
Alex - stock.adobe.com
8 best practices for a zero-trust storage strategy
Explore how to apply the zero-trust security model to storage systems. Given today's threat landscape, additional data protection is key for enterprises.
Organizations face an increasing number of challenges as they try to protect their data and storage systems. A zero-trust storage strategy, though, takes a "trust no one" approach to security that recognizes the fluid nature of today's data boundaries.
No longer confined to private networks, sensitive data might reside in multiple locations, as does an increasingly distributed workforce. IT teams also face a growing number of regulations that govern how they have to store and protect data, further complicating data management. Traditional approaches to cybersecurity can no longer meet many of today's data protection needs.
In the zero-trust model, sensitive resources are off limits to all users and devices until they have been properly verified. Although this approach can help better protect data, implementing a zero-trust storage strategy takes a significant effort. The better prepared an IT team is for such an undertaking, the more likely it will be to deploy an effective system that protects data wherever it lives.
What does a zero-trust storage strategy entail?
Traditional approaches to protecting resources have been based on building a strong perimeter around IT infrastructure. The perimeter-based model uses firewalls and other technologies to create a castle-and-moat structure that extends trust to all users and devices within that perimeter and excludes everything else. Although perimeter-based security worked well in the past, the continued proliferation of cloud-based services, remote workers, BYOD programs, edge computing and IoT devices has opened up sensitive data to a new set of risks. Securing the perimeter is no longer enough to meet the rising tide of today's sophisticated cyberthreats.
Zero-trust security restricts and controls access to data, storage systems and other resources. The zero-trust model assumes no users, devices, services or other systems can be trusted until they are fully authorized and authenticated when they first connect to the network and then get reverified at multiple points. The model always maintains strict access controls to all resources, using tools such as microsegmentation, system monitoring, identity and access management (IAM), and comprehensive security policies that define granular controls over storage, data and other resources.
The zero-trust approach has been gaining steady momentum in recent years because of increasing data threats. In 2018, Forrester introduced the Zero Trust eXtended Ecosystem and its seven core pillars for an effective zero-trust platform. The same year, the National Institute of Standards and Technology offered extensive guidelines for implementing the core components of a zero-trust platform. More recently, U.S. federal government agencies have taken steps to implement zero-trust security at a national level.
A zero-trust platform controls access to all of an organization's data, whether at rest or in motion. The platform also protects the communications and data associated with maintaining those systems. Any single point in a network can represent a potential vulnerability. A compromise can affect that point, as well as other network resources, including the storage systems and their data. For this reason, a zero-trust initiative must be a network-wide effort that incorporates storage along with all other resources.
Best practices to implement zero-trust storage
IT teams must proceed carefully with zero-trust storage strategy efforts. Here are eight best practices to keep in mind for implementation.
1. Map out where sensitive data currently resides and how it flows
Identify the entire protect surface -- the key data and systems that need safeguards against attack -- and the entry points to those systems. The information should also include the communication channels between administrators, applications and devices.
Catalog all data, including where it's located and how it's stored. Finish with a comprehensive map of where everything resides and how it all connects.
2. Assess current storage and data security
Determine the storage protections in place and how the organization applies security to each component. Identify various attack surfaces and top vulnerabilities. Do a little clean-up -- such as removing old or unused accounts -- and address immediate threats until the zero-trust platform is fully operational.
As part of the assessment, determine which users or accounts are currently authorized to access resources and their level of access. Identify the endpoints where they're connecting to resources, when they're accessing those resources and how often. Carefully document all findings for quick reference and to understand access patterns.
3. Verify and identify all storage-related devices and services
IT teams should know the type of storage hardware, type of storage, type and version of software and firmware, as well as details about the storage network.
IT teams should be able to verify all devices connecting to their networks. No system should be able to access network resources without proper identification that can authenticate, authorize and validate them. The teams should attach a strong identity to each device and make sure it has only one -- not multiple -- identities. They should also ensure that each device meets their organizations' specific security requirements.
4. Plan and implement network segmentation
One of the most useful tools for securing a network is microsegmentation, which divides the network into logical components that control access to data and resources. Microsegmentation reduces the immediate attack surface and prevents lateral movement through the network, which helps contain any data breaches. Admins often use microsegmentation with next-generation firewalls that include advanced features such as intrusion prevention and deep-packet inspection.
Even with microsegmentation, IT teams should adopt a zero-trust policy that treats every channel as a potential threat until proven otherwise. They should never assume implicit trust between two entities on the same network or within physical proximity of each other. In addition, they should secure all communications between resources to prevent eavesdropping and ensure the integrity of those communications. IT teams can also use software-defined perimeters that control access to resources by forming virtual boundaries around them.
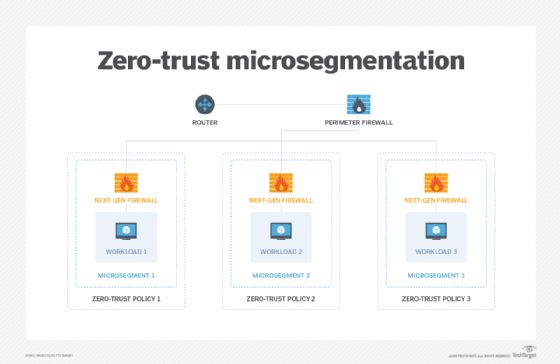
5. Develop and implement granular zero-trust policies
At the heart of a zero-trust storage strategy is a set of policies that grants users access to specific resources, while prohibiting all other access. Zero-trust security policies should apply to everyone, regardless of their position in the organization or whether they're considered owners of a resource. Users shouldn't be able to access any resources other than those admins have explicitly granted them.
Base permissions on principles of least privilege, with access limited to only what's necessary and only for as long as needed. Admins should revoke access immediately after a session ends. To enforce these policies, develop a framework for managing them and applying them at each entry point. Framework components should communicate over a separate control plane that facilitates secure communications.
6. Monitor and audit storage systems and the network
Monitoring and auditing strategies should be able to track storage resources, whether on premises, in the cloud or in other environments. Evaluate devices and services individually, correlate how they interact and look at specifics such as the data users access or the actions they carry out.
IT teams should set up alerts, so they are immediately notified of any suspicious activity. They should maintain activity logs and continuously analyze the collected information to determine what is working, what needs to be improved, where security holes might exist and whether there is any anomalous behavior. Teams should automate monitoring and auditing operations, particularly when it comes to responding to threats in real time. The teams should also conduct penetration testing and stay current on threat intelligence.
7. Don't trust the local network
On the local network, deploy basic security measures that reinforce the larger zero-trust effort and that provide additional protections to storage and data. For example, encrypt all data at rest and in motion.
IT should use tools such as multifactor authentication (MFA), single sign-on and IAM to further enhance security. A zero-trust storage strategy should include a backup and recovery platform that incorporates the same safeguards as the other resources. At least one copy of the backup data should be immutable and air-gapped to prevent possible tampering. Organizations should also consider other steps to prevent data loss, such as application allowlisting and physically protecting devices from potential threats.
8. Don't forget about your users
End users play a critical role in the success or failure of an effective zero-trust storage strategy. IT teams should explain why they will implement the strategy and its potential impact. Not only does this better prepare them for the inevitable change, but it also provides an opportunity to educate them about potential security risks and how they can help protect data.
The end user's experience accessing data, storage systems and other network resources is key. If users face numerous MFA steps whenever they try to perform a task, they will become increasingly frustrated and perhaps reach a point where they barely look at prompts or notifications. The user's interaction with the secure systems should be as streamlined and straightforward as possible, without making their jobs more difficult.








