
Getty Images/iStockphoto
Flashpoint: Threat vectors converging, increasing damage
The threat intelligence vendor warned that threat actors are increasingly combining known vulnerabilities, stolen credentials and exposed data to wreak maximum damage.
Cyberthreats are converging as attackers increasingly combine known vulnerabilities with stolen credentials and exposed data to compromise enterprises, according to new Flashpoint research.
The vendor's inaugural "State of Cyber Threat Intelligence 2023" report, released Thursday, examined threats and identified trends from 2022 to highlight upcoming security challenges enterprises might face. The data was derived from Flashpoint's threat intelligence team, which consists of more than 100 researchers, and its collections that use AI, machine learning and natural language processing models to search for relevant information.
The report's main takeaway -- and challenge for defenders -- is how threat vectors are converging, as well as the "cyclical" nature of attackers' tactics, techniques and procedures in the cybercriminal ecosystem.
"Organizations cannot afford to view, prepare for, mitigate, and prevent these threats in silos, as though one threat (and the cycle it exists in) is separate from another," Flashpoint wrote in the report.
One example is the way threat actors take advantage of CVEs, stolen credentials and exposed data. Flashpoint collections determined that 4,518 data breaches were reported last year, resulting in 22.62 billion exposed or stolen credentials and personal records.
Ian Gray, director of research and analysis at Flashpoint, told TechTarget Editorial that Flashpoint is seeing low-level attacks using stolen credentials obtained purely from off-the-shelf brute forcing and credential stuffing tactics. However, these simple methods can inflict significant damage.
The stolen credentials typically come from previously known breaches or compromises and can be leveraged until an account service gets burned or the credentials are reset. They can also be used as an extortion tactic against large companies.
"We've seen a number of threat actors use what I would call really low-sophistication attacks for high impact," Gray said. "A given set of credentials, which may cost a few dollars on a marketplace, can elicit thousands, hundreds of thousands or millions of dollars' worth of damage for an attack."
The report noted how exposed records such as financial information, emails and Social Security numbers were used to deploy phishing campaigns. Another threat vector that garnered significant attention from attackers was known vulnerabilities. There were 26,900 vulnerabilities reported last year, according to the report, and 55% were remotely exploitable.
"This brings the total number of known vulnerabilities to 306,000 -- with the Common Vulnerabilities and Exposures (CVE) and the National Vulnerability Database (NVD) failing to report 97,000," the report read.
Flashpoint researchers told TechTarget Editorial that there are vulnerabilities missing from the NVD because the way flaws are fundamentally collected is not conducive to broad coverage. While there are some approved cases in which companies can assign and use CVE IDs without Mitre oversight, most of the time Mitre relies on a model that requires researchers and companies to report and disclose to them.
"That leads to cases where coverage for some vendors is fairly comprehensive while also missing thousands of vulnerabilities every year disclosed via researcher blogs and vendors that are not part of their federation," the researchers said in a statement to TechTarget Editorial.
It's clear that attackers are leveraging and exploiting known vulnerabilities, and timely patching of those CVEs continues to be a problem -- of which threat actors are fully aware.
By monitoring communication channels and illicit markets, the Flashpoint intelligence team observed 766 instances in which threat actors referred to a vulnerability by its CVE. Overall, the data revealed 1.1 million threat actor mentions of CVEs.
Flashpoint provided a list of the top mentioned CVEs. Unsurprisingly, the Apache Log4j flaw, tracked as CVE-2021-44228, that caused prolonged challenges for vulnerable organizations was listed as the top flaw for January 2022. It was publicly disclosed in December 2021.
More recently, threat actors eyed the critical Fortinet authentication bypass vulnerability, tracked as CVE-2022-40684, that was publicly disclosed in October. The advisory revealed that the flaw was being actively exploited and affected multiple Fortinet services. Flashpoint listed it as the most mentioned CVE from October through December.
Because those vulnerabilities saw "the most active discussions and could result in remote code execution," Flashpoint recommended that enterprises prioritize patching any on that list.
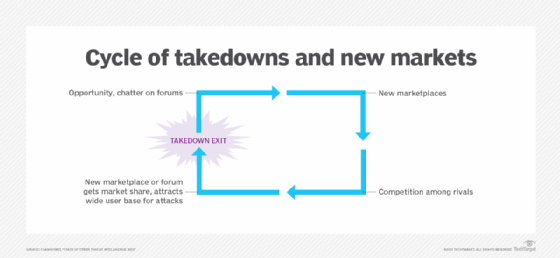
Illicit marketplaces fuel the cycle
The use of illicit dark web marketplaces plays a major role in attackers' ability to be successful, according to the report. Even if one gets shut down, such as German authorities did with Hydra Market last year, threat actors will regroup and open a new forum.
Flashpoint found that "adept threat actors and ransomware gangs increasingly share code, in addition to tactics, tools, and procedures -- largely thanks to the proliferation of illicit markets." One example the report highlighted was the Conti ransomware gang. Though the ransomware group disbanded in May, Flashpoint researchers observed overlaps associated with current gangs such as Royal.
The report referred to ransomware as a "scourge," noting a 7% increase from 2021, with 3,164 reported ransomware victims last year. Based on its collections so far this year, the threat intelligence vendor believes the number of reported ransomware victims in 2023 might exceed 2022's total.
"The proliferation of illegally obtained data gives threat actors ample opportunities to circumvent organizational security measures and controls -- empowering ransomware groups like LockBit to hold data for ransom, or sell or expose it on illicit markets," the report read. "The efforts of threat actors -- fed by human error, vulnerabilities, and the past victories of their malicious peers -- perpetuates an endless cycle."
Gray said it was important to analyze threats in terms of cycles to determine the best way to break them. Year over year, more instances of ransomware occur and more vulnerabilities are disclosed. While Gray said disclosures are good, he believes the steady increase in cyber attacks is primarily the result of unpatched vulnerabilities, which perpetuates the cycle.
Still, Gray emphasized that finding, disclosing and mitigating vulnerabilities are crucial to stemming the rise in threats. "We are putting more friction on threat actors by identifying these threats," he said. "Also, law enforcement takedowns and arrests of individuals does typically slow down or diminish that activity."
Earlier this week, a coordinated law enforcement effort resulted in police raids and arrest warrants for core members of the DoppelPaymer ransomware group. A press release issued by the German regional police referred to the suspects as "masterminds" of the ransomware gang, known for hitting hospitals and critical infrastructures.
Arielle Waldman is a Boston-based reporter covering enterprise security news.







