How to prepare for malicious insider threats
Stopping malicious insider threats is just as important as preventing external ones. Uncover what to look for and strategies to prevent insider threats before they cause damage.
External threats garner a lot of attention, but what about when the call is coming from inside the house?
Insider threats can undo a security team's efforts through careless or malicious actions. Negligent employees remain the top insider threats, causing 62% of all insider incidents. But malicious insiders can't be ignored. According to Tessian research, 43% of security incidents between March and July 2020 were caused by malicious insiders.
Mastering Defensive Security: Effective techniques to secure your Windows, Linux, IoT, and cloud infrastructure, written by Cesar Bravo and published by Packt, provides a thorough breakdown of the tactics and vectors security professionals must consider when developing a cybersecurity strategy, including a chapter on how to prepare for insider threats.
In this excerpt from Chapter 4, Bravo explains how to spot negligent and malicious insider threats, as well as tools and strategies to combat them, including segregating duties, job rotation, mandatory vacations and analyzing logs. Bravo then covers how to master social engineering, from common attack techniques to types of attacks and defending against them. Download a PDF of Chapter 4 to read more.
Check out an interview with Bravo where he discusses using Mastering Defensive Security for new and inexperienced infosec professionals.
Understanding layer 8 – the insider threat
As you probably know, users are also called layer 8 (as a joke) because they are on top of the 7-layer OSI model.
Another, more professional, way to call users is insiders. These insiders are a serious threat because they are already inside the network; therefore, many of our defensive systems and mechanisms (which are used to prevent users from accessing our network) will not apply to them.
Now, we will cover the different types of users that you need to consider when creating your cybersecurity strategy.
The inadvertent user
Based on a study from the Ponemon Institute, around 24 percent of data breaches are caused by innocent human errors. We call them innocent errors because they are normally user mistakes in which there is no user intention to cause harm to the data or the systems.
Many people believe that these kinds of incidents are rare or cause minimal impact. However, as you can see in the following diagram, a study from the Ponemon Institute, in 2020, shows a very different panorama:

I am going to summarize the most common mistakes or errors caused by inadvertent users, as follows:
- The use of weak passwords
- The repetition of passwords across systems
- The use of the same password for personal systems
- A lack of understanding of cybersecurity policies
- The misuse or abuse of privileged accounts
- Unattended devices
- The mishandling of data
- The installation of unauthorized software
- The inadvertent disruption of systems
- Careless internet browsing
- The use of free or open Wi-Fi
- "Click before think" (that is, in email attachments or links)
- The inadvertent disclosure of sensitive information
As mentioned earlier, these are innocent mistakes with no intention from the user to harm the company. However, there is another type of threat in which users are motivated to perform an attack, and they are known as malicious insiders, which we will be discussing next.
The malicious insider
First, let's try to gain an understanding of what types of motivation might cause an employee to turn into a malicious insider:
- Offers from external attackers to provide data or perform actions in exchange for money
- A lack of cybersecurity regulations and corporate sanctions
- A lack of controls
- The concentration of power
- Bad management
- Poor performance appraisals
- Disagreements with corporate policies, strategies, and coworkers
- Layoffs
The following figure shows the difference in terms of motivation between a malicious insider and an inadvertent user:
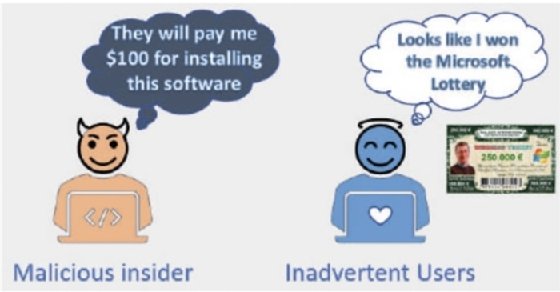
As you can see in Figure 4.2, understanding those motivations will help you to work with management to create strategies to avoid users turning into malicious insiders. Additionally, implementing a training and education strategy will be your best ally to prevent mistakes from inadvertent users.
How do you spot a malicious insider?
Here is a list of behaviors or actions that can help you to identify a malicious insider before is it too late:
- The download of big amounts of data (or a dump of databases)
- After-hours access to systems and information
- Escalation of privileges
- The download of sensitive information without a business need
- The creation of accounts without following established processes and controls
- The increased upload of data to unknown external addresses
- Repeated access requests to sensitive systems or data
- Requests for exceptions of a given cybersecurity policy
- The increased usage of external storage devices
- Abnormal attachments on emails (by size or by the number of files)
- Evidence or signs of the execution of hacking tools
- Unexpected or increased connection of personal devices to the corporate network
If you don't think that you will face a malicious insider, then think twice. A study published by inc.com shows that almost one in five employees will be willing to sell their password to an external attacker, and as you can see in Figure 4.3, they will do so for a very low price:
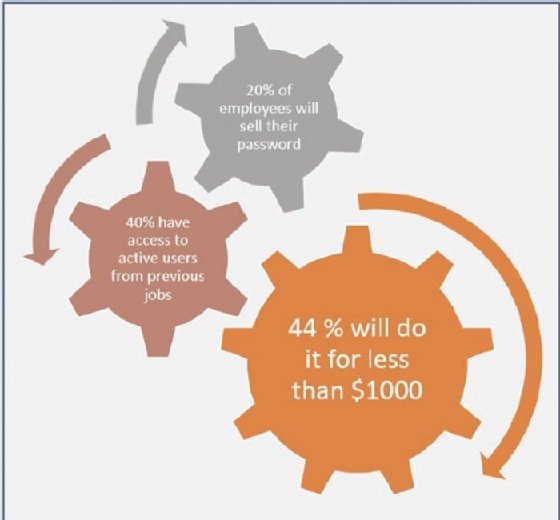
Now that you see that this is a serious threat, let's consider some actions that you can perform in order to reduce the probability and impact of risks associated with those malicious insiders.
