security posture
What is security posture?
Security posture refers to an organization's overall cybersecurity strength and how well it can predict, prevent and respond to ever-changing cyberthreats.
An organization's security posture includes its networks, information security, network security, data security and internet security, as well as penetration testing, vendor risk management, vulnerability management, data breach prevention, security awareness training for employees to prevent social engineering attacks and other security controls.
A company's security posture, however, isn't static. Rather, it is constantly changing to respond to new vulnerabilities and threats in the cybersecurity landscape. As such, enterprises are transitioning from fragmented tools and outdated security frameworks to end-to-end security postures that can protect against these new security threats and vulnerabilities.
How a strong security posture protects companies
A strong security posture aims to protect organizations against cybersecurity threats by detecting and preventing malware intrusions -- like ransomware -- and data breaches. It also prevents the theft of intellectual property.
For example, a company that requires employees, third-party vendors and customers to use two-factor authentication or multifactor authentication -- or at least cycle through complex passwords -- to log in to its website can keep corporate data safe.
In addition, implementing firewall, antivirus and antimalware tools as part of a strong security posture can make it difficult for cybercriminals to break into its network and steal sensitive data. This strategy helps deter cyber attacks.
Implementing anti-phishing and email security tools as part of a comprehensive security posture can help a company stop spam from making its way to users' inboxes. These tools also scan messages and remove any malicious content before forwarding them to the company's mail server.
Strategies to strengthen security posture
Organizations are constantly faced with a variety of security issues, such as how to reduce vast attack surfaces; how to secure their networks, devices, endpoints and other IT assets and how to keep hackers from breaching their systems. There are many ways companies can enhance their security policies to meet these challenges, including the following:
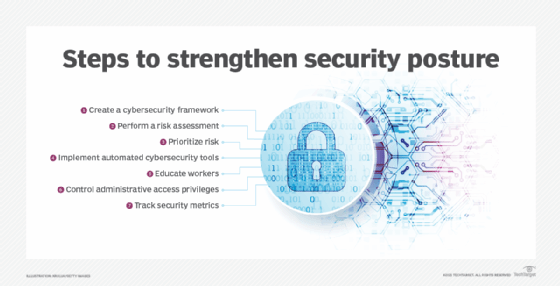
- Create a cybersecurity framework. Companies should align their security requirements with the goals and objectives of the business.
- Perform a risk assessment. A cybersecurity risk assessment identifies the level of vulnerability across an organization's assets. The results enable organizations to determine what they need to do to improve their security postures. They also help identify the security controls that should be put in place to protect the business against future attacks.
- Prioritize risk. After identifying the asset vulnerabilities, enterprises should then rank them based on the overall risk they pose to the business and determine what to work on first.
- Implement automated cybersecurity tools. Using automated tools can help reduce incident response times and prevent hackers from infiltrating the network.
- Educate workers. Security awareness training should be part of the onboarding process. In addition, companies should regularly test employees on their knowledge of the organization's cybersecurity policies, including ones related to social media.
- Control administrative access privileges. Organizations should only grant administrative access privileges to a small group of employees, like security teams. Letting too many people modify hardware and operating system settings can be disastrous to companies' security postures.
- Track security metrics. Security metrics enable companies to accurately measure the effectiveness of their cybersecurity posture. Security metrics can also help organizations uncover ways to mitigate risk, as well as help with prioritizing future potential risks. To be effective, a security metrics program depends heavily on what enterprises decide to measure. Consequently, companies must track the metrics that affect the business from an operational and strategic perspective.
Security posture assessment
Conducting a security posture assessment enables organizations to understand where they stand in their cybersecurity journeys. It can help an organization strengthen its security posture by providing a concrete cybersecurity roadmap.
Security posture assessments are based on the following assumptions:
- Companies must know the importance of the data they have and what tools they have to ensure data protection.
- Enterprises should know where they stand in terms of their security status.
- Organizations must know what they need to develop and what direction to go to get there.
- Companies need to know how to keep the momentum of security going.
A security posture assessment helps organizations design and develop appropriate cybersecurity roadmaps and functionality within their business continuity planning and overall security programs. In addition, security posture assessments combine all the aspects of a company's cybersecurity strategy into one comprehensive assessment to provide a view of its internal and external security posture.
Security posture assessments help enterprises assess and improve their security postures in the following ways:
- Identifying and managing the value of their data.
- Defining the threat exposure and security risks of their data.
- Evaluating if they have appropriate, reliable and efficient security measures in place.
- Recommending a concrete action plan (i.e., an incident response plan) to help companies better control their risk exposures and strengthen their cybersecurity defenses.
Learn how data security posture management complements an organization's security posture.





