What is data in use?
Data in use is data that is currently being updated, processed, erased, accessed or read by a system, application, user or device. This type of data is not being passively stored, but is instead actively moving through parts of an IT infrastructure.
Examples of data in use
In general, data in use includes any data that is being processed, accessed or read. Examples include data that is stored in or processed by the following:
As an example, when a user requests access to their transaction history or makes a transaction on a banking website or application, the transaction data is considered data in use. Similarly, authorizing user logon input is an example of data in use.
Data that is retrieved from a database at an application's request is also data in use. The application uses this data in specific ways to allow users to meet defined objectives.
The data in cloud storage files is also considered data in use. It is commonplace for multiple users to access a document stored in Google Cloud or Microsoft Office 365. When they simultaneously make changes to the document, its data is considered to be in use.
Data might be actively queried from one or more sources by a data analytics application. It can also be processed and analyzed by that application in real-time to provide useful insights to a user. This data is also data in use and the insights generated from it can support user decision-making.
Three states of data
Data in use is one of three states of digital data -- the other two states are data in motion and data at rest.
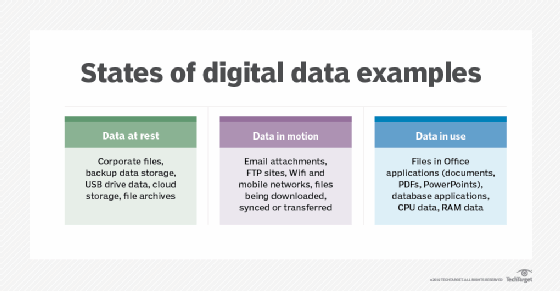
Data in motion refers to data that is being transported within a computer system or between computer systems (including virtual machines or devices on a virtual private network). It is also known as data in transit or data in flight.
Data at rest is data that is not currently being accessed or used. It has already reached a destination and is therefore no longer moving across a network. Files that are rarely or never changed, such as archival or reference files, as well as files that are regularly but not constantly changed, are all examples of data at rest.
In contrast to the abovementioned two types of data, data in use is data that is being actively used. It is not at rest and it might not be in motion.
Data states are used by information security professionals to identify endpoints where data should be encrypted. Knowing data states is also important to maintain compliance with regulatory guidelines, such as the Payment Card Industry Data Security Standard (PCI DSS) and the General Data Protection Regulation (GDPR).
Threats to data in use
Because data in use is directly accessible by one or more users, data in this state is vulnerable to attacks and exploits. Additionally, security risks become greater as permissions and devices in an IT network increase. Often, data in use might contain digital certificates, encryption keys and intellectual property. Businesses must monitor and secure these types of data to prevent falling victim to cyberattacks.
Man-in-the-middle (MitM) attacks are a common threat to data in use. This is a type of eavesdropping attack in which an adversary secretly intercepts the data and may manipulate it for malicious purposes.
Some of the other common threats to data in use include:
- Malware and ransomware. Malicious software in the form of malware and ransomware. can allow bad actors to steal or delete data in use, or encrypt it to make it unavailable to authorized users.
- Phishing scams. Phishing is when a scammer attempts to obtain sensitive data in use, such as passwords or credit card details, using fraudulent emails and posing as a trustworthy sender.
- Insider threats. Unscrupulous or careless insiders (current or former employees, contractors, vendors, business partners) who maliciously or inadvertently misuse their privileges, leading to data breaches.
- SQL injections. SQL injections are a cyberattack technique in which attackers insert a string of malicious code into a database query to gain unauthorized access to the data in use within the database.
- Memory scraping (RAM scraping). A cyberattack technique in which attackers try to read memory registers to extract sensitive data, such as encryption keys or credit card information.
- Data leaks. Weak or missing access controls or elevated privileges might allow users to engage in activities -- text copy-paste, screen captures, emailing multiple users -- that result in unintended data exposure or leaks.
The importance of encryption data in use
In order to safeguard data in use from cyberattacks, it is critical to implement strong security controls such as encryption. Encryption methods like asymmetric encryption, HTTPS, Transport Layer Security and Secure Sockets Layer are commonly used. In addition to encryption, some important ways that data in use is protected include user authentication at all stages, strong identity management and well-maintained permissions for profiles within an organization.
Encryption can be applied at the drive level or memory level. Full disk encryption, or FDE, involves encrypting all the data on a drive and its operating system to prevent unauthorized data access and to ensure that it remains inaccessible even if the device is stolen. In contrast, memory encryption involves encrypting only the contents of the system RAM to ensure that only an authorized user with the decryption key can read the contents of the RAM.
Other security strategies to protect data in use
Some of the other common practices for protecting data in use include:
- Tracking and reporting data access to detect suspicious activity and potential threats; for example, monitoring login attempts to platforms with sensitive information.
- File integrity monitoring, or FIM, tools that monitor and track file changes in real time to enable security teams to detect unauthorized alterations or deletions.
- Strict access control and endpoint security management with authentication measures in place before data can be accessed and used.
- Well-documented disaster recovery plans that can accelerate the recovery process if data in use is compromised or lost.
- Email monitoring tools that track and analyze email content, attachments and metadata to protect data in use from security threats (both intentional and inadvertent).
- Data loss prevention tools that mitigate threats to critical data in use by placing the data behind a network firewall.
- Nondisclosure agreements, also known as NDAs, for employees and stakeholders that specify the punitive measures that will be imposed on those parties if they share the information without the organization's express permission.
Privileged access management, or PAM, is another way to safeguard data in use from theft and leaks. By using techniques for shared access password management, privileged session management and application access management, security teams can monitor which users have access to what data and also prevent malicious parties from accessing sensitive in-use data.
As data environments expand in step with the growing threat landscape, organizations can also benefit from implementing strong user authentication and authorization controls for protecting data in use. For example, multifactor authentication (MFA) mandates the use of multiple authentication processes to gain access to a business system or account. MFA makes it harder for hackers to access that system, even if they manage to steal one of the factors -- such as a user's login credentials (user name and password).
It is also advisable to adopt data security posture management (DSPM) technologies and tools. These tools provide a holistic view of all data in use, particularly sensitive data, as well as its security posture. The DSPM approach also enables organizations to do the following:
- Identify vulnerabilities in data in use.
- Implement controls to prevent data breaches.
- Identify instances and causes of data misuse or exfiltration.
- Discern if any data in use was accessed without proper authorization.
Finally, it's crucial to monitor user permissions and privileges regularly. Doing so can raise red flags like excessive permissions or elevated privileges, which, left unaddressed, might lead to the exposure or compromise of business-critical data in use. Security permission analyzers can be useful in these areas. In addition, information rights management can help to control and secure data in use from unwanted or unauthorized access.
With rising cyberthreats, here are tips to protect and secure your data at rest, in use, and in motion.