Protecting your infrastructure against malicious insiders
Let's take a look at the tools, systems, and strategies that you can implement to protect against this threat.
The segregation of duties
This is one of the core activities that you must do as part of your defensive security strategy, and it is based on two main actions or activities:
- The first one is about the identification of the most critical tasks on your infrastructure. Here you need to ask yourself: what are the human actions that (if performed by a malicious insider) will cause a considerable impact on the systems and data?
- Second, once you identify those activities, you need to set controls to ensure that a single person cannot perform those tasks by themselves.
The importance of segregating duties
Researchers agree that the biggest hack to a social media platform (for example, the Twitter hack of 2020) could be prevented if a segregation of duties was put into place.
Now, let's take a look at some examples of how you can leverage and implement this strategy.
An example of the segregation of duties
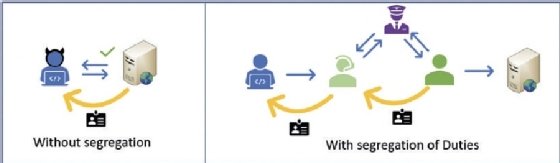
As you can see in Figure 4.2, allowing a system administrator to create privileged accounts allows a malicious insider the possibility to perform a dangerous attack. Instead, you must put some systems and processes in place to elaborate a flow for the creation of new users, which requires the involvement of several groups, reducing the probability of the attack.
In the following example, you can see a flow in which the system administrator will have to create a ticket with the request. The request is then sent for approval, and once it is approved, it will be sent to the Identity Management Access (IAM) team to fulfill the request.
Notice that filtering all the communications through the helpdesk (in both directions) is a great way to prevent direct communications between the malicious insider and the person in charge of creating the accounts, which greatly enhances the security of this method:
Another great example is related to backups because a malicious insider might know that deleting some files will not do any harm. This is because they can be retrieved from the backups, and in those cases, they will target the backups to prevent any restoration attempt.
To prevent this dangerous scenario, you can use the segregation of duties to ensure that a single user won't be able to delete those backups because a flow is in place to perform that action (supported by a policy, a process, and enforced by the system).
The use of mailboxes
When the segregation of duties is implemented, a malicious insider might try to persuade or convince another person to do some actions to help with the attack.
To avoid this, you can use mailboxes for the communication of highly sensitive teams, such as approvers, the helpdesk, the IAM team, and more. This will avoid exposing the identity of the people on those jobs, preventing any direct attempt to persuade or blackmail them:
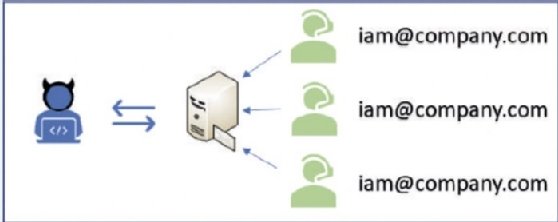
As you can see in Figure 4.5, even if there is a direct channel of communication with support teams (which is normal in small companies), malicious insiders won't be able to identify who is the person is working on the request.
Job rotation
Another good practice is job rotation for IT support personnel. This consists of the creation of a policy that requires IT personnel to switch roles from time to time. This requires the implementation of cross-training, mentoring, and skill-development programs, which is also motivational for IT personnel.
This simple policy gives you some extra advantages in your defensive security strategy, including the following:
- Reduces the risk of downtime: You must ensure that you have people trained to avoid risks due to a lack of skills regarding a given technology. For example, "Oh, we will have to wait until next week because Maria is out, and she is the only one who knows about DB2."
- Reduces the risk of fraud: When a person stays "fixed" in the same role, they might be able to cover their own tracks (in the case of any illegal activity). However, if you keep rotating them, there is a reasonable probability that the new person will discover some "anomalies" that could uncover that illegal activity.
- Decrease the impact of the attack: By reducing the time for which a person is doing the same role, it will also reduce the time a person will have to perform an illegal activity; therefore, the impact of such an attack (on your data and systems) will be lower.
