kras99 - stock.adobe.com
Ctera's Ransom Protect update helps guard file system
A new update to Ctera's file gateway offering adds ransomware protection into the file system itself, protecting data with AI-powered detection and alerts.
The latest update to Ctera's global file system wants to keep the ransomware barbarians at the enterprise gates -- far away from data and backup systems.
The new Ctera Ransom Protect update will add new security features to customer file systems, including behavioral anomaly detection, recovery with snapshots, and a management dashboard for alters and incidents.
New Ransom Protect capabilities will be free and generally available through an update in July, according to Ctera executives. The vendor sells file gateway technologies that cache enterprise-critical data on premises for faster access and tier colder data to cheaper object storage in public and private clouds.
As ransomware prevention continues to dominate the IT buying conversation, file systems should attempt to prevent attacks and system takeovers, which might affect backups, according to Ray Lucchesi, founder and president of Silverton Consulting.
"Backups are after the fact," Lucchesi said. "By that time, it's too late. You could still recover, but your system is toast. Hopefully, [Ctera's offering] could detect it or flag it before it has a massive effect on your data."
Adding more monitoring and messaging systems can lead to alert fatigue for security and storage administrators or affect system performance, but IT buyers are looking for every possible layer of defense against ransomware that they can get, he said.
"It takes processing power to [run security processes]," Lucchesi said. "High-performance systems can't do this sort of thing because it takes too much time. Doing this sort of thing can add overhead."
Holding the line
New Ransom Protect capabilities will be added into the Ctera Portal, the vendor's data management system that oversees employee devices or filer appliances at remote data centers.
Behavioral anomalies among users or files are spotted using machine learning, which expands detection beyond scanning for specific ransomware signatures. Examples of anomalies include significant changes to a set of files within a short amount of time or a user initiating changes to files in a way that is out of character.
A new Ransom Protect dashboard within the Ctera console adds monitoring capabilities, incident logging and a list of blocked users. Recovery services include rollback to snapshots pulled from immutable and air-gapped cloud storage.
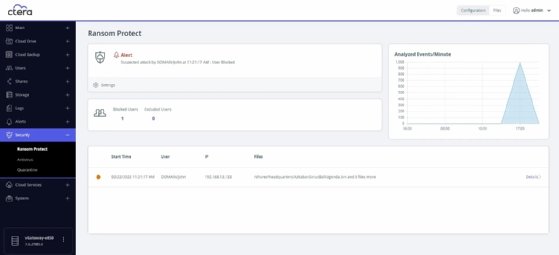
The new capabilities help harden the Ctera file system, which is used for primary storage, against ransomware attacks, separate from a user's existing backup or security software, according to Oded Nagel, CEO at Ctera.
The vendor has provided recovery services for customers including immutable snapshots, but customer interest and the increasing devastation of cyber attacks had the vendor consider new ways of protecting its platform and expediting recoveries.
"We're doing [recoveries] on a weekly basis," Nagel said. "We help our customers recover, but if you have a global file system with 1 billion files, it'll take a while."
Future updates for Ransom Protect will include additional ransomware attack prevention as well as greater connections to security services through APIs.
Another brick in the wall, reprise
Security-centric additions to file systems can help protect data, but recovery strictly through snapshots leaves open the possibility of corrupted data, said Dave Raffo, an analyst at Futurum Group.
"You want to know the data you recover isn't also infected," Raffo said. "This security is a must-have. Everybody needs it, and they better get it right."
Backup and disaster recovery companies such as Cohesity and Rubrik have made cyber attack prevention a critical part of their portfolio in the last few years, Raffo said. The shift in focus has provided greater market visibility, so it was only a matter of time before the storage services themselves would attempt a pivot, he added.
"It's worked pretty well for them, [and] you'll see a lot of other [vendors] go down that route," Raffo said. "Security itself isn't the product, but the security features are what get most of the attention."
Despite the possible effects on performance for the most demanding of customers, Lucchesi said the addition of security to a customer's file system should be considered a net positive, just like adding greater protection to any part of the technology stack.
"You have to have fences on top of fences," he said. "I don't think any one solution could stand on its own."
Tim McCarthy is a journalist from the Merrimack Valley of Massachusetts. He covers cloud and data storage news.