An overview of the CISA Zero Trust Maturity Model
A zero-trust framework blocks all attempts to access internal infrastructure without authentication. The CISA Zero Trust Maturity Model is a roadmap to get there.
Zero trust is a rigorous approach to security that presumes no user, device or network is trustworthy. The principal benefit of a zero-trust policy is that it blocks any attempt to access internal IT infrastructure resources without proper and continuous authentication. Adding zero trust to any IT environment ensures it delivers a completely secure and impenetrable barrier to unauthorized access attempts.
What is the CISA Zero Trust Maturity Model?
First introduced as a discussion document in June 2021, the U.S. Department of Homeland Security's (DHS) Cybersecurity and Infrastructure Security Agency (CISA) Zero Trust Maturity Model aims to help organizations in their transition to zero trust.
The model supports and conforms to requirements specified in Executive Order 14028: Improving the Nation's Cybersecurity, which notes that the U.S. "faces persistent and increasingly sophisticated malicious cyber campaigns that threaten the public sector, the private sector, and ultimately the American people's security and privacy. The federal government must improve its efforts to identify, deter, protect against, detect, and respond to these actions and actors."
CISA's Zero Trust Maturity Model provides a framework for organizations in the public and private sectors to strengthen their efforts to prevent unauthorized access to their technology infrastructures and information resources via zero trust.
7 zero-trust foundational rules
The DHS document lists the following seven foundational rules of zero trust as defined in the NIST Special Publication (SP) 800-207 (2020), Zero Trust Architecture:
- All data sources and computing services are considered resources.
- All communication is secured regardless of network location.
- Access to individual enterprise resources is granted on a per-session basis.
- Access to resources is determined by dynamic policy.
- The enterprise monitors and measures the integrity and security posture of all owned and associated assets.
- All resource authentication and authorization is dynamic and strictly enforced before access is allowed.
- The enterprise collects as much information as possible about the current state of assets, network infrastructure and communications, and uses it to improve its security posture.
The executive order calls for government agencies to develop migration plans toward zero-trust security environments for technology infrastructures. The CISA Zero Trust Maturity Model is one of the approaches to the achievement of zero trust, which the model document acknowledges may take time to implement.
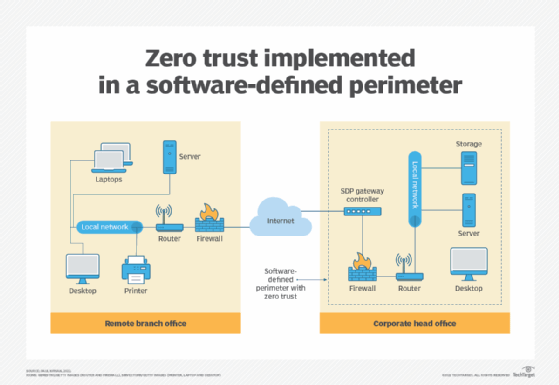
The graphic below depicts an example of a software-defined perimeter (SDP) with zero trust. In this example, an SDP controller manages all user and device verification and authentication activities before permitting a connection to be established with internal network and IT resources. The SDP creates a zero-trust wall around the internal network asset, preventing all access attempts except those that have been fully authenticated.
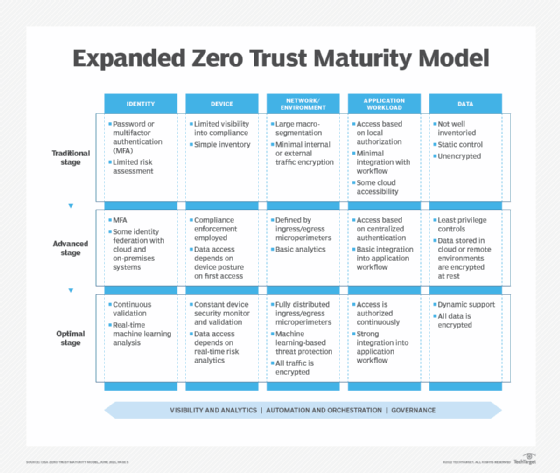
Zero Trust Maturity Model stages
Acknowledging that the transition to a zero-trust environment will take time and investment, the Maturity Model recommends a three-stage approach to zero trust:
- Traditional zero-trust architecture. Largely a manual -- rather than automated -- environment, the starting point is characterized by manual operational procedures, nominal security policies and limited enforcement, manually implemented incident response and mitigation processes.
- Advanced zero-trust architecture. Next up is a nominal increase in automation, centralized management, better policy enforcement, more specific dependency on external systems and enhanced incident response and mitigation procedures.
- Optimal zero-trust architecture. The final stage uses automated systems across most elements of the security infrastructure and has better alignment with relevant security standards, enhanced centralized management, better policy enforcement and enhanced incident response and event mitigation.
Each stage contributes to the overall progression to a strong and secure zero-trust architecture that complies with the five pillars in the CISA Zero Trust Maturity Model: identity, device, network/environment, application workload and data.

The figure above shows the progression from a traditional zero-trust approach through to an optimal zero-trust environment. The model envisions organizations making incremental changes and improvements across all five pillars of the model over time toward an optimized state.
Each pillar also has elements and specifications regarding visibility and analytics, automation and orchestration, and governance. Each of these three layers ensures zero-trust activities address these important elements throughout the transition to an optimized environment.
The 5 pillars of the CISA Zero Trust Maturity Model
- Identity. This pillar describes characteristics of each user or agency. Among the elements that describe each entity are authentication, risk assessments and tools to identify each entity, whether they are manual or automated.
- Device. Any device connecting to a user network is characterized by this pillar. It addresses asset tracking and management, access to the device and how the device complies with security rules and protocols.
- Network/environment. This addresses the network environment, whether hardware-based, wireless or linking to networks, such as the internet. It also examines the presence of encryption, threat identification and mitigation resources, and how the network is physically and logically configured.
- Application workload. This pillar examines the systems and applications being executed on site as well as remotely, such as in cloud environments. The process analyzes how applications are accessed, security measures that protect applications and the presence of threat identification and mitigation measures.
- Data. All aspects of securing production data, data storage, data management and data protection are examined in this pillar. Among the issues addressed are data access, data encryption and data inventory management.
What's next for the Zero Trust Maturity Model?
The current version of the CISA Zero Trust Maturity Model, when released in 2021, was largely for review and comment. An updated version, 2.0, had been rumored for midyear 2022. It is expected to include enhancements to the five pillars and their characteristics, as well as guidance for organizations to move forward on their zero-trust development activities.