Mandatory vacations
This is based on the same principle as job rotations, and it serves as a way to detect and stop frauds. The way this works is very simple: first, it is known that insiders who commit fraud tend to be paranoid of being discovered. Therefore, they avoid taking vacations to prevent someone from finding their malicious activity.
Additionally, it will be easy to identify deltas in the activities between a new admin and the previous admin (who is now on vacation) that might lead to the discovery of malicious activities:
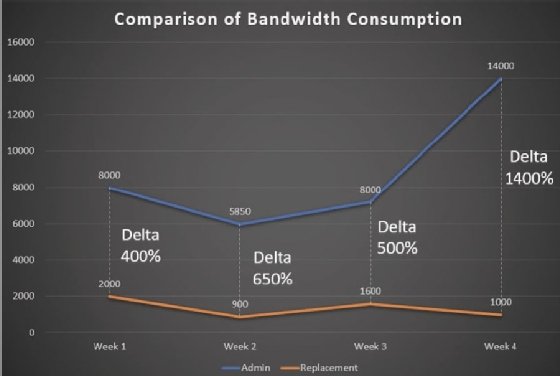
Figure 4.6 shows a scenario in which a privileged user used to download more than 4GB of data per week (which was considered to be normal) until the person was forced to take vacations and the use of bandwidth decreased by more than 400 percent, which confirmed that the user was engaging in unauthorized use of corporate bandwidth.
The analysis and correlation of logs
Unprocessed data might not trigger any alarms, but as demonstrated in the previous example, when it is properly correlated, it could show very interesting information.
Logs are a gold mine; however, you need to dig relatively deep to uncover useful information. One of the most basic ways to gather that information is by correlating data between users and systems to identify outliers.
Additionally, when doing the analysis, you need to determine which are the events that are higher or lower than the average and those are the ones that you should investigate further.
Also, there are many systems that automate the analysis of logs. So, instead of giving you some brands and names, I am going to show you the type of tools that will help you to achieve this, so you can search and find the solution that better suits your organization. Additionally, I would suggest you look for alternatives that leverage machine learning algorithms in order to improve detection and reduce false positives.
The systems are as follows:
- Behavior analytics systems
- Threat intelligence
- Anomaly detection
- Predictive alerts
However, I want you to know that not having those systems is not an excuse to waste your valuable data. In fact, I remember a very interesting scenario in which, by analyzing several logs, we found a system administrator that was illegally using corporate assets to "mine" bitcoins.
How did we find it?
By simply checking the logs, we discovered that several systems and non-production servers were normally turned on from 10 pm until 4 am with the sole purpose of mining bitcoins. Additionally, those logs contained the level of detail required to identify the users involved but also the evidence required to pursue the associated penalties and sanctions against them.
Alerts
Another great way to identify a malicious insider is by setting up monitors to give you alerts when a cybersecurity system is disabled by the user.
This is especially useful in those companies that give administrative rights to all the employees because they think they can bypass the security mechanisms (such as disabling the antivirus software or a firewall); however, what they don't know is that you are already one step ahead.
Important note
There are several ways in which to prevent a user from disabling some security features; however, not all companies or IT departments have the tools, knowledge, or interest in doing so, and that is why it is important for you to learn how to deal with these scenarios.
Now, let's take a look at one example of a very common practice in IT departments, which is a really bad practice for security.
Shared credentials
By default, the best practice says that shared credentials should NOT be allowed in your infrastructure. However, in case you do have them, you need to set up additional controls in place such as Multifactor Authentication (MFA), Role-Based Access Control (RBAC), and Privileged Access Management (PAM).
PAM works by locking shared credentials into a repository that can only be accessed by authenticated employee accounts (enabling accountability). Once the credential is used by the system administrator, the credential is reset for the next employee. Although PAM solves the challenge of shared accounts, it is very expensive to implement:
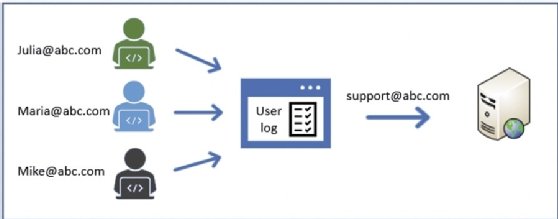
The preceding diagram is an example of a PAM system and shows how each user logs into a centralized system (to enable accountability), and then from there, inject the shared account into the server.
About the author
Cesar Bravo is a researcher and inventor who has more than 100 inventions related to cybersecurity that are being patented in the U.S., Germany, China and Japan. Those inventions include cybersecurity hardware, secure IoT systems and devices, and even cybersecurity systems for autonomous cars.
He loves to share knowledge, and he has been working with several universities to teach cybersecurity at all levels, from introductory courses for non-IT people up to a master's degree in cybersecurity for which he has also served as a thesis director.
In recent years, Bravo has become a recognized speaker, including delivering a TEDx talk and giving international presentations about cybersecurity and innovation in the U.K., Germany, Mexico, U.S. and Spain.






