Use network standardization to facilitate automation
Network teams can automate and standardize network designs to improve configurations, simplify operations and more easily implement changes within their networks.
Standardized and simplified network design and configuration are essential foundations for a smoothly functioning system. Ensuring consistency across the network facilitates the implementation and effective use of automation, making it easier to deploy changes and validate network operations across your infrastructure.
For example, using a single Git hosting service such as GitHub, GitLab or Bitbucket as the network source of truth instead of multiple hosting services ensures engineers are familiar with one specific platform for DevOps.
This article explores these functions further. But first, let's examine what network equipment vendors recommend.
Using building block designs
Network equipment vendors recommend that network teams adopt building block designs to further enhance standardization and simplify automation. Each building block should specify the exact hardware, OS, interface selection and configuration used. To reduce system complexity, teams should minimize the number of building block variations their automation systems handle.
For example, it's best to have two remote site designs: an older design to transition from and a new design to transition to. Teams might also have small and large site designs for a total of four. Note that supporting more unique designs often increases the effort needed to maintain the automation system.
One key challenge in managing multiple designs is handling significant design variances -- differences that automation can't deploy. For example, hardware changes such as equipment refreshes or interface updates fall into this category because they require more than just a configuration update. Contrast that with a simple configuration change, like updating an access control list, which is easily deployed by automation.
It's tempting to deploy a nonstandard hardware configuration to handle new site requirements, but the downside is that it requires additional complexities in the automation process. Even simple differences, like changes in the interfaces used for uplinks, can complicate automation. Thus, when emergency situations arise that require exceptions to standards, teams should work to standardize them as soon as possible.
Automation and network standardization
When your network follows a consistent design, automation tools can reliably execute critical functions such as maintaining an up-to-date network device inventory, monitoring for configuration drift, conducting configuration audits, applying network device OS updates, performing configuration remediation, managing changes efficiently, enforcing security policies and using AI agents.
Let's explore these functions.
1. Network device inventory
A network device inventory guarantees the recognition of all devices. Regularly scheduled network scans might reveal rogue or unprotected devices that aren't protected by a security patch, so teams should make sure their networks are secure. Network inventories can also remove any old, forgotten devices that pose an operational risk to the network.
Automation plays a crucial role in this process by continuously discovering a device and getting details about it. The process also has the ability to catalog network devices, detect unauthorized additions and flag discrepancies in real time. One popular open source tool is NetBox; alternative products include Datadog and SolarWinds.
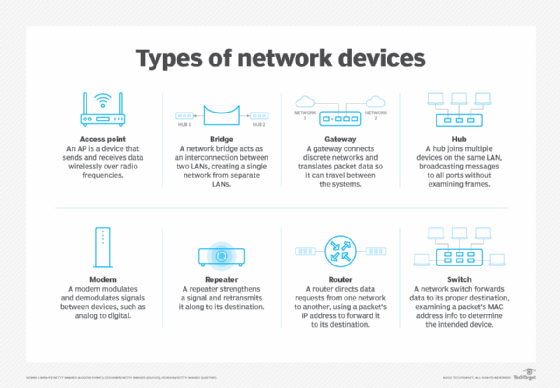
2. Configuration drift
An automation system can collect configurations and monitor changes once the network inventory recognizes devices on the network. Incorrect changes are the greatest cause of network outages. Network teams will find that tracking configuration drift is a critical function in failure diagnosis to identify what changed. Standardized designs make it easier to determine when something changes and whether the change was caused by an outage.
3. Configuration audit
A configuration audit identifies devices with configurations that don't match a team's best practices and policies.
Network teams can guarantee that standardized configurations are operational by performing an audit that compares device configurations against standardized configuration templates and by remediating noncompliant configurations. The templates specify required commands that should exist and forbidden commands that shouldn't exist. The templates are specific to each device function and model.
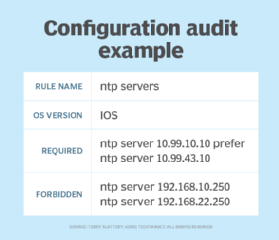
This audit identifies configurations that don't match the standards for teams to bring them into compliance. Teams should also address any differences in hardware, like device vendors and models, before standardizing the related configuration elements.
Some examples of popular configuration auditing tools are Kyverno for Kubernetes network policies, SolarWinds Network Configuration Manager and Infoblox NetMRI.
4. Network device OS updates
Network teams should also standardize the OS versions used on their devices to simplify updates and patch processes. The initial inventory process should identify the OS used on each device. Keep the OS patched to avoid network security holes and subtle bugs that affect a network's operation. The patching process will be much smoother on a network that minimizes the number of OSes.
5. Configuration remediation
Remediation and configuration updates are where automation provides its greatest value. For example, updating passwords, modifying a critical access control list or making a routing protocol change across hundreds of routers are actions made simpler by starting with a known, standard configuration.
6. Change management
Change management also becomes more efficient with automation. If all network configurations are stored in one Git repository, engineers can easily track changes, enforce version control and roll back to previous configurations if needed. Different tools offer distinct advantages when choosing a standard platform for change management.
For example, a database-driven platform like NetBox provides a structured and enriched source of truth for network configurations. On the other hand, a Git-based platform like Nautobot -- born out of NetBox -- extends Git's version control benefits while allowing for more automation-driven workflows, including CI/CD pipelines for network configuration updates.
7. Security
Standard designs are important for other reasons, including security. Network teams should consistently apply good security configurations across the entire infrastructure to prevent bad actors from accessing the network. For example, with cloud networking, enforce a standardized routing policy where all traffic is routed through a central security VPN before reaching the internet or other virtual private clouds.
8. Network troubleshooting
Standardization greatly simplifies network troubleshooting because standard operating procedures are easier to create and maintain. For example, if every switch is configured to send logs to a centralized server, engineers can easily access the logs to track down the root cause of an issue.
9. Standardization across public clouds
Standardization should extend beyond on-premises networks to cloud and multi-cloud environments. For example, teams using infrastructure-as-code tools like Terraform or OpenTofu can use one configuration language to define networking policies across AWS, Azure and Google Cloud. This guarantees uniform security groups, firewall rules and routing configurations.
10. AI-driven network automation
Creating a digital twin of the network and using AI to interact with it using natural language rather than complex network configuration is starting to gain traction. When an interaction is made using natural language, AI agents preconfigured with a knowledge base of network instructions understand the language and interact with the network device or cloud infrastructure on behalf of the human.
It's important to standardize a knowledge base for your AI agents. The knowledge base can be built with vendor-neutral instructions. For example, when a network engineer says, "Set the speed of all active Gigabit Ethernet interfaces with an IP address in subnet 192.168.1.0/24 to 10 Gbps," the agent translates that request into a vendor-neutral format. To see more of this in action, check out John Capobianco's YouTube channel.
Automation and network standardization complement each other
Automation and network standardization work together to improve network operations and reduce human error. Standard network designs enable consistent application of automation across larger parts of networks. In turn, automation identifies exceptions to network standards and enables the network team to implement configuration changes quickly and accurately. This synergy results in a more secure, scalable and resilient network that's ready to support future technologies like AI-driven automation.
Editor's note: This article was updated in February 2025 to reflect the latest developments in network standardization as it relates to automation.
Charles Uneze is a technical writer who specializes in cloud-native networking, Kubernetes and open source.
Terry Slattery is an independent consultant who specializes in network management and network automation. He founded Netcordia and invented NetMRI, a network analysis appliance that provides visibility into the issues and complexity of modern router- and switch-based IP networks.







