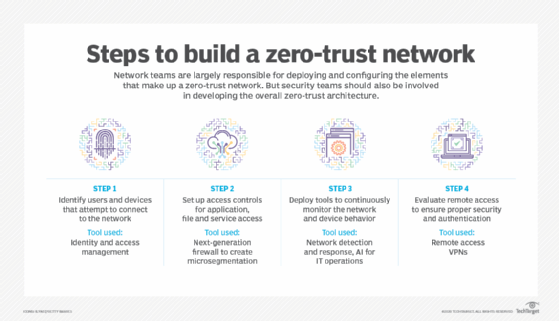
Zero trust is a network security model that has more specific principles than those of defense in depth. With zero trust, the goal is to never trust anyone or anything that accesses and communicates with applications and services inside a corporate network. Zero trust uses the principle of least privilege to ensure that only the correct devices and users connecting to the network, as well as workloads within public and private data centers, are allowed and expected to transmit and receive data.
Benefits of zero trust
The benefit of zero trust is contained within the adage of "never trust, verify everything." With zero trust, users must constantly prove they have appropriate permissions, from initial login and thereafter. This means that, even if attackers infiltrate a system, they can't necessarily do any damage or exfiltrate data.
Despite the restrictive-sounding nature of zero trust, it can boost UX through tools such as single sign-on, reducing the worry around password mismanagement.
Other benefits include improved monitoring, acting as a barrier to lost or stolen data, and the ability to centrally manage application and data security policies.
Challenges of zero trust
Much like defense in depth, managing zero trust can be complex, especially during implementation. The larger the company, the higher the number of authentication and authorization features required to keep data secure.
Another common complaint of zero trust is that it requires more staff or the use of managed service providers.
The case for zero trust and defense in depth
Taking a narrow view of what defense-in-depth and zero-trust strategies aim to deliver, one might assume the two approaches are mutually exclusive. In fact, the opposite is true. For example, zero-trust principles can be included as a part of an overall defense-in-depth strategy that also incorporates other application and data protection features that are not considered to be part of zero trust.
Even more interesting, however, is that defense-in-depth philosophies can be included in zero-trust deployments. For example, security administrators can lock down users' accounts so that they only have the right to operate certain applications and services, based on business needs. In addition, admins might create logically segmented security zones that restrict access to portions of a network that users never need. Thus, if a user account were to be compromised, not only is that account restricted from accessing only those resources that the account is configured to reach, but the security zones also further limit this access if an account is misconfigured or manipulated.
Editor's note: This article was updated in June 2024 to improve the reader experience.
Andrew Froehlich is founder of InfraMomentum, an enterprise IT research and analyst firm, and president of West Gate Networks, an IT consulting company. He has been involved in enterprise IT for more than 20 years.







