What is promiscuous mode in networking?
In computer networking, promiscuous mode is a mode of operation in which a network device, such as a network interface card (NIC) or an adapter on a host system, can intercept and read in its entirety each network packet that arrives instead of just the packets addressed to the host. Usually, data packets are filtered by a NIC so that it can only see the traffic it is supposed to see. Promiscuous mode removes this limitation so that the NIC can read all network traffic.
Promiscuous mode is a popular security, monitoring and administration technique that enables the network operating system (NOS) to view or "sniff" all network traffic. This helps network admins review network activity to diagnose and troubleshoot problems and identify network intrusions. However, malicious actors can also exploit the mode to snoop on network traffic, either to compromise devices or to steal confidential or sensitive data.
What does promiscuous mode do?
Promiscuous mode applies to both wired and wireless NICs. In both cases, turning on the mode ensures that every data packet that is transmitted is received and read by the controller. Thus, it causes the controller to pass all traffic it receives to the central processing unit instead of just the frames it is specifically programmed to receive.
This means the NIC does not filter packets. Instead, it passes each packet on to the NOS or any monitoring application installed on the network. This enables a network monitoring tool to examine the transmission content for potential threats and review network traffic for diagnostic purposes -- e.g., to pinpoint performance issues or find the root cause of latency problems.
In a bridge network, the NIC might be required to operate in promiscuous mode. In such a case, the mode must be supported by each network adapter and the input/output driver in the host operating system. Some OSes require superuser privileges to enable this mode.
Promiscuous mode can also be configured to make packet data accessible to a guest OS or a visitor on the host system.
Promiscuous mode and packet sniffing
Within networks, the promiscuous mode of operation is used for packet sniffing -- the practice of collecting and logging packets that pass through the network for analysis, such as traffic or bandwidth usage analysis.
Any NIC attached to a network can receive all traffic, but most are configured not to do so. A packet sniffer adopts promiscuous mode to change this configuration. The network adapter can be in promiscuous mode for the following reasons:
- It was manually configured using the ifconfig command or ip link set.
- A monitoring tool is being used.
The packet sniffer collects all the traffic flowing through the physical interface, separates or reassembles it as required, and then logs it per the network's requirement. This enables the NIC or adapter to pass all network traffic up the stack, regardless of the packets' destination addresses.
Most packet sniffers today are software-based, although hardware packet sniffers are also used. One example of packet sniffer software is tcpdump. Tcpdump is a free network packet analyzer for specific interfaces. Tcpdump, which runs under a command-line interface, enables users to display TCP/IP and other packets transmitted or received over a network. The packet data can be saved in a file for later analysis -- for example, to troubleshoot connectivity issues or to discover what Domain Name System queries the device is sending.
Wireshark is another popular packet sniffing and analysis program. This open source, freely available tool captures and presents detailed live packet data from a network interface to help users troubleshoot network problems, identify security gaps, verify network applications and debug protocol implementations. Wireshark versions are available for Windows and Linux, and they include features to filter packets, search packets, save packet data and export packets in various file formats.
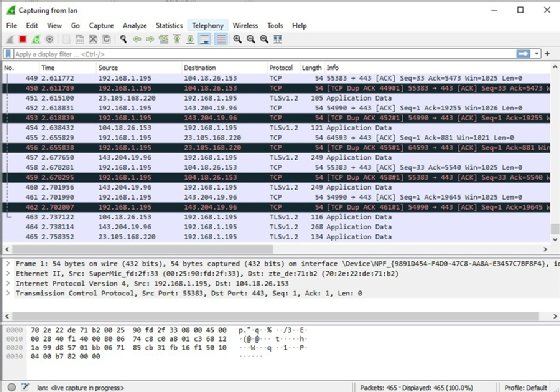
Applications of promiscuous mode
Promiscuous mode is often used to monitor network activity and diagnose connectivity issues. It is sometimes given to a network snoop server that captures and saves all packets for analysis -- for example, to monitor network usage. With the help of a packet sniffer, network admins can gain useful insights into network behavior and determine if those behaviors are desirable. They can then determine what actions to take to optimize network performance.
