What is COPE (corporate-owned, personally enabled)?
COPE (corporate-owned, personally enabled) is a type of mobile device management (MDM) model that allows employees to use corporate-owned mobile devices for specific types of tasks that are not directly related to work.
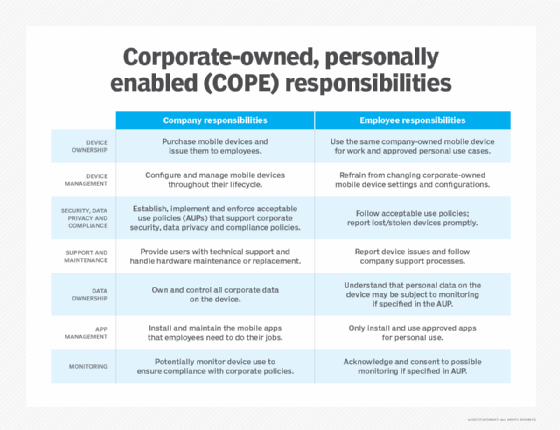
When a company uses a COPE model, it is responsible for purchasing, provisioning and maintaining the notebook computers, tablets and smartphones employees use to do their jobs. The company is also responsible for creating and enforcing acceptable use policies (AUPs) that govern how employees use corporate-owned devices outside work.
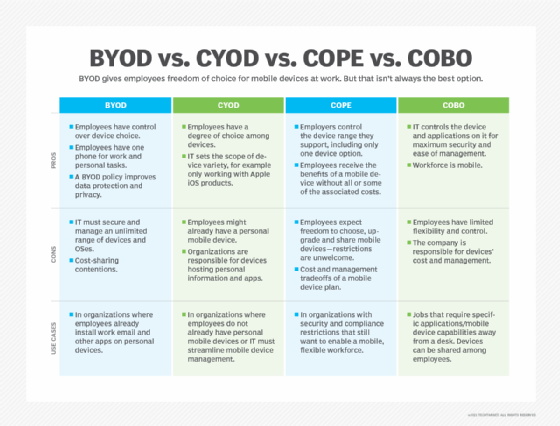
COPE can be an effective strategy for balancing employee convenience with the need for IT control. In large enterprises, this approach can be contrasted with bring your own device (BYOD) strategies, where employees use their personal devices for work, and corporate-owned, business-only (COBO) strategies, where corporate-owned devices are strictly limited to professional use.
What are the benefits of COPE?
The COPE model offers several advantages for both businesses and employees. Its blended approach to mobile device management can be a versatile solution for organizations seeking better control over their IT infrastructure, proprietary data and employee experience.
One of the most significant benefits of COPE is cost efficiency. When organizations purchase mobile devices in bulk, they can often secure wholesale discounts for hardware, software licenses and data plans. Standardizing a limited set of device models, OSes and configurations can also help IT departments reduce the operational costs associated with device provisioning and technical support.
Security and compliance are also major advantages of COPE. Because the organization owns COPE devices, IT can employ safeguards such as encryption, remote wipe capabilities, multi-factor authentication (MFA) and zero-trust. Unified endpoint management (UEM) software and other types of mobile device management tools can help protect sensitive company data and facilitate compliance with industry regulations such as GDPR, HIPAA or the Sarbanes-Oxley Act.
For employees, COPE offers the convenience of using the same device to complete work and a limited number of personal tasks. The IT team provisions, manages and supports COPE devices, so employees don't have to worry about installing security patches, handling software updates or troubleshooting technical issues. This can help eliminate the frustration employees in BYOD environments face when they need to reconfigure personal devices to meet changing security and compliance policies.
What are some common challenges of the COPE model?
One of the biggest challenges associated with the COPE model is that the organization is responsible for purchasing a large number of mobile devices and then managing the devices until their end of life (EOL). The upfront costs can be significant, and the requirements for provisioning, deploying and maintaining COPE devices can increase IT workload and necessitate additional staff.
If it has not already, the organization must invest in enterprise mobility management (EMM) and/or unified endpoint management (UEM) solutions. The IT team uses this software, which can be deployed on-premises or purchased as a cloud service, to configure, monitor, secure and manage mobile devices, applications and data across the organization from a centralized platform.
