
Getty Images/iStockphoto
Microsoft issues first Secure Future Initiative report
In the first progress report since the launch of its Secure Future Initiative, Microsoft said it's made key improvements to identity and supply chain security.
Microsoft issued its first Secure Future Initiative progress report Monday, which touted an increased focus on identity and access management, software supply chain security, and threat detection efforts as nation-state attacks continue to evolve.
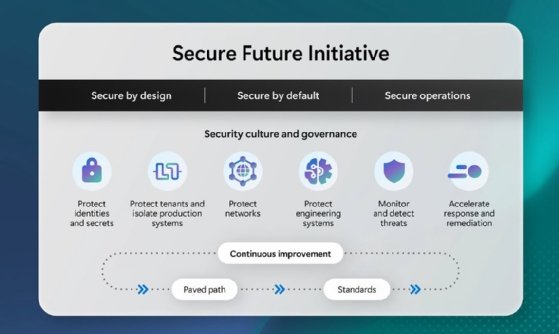
In a blog post accompanying the report on Monday, Charlie Bell, executive vice president of security at Microsoft, highlighted progress the company has made on the Secure Future Initiative, which launched in November. The SFI includes six pillars or areas of focus, with an emphasis on secure by design, secure by default and secure operations principles.
Microsoft developed the SFI after a China-based threat actor it tracks as Storm-0558 breached the company in 2023. While Microsoft initially said Storm-0558 stole a Microsoft account (MSA) consumer signing key that was accidentally included in a crash dump, the company later disclosed that there wasn't enough evidence to prove that theory; an investigation into the MSA key theft is ongoing.
In April, the U.S. Department of Homeland Security's Cyber Safety Review Board report took Microsoft to task over the attack, citing a "cascade of security failures" that let Storm-0558 actors breach email accounts at 22 customer organizations, including several federal agencies. One area of concern for the CSRB report was the lack of automated signing key rotation for the consumer MSA system.
The first pillar highlighted in the SFI progress report focused on changes to Microsoft's identity security, specifically for protecting signing keys. "We completed updates to Microsoft Entra ID and Microsoft Account (MSA) for our public and United States government clouds to generate, store, and automatically rotate access token signing keys using the Azure Managed Hardware Security Module (HSM) service," Bell wrote in the blog post.
Using token-stealing malware, Storm-0558 attackers compromised the account of an engineer who worked for a company Microsoft had acquired. Therefore, Microsoft made identity and access management (IAM) improvements that address token life spans and aim to remove traditional passwords for employees.
For example, the report said the company's standard identity SDKs, which provide consistent validation of tokens, now cover more than 73% of tokens issued by Entra ID for Microsoft applications. Another IAM improvement includes video-based user verification for 95% of Microsoft internal productivity environment users to help verify identity, including remote employees. Microsoft is also enforcing phishing-resistant user credentials in its used environments.
Additionally, Microsoft said it has enabled its auditing tool Purview with new features to help protect "passwords, secrets, and keys that would enable an attacker to extract and reuse that information in future attacks."
More SFI pillars
The second SFI pillar focused on protecting cloud tenants and isolating production systems. "We completed a full iteration of app lifecycle management for all of our production and productivity tenants, eliminating 730,000 unused apps," Bell wrote. "We eliminated 5.75 million inactive tenants, drastically reducing the potential cyberattack surface."
The third pillar addressed network security. The report noted that more than 99% of physical assets on Microsoft's production network have been recorded in a central inventory system, and each asset is monitored for credential, firmware and access control list hygiene.
The report's fourth pillar also addressed supply risks and noted that 85% of Microsoft's production build pipelines for commercial cloud services are now using centrally governed pipeline templates. Microsoft stressed that its engineering systems are a prime target threat actors use to gain access to customer environments. "In recent attacks, we've seen threat actors exploit the software supply-chain through both code exploits and social engineering. We then see them attempt to exfiltrate source code to find secrets and vulnerabilities in source to be used immediately or stored to leverage at a later date," the report said.
The fifth pillar focused on monitoring and detecting threats. To that end, Bell said Microsoft has made "significant progress" toward making sure all Microsoft production assets and services are emitting standardized security logs. "For instance, we have established central management and a two-year retention period for identity infrastructure security audit logs, encompassing all security audit events throughout the lifecycle of current signing keys," he wrote. "Similarly, more than 99% of network devices are now enabled with centralized security log collection and retention."
In the sixth and final pillar, Microsoft outlined efforts to improve vulnerability response and remediation processes, which have been heavily criticized by cybersecurity vendors in recent years. "We began publishing critical cloud vulnerabilities as common vulnerability and exposures (CVEs), even if no customer action is required, to improve transparency," the report said. "We established the Customer Security Management Office (CSMO) to improve public messaging and customer engagement for security incidents."
On Monday, Microsoft also announced that it established a new Cybersecurity Governance Council with appointed deputy CISOs to assume major responsibilities. "As a group, they take responsibility for the company's overall cyber risk, defense, and compliance," Microsoft wrote in the report.
Lessons learned from Storm-0558 attack
Many of the changes outlined in the SFI report appear to be in response to the Storm-0558 attack and the resulting CSRB report, which noted that Microsoft's security culture was "inadequate and requires an overhaul."
Joy Chik, president of identity and network access at Microsoft, told TechTarget Editorial that the company took the CSRB's recommendations seriously and made significant progress in IAM.
"We do not want to have a repeat Storm-0558 attack, but on the other hand, we also recognize the threat landscape and the sophistication will continue to evolve. So we need to continue to use all the AIs and threat signals to continue and improve, and strengthen our protection, but also detection for these attack vectors," she said.
Chik said transitioning the MSA and Entra ID to the same token system enables the company to instantaneously apply security hardening to both the commercial and consumer side. As to why the changes weren't implemented sooner, she said Microsoft prioritized the commercial cloud side of operations, but realized that the same level of security was needed on the consumer side. Chik stressed that the updates to MSA and Entra ID help Microsoft raise the bar for both at the same time.
Chik also outlined how the IAM improvements would help prevent a repeat of the Storm-0558 attack. She said the attack highlighted how having multiple software layers of protection is not enough to prevent nation-state attacks, and that a security posture is better when there's zero human touch. Microsoft continues to focus on a zero-trust access approach to security, she said.
"I think this goes back to the zero-trust principles, the least amount of privilege. Basically, you should only give the amount of access you need with the least amount of privilege and with the least amount of time," Chik said. "Zero trust helps reduce legacy access tokens that are lying around that you don't really need anymore."
A key theme in the SFI progress report was enhancing IAM, particularly for Microsoft's engineering systems. Chik highlighted how the company reduced personal access token life span to seven days and disabled SSH access for all Microsoft internal engineering repositories.
She said the practice of reducing the token life spans was not implemented sooner because it's often difficult to find a balance between security and productivity. "You can always look back and say we could have implemented everything from the beginning," she said. "I think part of it goes back to the SFI, the principle of secure by design, secure by default and secure operations."
Arielle Waldman is a news writer for TechTarget Editorial covering enterprise security.







