enterprise mobility
What is enterprise mobility?
Enterprise mobility is an approach to work in which employees can do their jobs from anywhere using a variety of devices and applications.
The term commonly refers to the use of mobile devices, such as smartphones and tablets, for business purposes. But it also covers the mobility of corporate data and of workers themselves. As an example of enterprise mobility, an employee may upload a presentation from their desktop PC to a cloud storage service, and then access it from a personal Apple iPad to show at a client site.
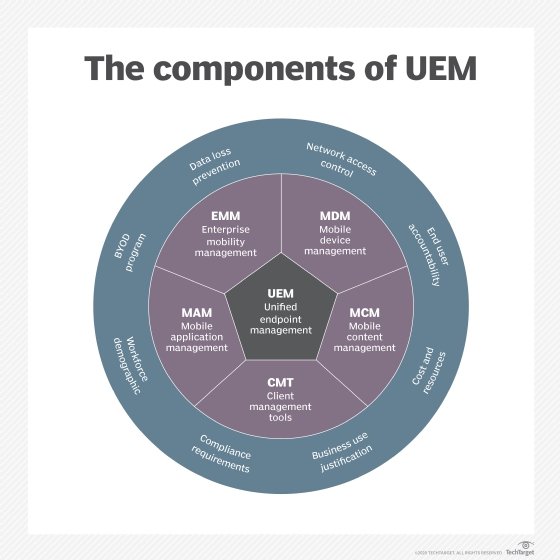
Enterprise mobility management (EMM) and other technologies have emerged to help IT departments enable mobile workers and to address security risks. A strong acceptable use policy for employees can also contribute to a successful enterprise mobility strategy.
Why is enterprise mobility important?
Enterprise mobility is important because it gives employees flexibility and choice, which can improve job satisfaction and increase productivity. Plus, by now every organization is already doing some form of enterprise mobility anyway.
Early enterprise-class mobile devices were typically employer-provided. These devices focused on providing personal information management capabilities, which included mobile access to email, calendars and contacts.
In 2007, Apple released the first iPhone, and Google followed with its own mobile operating system, Android. The iPhone and Android smartphones targeted consumers, and they helped introduce the concept of app stores to the masses.
As more consumers purchased these smartphones, and as more developers built enterprise apps for them, the bring your own device (BYOD) trend was born. Employees began using their personal smartphones for work -- often without employer permission -- because the devices and their apps enabled them to do their jobs more quickly and with a more streamlined user interface.
At the same time, American workers started to spend increasingly more time out of the office. By 2017, 43% worked remotely on at least a part-time basis, according to a Gallup survey.
In response to these converging trends, organizations adopted BYOD policies and took other steps to formally embrace enterprise mobility and flexible work styles.
BYOD is not the only enterprise mobility strategy option, however. Some organizations -- particularly in the government and highly regulated industries, such as finance -- continue to buy devices for employees and lock them down strictly for corporate use. There is also a middle-ground approach called corporate-owned, personally enabled (COPE). With COPE, an organization buys devices for employees, but with the understanding that they will use them for both business and personal tasks.
Understanding enterprise mobility security
The BYOD trend stoked fears in IT departments because employees were finding their way around existing security controls and using unmanaged devices to access corporate networks, applications and data.
In the early days of enterprise mobility, mobile device management (MDM) software was the primary security measure. This technology enables IT to remote-wipe devices, enforce the use of passcodes, blocklists and allowlists, and otherwise control what users can and can't do on their smartphones and tablets.
Faced with employees reluctant to give IT that much control over their personal devices, organizations turned to more granular enterprise mobility security measures. These included the use of mobile application management (MAM) and identity and access management.
MAM enables IT to control and secure specific apps without managing the rest of the device. Some MAM technologies use application wrapping, which hooks directly into an application's code to provide management capabilities. Others create a secure container for a group of apps to keep them and their data isolated from the rest of the device. There are also some MAM application programming interfaces built directly into Android and Apple iOS.
Identity and access management enables users to log on to multiple types of corporate applications -- including desktop, mobile and cloud apps -- with one set of credentials. This approach aims to simplify the management of multiple user accounts per employee, which can otherwise open organizations up to security risks.
MDM, MAM, and identity and access management capabilities are now typically bundled together as part of larger enterprise mobility management suites.







