Top 10 UEBA enterprise use cases
The top user and entity behavior analytics use cases fall in cybersecurity, network and data center operations, management and business operations. Check out the risks.
User and entity behavior analytics uncovers hidden risks to the enterprise. UEBA uses advanced data analysis techniques to sift through streams of data from multiple sources looking for evidence of attacks, reconnaissance and data exfiltration. In this case, behavior analytics means the actions of both people and systems, or entities. Examples include if a user suddenly does large data downloads, a system suddenly attempts to connect to another system it doesn't usually communicate with or anything else occurs out of the ordinary.
UEBA has multiple use cases in the following main areas:
- cybersecurity
- network and data center operations
- management
- business operations
Cybersecurity UEBA use cases
UEBA looks for evidence of a variety of types of threats or compromise by sifting through logs, configuration files and other data sources. It is key to the following use cases.
1. Detect lateral attacks
Network logs can show evidence of a system trying to contact other systems it doesn't usually talk to, possibly indicating it is compromised and being used as a launching pad for lateral attacks against other systems.
2. Identify compromised accounts
System and network logs can show that people, or accounts, are trying to do things they don't usually and shouldn't do. These can be an indication that the account's credentials have been compromised and a third party is using the account to map out capabilities and vulnerabilities or to exfiltrate sensitive data.
This article is part of
What is data security? The ultimate guide
3. Find insider threats
Behavioral analysis can spot an account making use of higher levels of privilege than usual or trying to reach systems it doesn't usually interact with. These are potential evidence of an insider abusing its account's capabilities.
4. Detect Trojan account creation
Analysis can spot unusual bursts of account creation, deletion or modification activity, such as a slew of system admin accounts being created or existing ones losing some specific access privileges. This behavior may indicate a bad actor is setting up local accounts from which to carry out further operations.
5. Monitor for account sharing policy breaches
UEBA systems can spot evidence that users have shared credentials instead of operating only within their own accounts, making compromise by bad actors more likely.
Prospective vs. retrospective UEBA
UEBA can be used prospectively or retrospectively in cybersecurity. Prospectively, cybersecurity teams or service providers use it to detect attacks as they occur, with the goal of triggering a response, preferably automated.
Retrospectively, cybersecurity teams, service providers and law enforcement use UEBA to review logs and other data as part of their forensic investigation of an attack that has already happened. UEBA can spot precursors to the attack and tease out the various threads of activity that constitute the attack. This information can be used to remediate the effects of the attack and sharpen and strengthen defenses and can then be shared on threat information feeds.
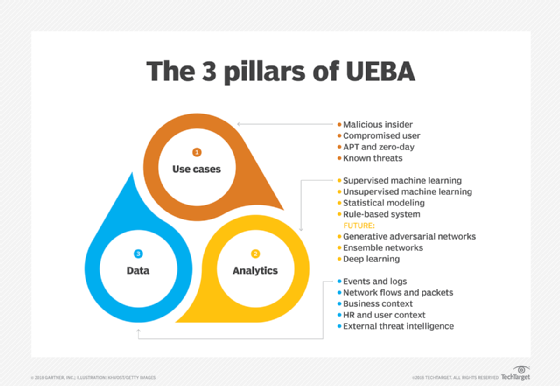
Operations use cases
The same features that make UEBA a powerful cybersecurity tool -- teasing meaningful information out of scattered streams of usage and performance data -- make UEBA software useful to systems operations teams.
The primary operations use cases include the following.
6. Predict impending failures in hardware and software
Anomalous behaviors can indicate current or impending malfunction in hardware; OSes; middleware, such as database management systems; application servers; and applications. A growing number of data transmission errors on a given network switch port, for example, might indicate the hardware is failing or there is a problem with the cabling to that port.
7. Perform root cause analysis
A single problem can sometimes produce effects across multiple systems and tiers of functions. Threat analytics are needed to spot the connections. For example, scattered transaction failures across several staff- and customer-facing applications and intermittent problems with a database server and application containers running in a specific Kubernetes cluster might stem from a problem with the storage network underlying them all.
UEBA can serve the operational needs of enterprises and cloud service providers, which can use them both prospectively or retrospectively. They can use UEBA tools to help identify the root cause of scattered problems that aren't obviously connected as they occur or use them after a failure to see if there were indicators of the problem that could have been spotted sooner -- and will be should they recur.
Other behavior analytics use cases
Outside of IT proper, an enterprise could use a behavior analytics tool to track and understand staff and customer behaviors for management and commercial purposes. These are not the same products used in operations or security, but they use the same techniques and fall under the rubric of behavioral analysis. Organizations should always undertake such usage within a framework of adherence to applicable law, corporate privacy protection policies and good employee management ethics, if analyzing employee behaviors.
Although rife with the potential for misuse, these tools can provide powerful insights.
Other UEBA use cases include the following.
8. Understand productivity
Behaviors can provide clues to both individual and team productivity, indicating what makes some people or teams more productive than others in a given context.
9. Understand actual team structures
Behavioral analysis can also uncover patterns of communication among staff, which can yield useful insight into which employees are seen by other employees as leaders, helpers or mentors.
10. Detect fraudulent transactions
Banks and other financial services institutions, as well as service providers, such as phone companies, have long used such technologies in fraud detection. These systems were some of the earliest applications of the analysis techniques UEBA tools use. In these contexts, tools focus on anomalous behaviors, such as the following:
- unusual uses of ATM cards or online banking;
- unexpected patterns of charges on credit cards;
- odd patterns in insurance claims;
- long-distance toll fraud; and
- robocalling.
By focusing on what people and systems do, UEBA tools uncover useful information in a growing variety of use cases. The rapid evolution of AI and machine learning will only broaden and deepen the set of tools available and their ability to tease meaning out of data scattered across time, geography and systems.







