Security teams need to prioritize DSPM, review use cases
New research showed data resilience is a top priority for security teams, as data security posture management grows to help manage and protect data and improve GenAI.
Enterprise security teams need to focus on cyber resilience to protect against ransomware and other threats, and a significant part of cyber resilience is data resilience. Data resilience refers to the capacity of data infrastructure to anticipate, withstand and recover from disruptions, ensuring continuous data availability and integrity. If something slips through the protection and detection layers, data infrastructure needs to persevere.
CISOs and security teams can undertake a limited number of projects during a fiscal year. And with a long list of possible projects, the reality is that they can only slot in three to five projects a year due to budget and bandwidth constraints.
Recent research from TechTarget's Enterprise Strategy Group showed data resilience is a top priority for nearly nine out of 10 survey respondents and is the top priority for 36% of respondents.
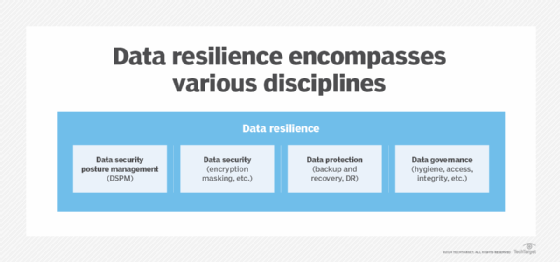
Data resilience is at the intersection of data security posture management (DSPM), data security, data protection and data governance. DSPM enables organizations to locate and categorize their sensitive data stores so they can protect, secure and govern the data.
Let's discuss why organizations need to prioritize DSPM to make a measurable impact on their security programs. I'll also describe where to start and the top use cases that can help drive success.
The need for DSPM
With ransomware incidents making headlines and operations at affected businesses grinding to a halt, security leaders recognize that while protection and detection are essential, threats can slip through. The ability for data infrastructure to withstand and recover -- also known as data resilience -- is essential, and they are prioritizing those projects.
A key element of data resilience is understanding where sensitive data stores are located and what is inside them. You can't secure something you don't know about, and DSPM helps identify and categorize data stores. It comprises technology and processes that continuously monitor and assess an organization's data security controls across all environments. DSPM discovers and categorizes data stores to identify weaknesses, prioritize risks and ensure data remains protected from evolving threats.
Two DSPM use cases
Data discovery is a means to an end. Organizations want to achieve something that discovering their sensitive data enables, which means they have a DSPM use case.
While there are six major DSPM use cases, two bubbled to the top when we asked enterprises what they wanted to achieve with DSPM:
- Data breach prevention. Data breach prevention is the most prevalent use case. Security teams need to know where their sensitive data is located, what is inside and the posture of that data so they can proactively avoid a potential breach. Actions can run the gamut from hardening data stores through encryption and masking to removing stale access to the data store.
- Facilitating generative AI technology deployment. Generative AI (GenAI) depends on data to inform the model, but organizations need to categorize the data to minimize the chance of data leakage. GenAI projects require locating and categorizing data so the model is properly informed and sensitive data doesn't inadvertently and inappropriately leak in response to an unprivileged worker's large language model prompt.
Figuring out what your organization wants to achieve -- use cases -- and how to improve your tooling and internal processes provide a path to tangible success. The DSPM market continues to grow with innovative startups, such as Bedrock Security, Concentric AI, Cyera, Normalyze and Sentra; ongoing acquisition activity, including Rubrik buying Laminar, CrowdStrike buying Flow Security, IBM buying Polar, and Tenable buying Eureka Security, to name a few; and organic expansion, such as Forcepoint, Varonis and Zscaler.
DSPM can solve a number of problems. Understanding where your organization wants to start is the first step down a path to success.
Todd Thiemann is a senior analyst covering identity access management and data security for TechTarget's Enterprise Strategy Group. He has more than 20 years of experience in cybersecurity marketing and strategy.
Enterprise Strategy Group is a division of TechTarget. Its analysts have business relationships with technology vendors.







