How are UEM, EMM and MDM different from one another?
IT should understand the differences between UEM, EMM and MDM tools so they can choose the right option for their users. Learn about the differences between these tools.
Over the years, endpoint management vendors have built more and more functions into their tools.
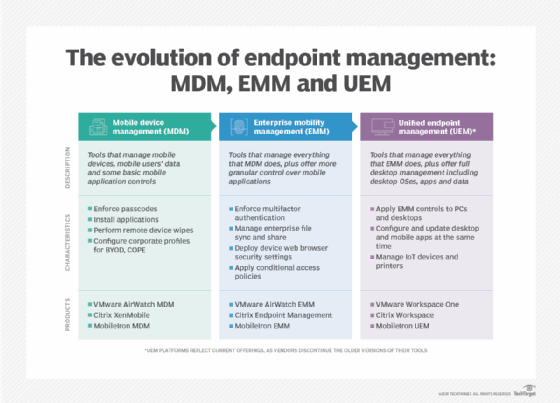
Mobile device management (MDM) products were among the earliest endpoint management tools. Then, enterprise mobility management (EMM) tools entered the market. Now, unified endpoint management (UEM) tools are often the preferred way to manage devices.
Vendors are the driving forces behind each change, and each product category provides a more granular level of control than its predecessor. This evolution has been part of a clear plan to offer more inclusive management as an all-in-one tool for endpoints, but how do MDM, EMM and UEM compare?
What is MDM, and what are MDM tools used for?
Mobile device management tools enable IT teams to manage mobile devices and provide controls, such as configuring email and applying security controls to mobile devices.
Early on, IT professionals struggled with managing and securing mobile devices. At the time, one of the major problems was that most users were working from domain-joined PCs with settings controlled by group policy settings. However, these group policy settings could only be applied to domain-joined Windows devices and couldn't secure the mobile devices entering the corporate environments.
Another problem that IT pros had to cope with was that network-level security controls could not protect mobile devices except when connected to an organization's Wi-Fi network. More importantly, the device management tools of the time required managed devices to connect to an organization's network.
MDM tools solved these and other problems. Such tools let IT professionals manage mobile devices over a normal internet connection, rather than forcing them to wait to manage devices until they connected to the organization's network.
MDM also gave organizations a way to apply security policies to mobile devices. Although mobile devices do not support group policies, MDM tools would often use ActiveSync policies as an alternative. ActiveSync policies could set password requirements for a device, disable hardware such as Bluetooth radios or cameras, require storage encryption or perform any other security configurations.
Although MDM tools solved several fundamental problems, they weren't perfect. MDM tools came shortly after the first smartphones, which meant that the technology had not yet had time to mature. As such, some MDM tools were OS-specific. For example, an MDM tool might have only worked with Android but not iOS, although some MDM tools of the time were cross-platform. Likewise, MDM tools tended to be extremely limited in scope. Organizations often used separate tools, known as mobile application management (MAM) tools, to handle applications on mobile devices.
Common MDM benefits and features include the following:
- Improved productivity.
- Decreased downtime and deployment times.
- The ability to apply security policies to mobile devices.
- Device auditing and reporting capabilities.
- VPN connectivity.
What is EMM, and what are EMM tools used for?
Enterprise mobility management tools are similar to MDM tools, except they offer capabilities beyond those first-generation products. Rather than requiring a separate tool for application management, for example, EMM tools often combine mobile device and application management into a single tool.
Despite this, the advent of EMM was more than just a consolidation of management tools. EMM was designed to address a fundamental shift in how mobile devices were used in the enterprise.
First-generation mobile devices were limited in their capabilities and were often used as little more than mobile email clients. However, users started integrating various business applications as their devices matured. At the same time, the BYOD trend began to take hold, bringing a need for a tool to protect business data on a device, regardless of whether the device was personally or company-owned.
Additionally, organizations needed a way of managing large numbers of mobile devices. By this time, mobile devices had gone mainstream, and device proliferation was becoming a huge problem in the enterprise.
EMM tools helped address the new challenges posed by mobile devices. These tools typically enabled users to enroll their own devices and let IT pros manage corporate-owned devices alongside BYOD devices at scale while protecting corporate data residing on the devices. EMM tools led organizations to develop comprehensive management strategies for mobile devices.
Features commonly found in EMM tools include the following:
- Cross-platform management of devices through a single pane of glass.
- Tools for enforcing device security through policies.
- A self-service portal for device enrollment and removal.
- Remote wipe capabilities.
- Application management.
What is UEM, and how are UEM tools different from MDM and EMM?
Unified endpoint management is a next-generation replacement for EMM. Like EMM and MDM tools, UEM platforms can manage mobile devices. The difference is that UEM tools also manage other endpoints, such as PCs and laptops. Some such tools even offer the ability to manage other types of endpoints, including IoT devices or wearables.
Vendors took the first step to improve endpoint management tools with the evolution from MDM to EMM, which provided a single tool for all the mobility management functions. Some organizations saw an influx of mobile users with complex management needs and realized they could run one EMM tool to handle all of these functions.
UEM tools were the next step in this evolution. EMM vendors added desktop and laptop management capabilities to their tools, while PC management vendors added mobile endpoint management functions.
Common features of UEM platforms include the following:
- Support for mobile operating systems, such as iOS and Android.
- Support for desktop and laptop operating systems, such as Windows, MacOS and Linux.
- Support for several different types of apps, including apps developed internally, apps from a public app store, apps purchased outside of an app store, web apps and built-in apps.
- Auditing tools that can identify devices that do not conform to the organization's security or compliance requirements.
- Security features, such as malware scanning and patch management.
- Reporting capabilities.