How does COPE compare to BYOD and other ownership models?
The overhead that COPE creates may not be cost-effective for all use cases. Smaller organizations or businesses with less stringent security and compliance requirements might find BYOD (bring your own device), CYOD (choose your own device) or COBO (corporate-owned, business-only) ownership models more practical.
BYOD (bring your own device)
BYOD allows employees to use personal devices for work-related tasks. While this approach can reduce an organization's hardware costs, it requires the organization to implement network access controls for mobile devices that enforce compliance with company policies. If employees use workarounds to avoid policy enforcement, they can introduce security and compliance risks.
CYOD (choose your own device)
CYOD provides employees with a pre-approved selection of corporate devices from which they can choose. This model gives employees more flexibility while still ensuring device standardization. Anecdotally, CYOD rollouts are known to improve productivity because employees will typically choose devices they already know how to use. In turn, this can lead to faster onboarding and fewer support requests down the road.
COBO (corporate-owned, business-only)
COBO strictly limits devices to work-related tasks and prohibits personal use entirely. This model is common in high-security industries such as government, military and healthcare, where sensitive data protection is paramount. While COBO deployments can help ensure maximum security, their limitations can frustrate users and lead to lower job satisfaction.
Hybrid mobile device management
In the past, many MDM tools limited IT to using either BYOD or COPE but not both. Today, the cloud is making it easier for organizations to use more than one ownership model and support hybrid mobile device deployments.
In a hybrid MDM model, some employees use company-owned devices that IT has completely locked down, some employees use COPE devices, and some employees use personal devices that have limited access to corporate resources. This approach is becoming increasingly popular because it allows companies to manage their employees' device experience more efficiently.
To be effective, hybrid rollouts should be supported by acceptable use policies aligned with the organization's security, data privacy and compliance standards.
How does a COPE policy work?
COPE policies work by documenting exactly how employees can use corporate-owned mobile devices for both work-related and personal tasks. In many cases, a COPE policy also makes it clear to the end user that the device is primarily intended to support business operations, and business-related functions always come first.
A COPE policy usually states that the organization will supply the end user with a device, pay for the mobile network service and support the device. COPE policies also specify which applications and websites are permitted for personal use and what level of access the organization's IT department has to personal data stored on the device.
COPE policies are important because they eliminate ambiguity about employer and employee responsibilities. Ideally, the transparency that this type of mobile device management policy provides encourages employees to use corporate-owned mobile devices responsibly.
Implementing a COPE policy
Successfully implementing a COPE policy requires the IT department to work with internal stakeholders in other departments. Here's a breakdown of the essential steps:
Define security and compliance requirements
First, the IT team should work with stakeholders across the organization to understand the its security, data privacy and compliance needs. This helps them align the COPE policy with the organization's risk tolerance and regulatory obligations and determine what level of control should be required for each configuration.
Address privacy and data separation
Next, IT management should collaborate with legal, HR and other department leaders to draft clear policies outlining acceptable use, personal app restrictions and data privacy expectations. Employees should be informed if their IT department will monitor private browsing data or other personal information stored on the device.
Plan for technical support and device management
A well-structured technical support plan for COPE deployments should define what technical controls the organization implements to enforce the policy for COPE devices. The plan should identify what mobile device management tools the organization uses and document requirements for service-level agreements (SLAs), escalation procedures and help desk availability.
Monitor and adapt policy over time
As technology evolves, organizations must continually update their COPE policies. Employee feedback, regular security assessments and network log analysis can help organizations refine and update COPE AUPs to meet changing business needs.
The future of COPE
In the future, expect AI-powered tools to play a larger role in streamlining COPE device management. Companies are already using machine learning (ML) to automate provisioning and policy enforcement, and AI agents are increasingly capable of providing users with chat-based technical support.
As hybrid work continues to be popular and the line between personal and professional use cases continues to blur, the integration of large language models (LLMs) will allow organizations to customize COPE policies quickly for specific job roles and responsibilities. In turn, this will help organizations improve security and compliance while reducing the overhead costs associated with COPE deployments.
Now that you know the meaning of COPE and understand the pros and cons, it's time to learn how to identify and deal with unmanaged network devices that your employees may be using at work. Also, explore what BYOD trends will take hold in the business world.