Network intrusion detection systems and intrusion prevention systems use promiscuous mode to analyze packets and identify anomalous, suspicious or potentially malicious activity.
What are the drawbacks of promiscuous mode?
Promiscuous mode is very useful for network monitoring, network analysis and troubleshooting, and network intrusion detection. However, this mode is considered unsafe due to its ability to access all network traffic on a segment. For example, in a system with multiple virtual machines, promiscuous mode lets every host see all network packets destined for all other VMs on that system, not just packets destined for their VMs. This can open the door to privacy violations and data theft, especially if one or more hosts are unauthorized or malicious systems belonging to cyberattackers.
Promiscuous mode also has certain limitations. For example, while debugging problems, admins should not use tcpdump with a NIC in promiscuous mode because tcpdump will not show which data packets the system accepts under normal conditions. Also, relying on the Internet Protocol addresses in tcpdump's output to determine the right packet will yield incorrect insights.
The mode can also display wrong information in other situations. For example, if the Ethernet address display is not turned on and the NIC is in promiscuous mode, it will -- incorrectly -- show that there are no problems on the network. Without the proper insight into actual problems, performance issues and even network outages could occur. To prevent such incidents, turning on the Ethernet address display in tcpdump is important.
How to enable promiscuous mode in Windows
The built-in command-line tools in Windows cannot directly enable promiscuous mode, so users will need to use third-party tools like Wireshark or the Nmap Project's Npcap in administrator mode.
It's easy to turn on promiscuous mode in Wireshark:
- Open Wireshark.
- Select the wireless adapter.
- Under the adapter's options, check "Enable promiscuous mode."
To turn on promiscuous mode with Npcap, type the command npcap -p <your adapter name>.
How to enable and disable promiscuous mode on a NIC with XenServer
Citrix XenServer is a server virtualization platform that uses a hypervisor, Xen, to enable the virtualization of multiple servers as a single, centralized resource pool. XenServer includes a text console through which promiscuous mode can be enabled on a physical NIC.
This requires running the command # ifconfig eth0 promisc.
Run the ifconfig command, and notice the outcome:
eth0 Link encap:Ethernet HWaddr 00:1D:09:08:94:8A
inet6 addr: fe80::21d:9ff:fe08:948a/64 Scope:Link
UP BROADCAST RUNNING PROMISC MULTICAST MTU:1500 Metric:1
RX packets:23724 errors:0 dropped:0 overruns:0 frame:0
TX packets:7517 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:2169478 (2.0 MiB) TX bytes:5423377 (5.1 MiB)
Interrupt:17The XenServer text console can also be used to disable promiscuous mode, using the command # ifconfig eth0 -promisc.
Run the ifconfig command again. If there are no errors, promiscuous mode has been disabled.
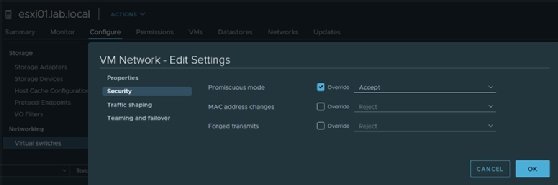
What is nonpromiscuous mode?
In promiscuous mode, the NIC lets all packets through, so even frames intended for other machines or network devices can be read. But in nonpromiscuous mode, when the NIC receives a packet, it drops it unless it is addressed to its specific media access control address or is a broadcast or multicast-addressed frame. Simply put, the NIC captures only traffic that's specifically addressed to its host.
So, when a data packet is transmitted in nonpromiscuous mode, all the local area network (LAN) devices listen to the data to determine if their network address is included in the packet. If it's not, the packet is passed on to the next LAN device until it reaches the correct network address. That device then reads the data.
Most NICs operate in nonpromiscuous mode until promiscuous mode is turned on.
Wireshark and tcpdump both aid network administrators in packet analysis. Learn how Wireshark's simple graphical user interface contrasts with tcpdump's speed and scripting abilities.



