full-disk encryption (FDE)
What is full-disk encryption (FDE)?
Full-disk encryption (FDE) is a security method for protecting sensitive data at the hardware level by encrypting all data on a disk drive. FDE automatically encrypts data and operating systems (OSes) to prevent unauthorized access.
Disk-level encryption safeguards data from getting into the wrong hands and is important for organizations that are following data security compliance regulations such as the Health Insurance Portability and Accountability Act or the General Data Protection Regulation.
FDE is especially useful for desktops, laptops and mobile devices that can be physically lost or stolen. Even if the device is stolen, the encrypted data will be inaccessible to the thief. Because one key is used to encrypt the entire hard drive, FDE requires network administrators to enforce a strong password policy and provide an encryption key backup process in case employees forget their password or leave the company unexpectedly.
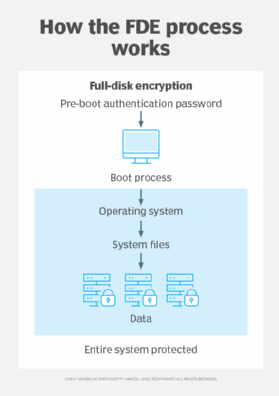
FDE works by automatically converting data on a hard drive into a format that can't be understood by anyone who doesn't have the key to undo the conversion. Specifically, the hard drive is converted from a readable plaintext to a ciphertext that isn't readable unless it's converted back to plaintext with a key. Without the proper authentication key, even if the hard drive is removed and placed in another machine, the data remains inaccessible. The encryption process is performed using encryption software or hardware that's installed on the drive. Some systems don't encrypt the master boot record -- the code that starts the OS loading sequence -- meaning that not everything on those devices is encrypted.
FDE is often installed on computing devices at the time of manufacturing. For example, FDE is enabled through features like BitLocker, which is included in certain Microsoft Windows versions, or FileVault, which is built into the macOS. BitLocker and FileVault enable users to recover lost passwords. BitLocker stores recovery information on Active Directory, and FileVault backs up encryption keys to Apple iCloud. Microsoft also offers Device Encryption on all Windows devices that protects data by encrypting the drive.
Benefits of full-disk encryption
Full-disk encryption offers the following advantages:
- It requires no special attention from end users after they initially unlock their computer. When data is written, it's automatically encrypted, and when it's read, it's automatically decrypted.
- Data can't be extracted without a device password and encryption key.
- It helps protect data at rest against cyber attacks and data leaks.
- Temporary files are also encrypted.
- Users are authorized before the device boots.
- FDE is faster than manual encryption methods, which are more time-consuming and less efficient.
Drawbacks of full-disk encryption
Some disadvantages of FDE, however, include the following:
- The encryption and decryption process can slow down data access times, particularly when virtual memory is being heavily accessed.
- If users forget their password and lose their recovery key, the device will be inaccessible to them, and they will be locked out just like an intruder.
- Data in transit isn't protected, so data shared between devices and through email is still vulnerable to hacking.
- The costs involved with FDE include the encryption hardware or software, as well as the time it takes to operate a computer with FDE.
Learn more about centralized encryption methods in IT environments and how they're critical to preventing data theft.
