physical layer
What is the physical layer?
The physical layer is the first and lowest layer of the Open Systems Interconnection (OSI) communications model. The physical layer's function is to transport data using electrical, mechanical or procedural interfaces.
OSI is a reference model used to show how applications communicate over a network. The model focuses on providing a visual design of how each communications layer is built on top of the other, starting with the physical cabling all the way to the application that's trying to communicate with other devices on a network. IT networking professionals use the OSI model to conceptualize how data is sent or received over a network.
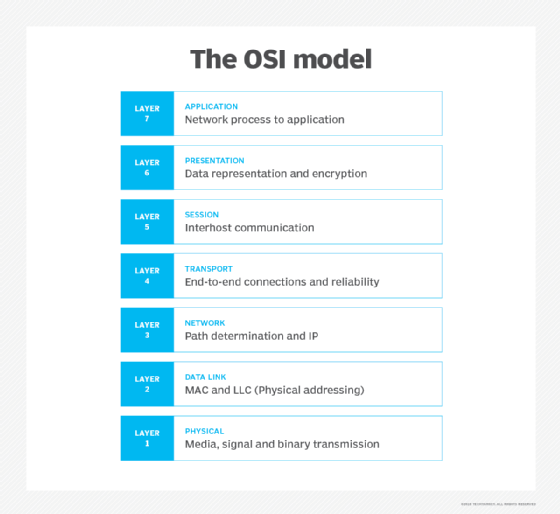
The physical layer is the layer closest to the physical connection between devices. This layer covers a variety of devices and mediums, among them cabling, connectors, receivers, transceivers and repeaters. The physical layer doesn't deal with the physical medium, but it specifies the properties and physical connectivity of low-level parameters, like electrical connectors. The physical layer acts as a foundation for the other layers. It's also useful for understanding the connections between devices, while adding visibility can aid in some risk mitigation processes.
The physical layer determines how to use electricity to place a stream of raw bits from Layer 2, the data link layer, onto the pins and across the wires of a twisted-pair cable. From an optical standpoint, the physical layer converts a stream of zeros and ones onto fiber using light as its physical medium. Lastly, the physical layer uses a wireless transmitter to convert these bits into radio waves for transport.
Functions of the physical layer
The physical layer is responsible for sending computer bits from one device to another along the network. Its role is determining how physical connections to the network are set up, as well as how bits are represented into predictable signals -- as they are transmitted either electrically, optically or by radio waves.
To do this, the physical layer performs a variety of functions, including the following:
- Defining bits. Determines how bits are converted from zeros and ones to a signal.
- Data rate. Determines how fast the data flows in bits per second.
- Synchronization. Ensures that sending and receiving devices are synchronized.
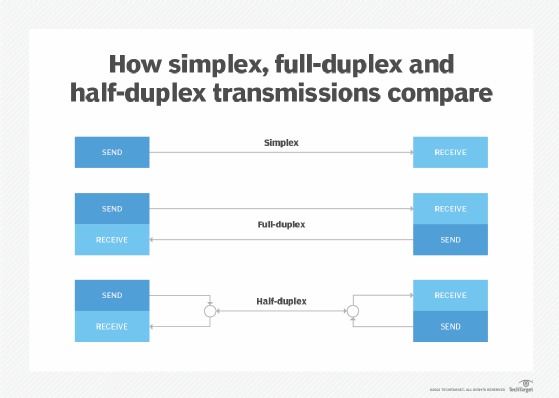
- Transmission mode. Determines the direction of data transmissions and whether those are simplex (one signal is transmitted in one direction), half-duplex (data goes in both directions but not at the same time) or full-duplex (data is transmitted in both directions simultaneously).
- Interface. Determines how devices are connected to a transmission medium, such as Ethernet or radio waves.
- Configuration. Provides point-to-point configurations and multipoint configurations.
- Modulation. Converts data into radio waves.
- Switching mechanism. Sends data packets from one port to another.
- Signal equalization. Helps create more reliable connections and makes multiplexing easier.
Physical topology
Physical topology refers to how devices are linked. Physical topologies include the following:
- Mesh topology. Mesh topologies consist of devices, also referred to as nodes, that are linked to every other node in the network. These networks are set up to efficiently route data between devices and clients.
- Star topology. Star topologies are a local area network topology where all nodes are directly connected to a common central computer.
- Bus topology. Bus topologies consist of multiple devices that are connected through one cable called a backbone cable. Devices connected to a bus topology directly connect and transmit data to one another.
- Ring topology. Ring topologies are a configuration where every node directly connects to two other nodes on a network, creating a circle. Data sent to a node transmits from one node to another around the ring until it reaches its destination.
- Tree topology. Tree topologies are structured in a hierarchical structure where nodes link together like a tree when drawn out in network diagram form.
- Hybrid topology. Hybrid topologies are a combination of two or more other topologies and are used depending on factors related to performance, reliability or cost.

The physical layer also provides the previously mentioned transmission modes:
- A simplex mode where only one node can transmit data and the other node receives data.
- A half-duplex mode where two nodes can send and receive data but not at the same time.
- A full-duplex mode where data can be sent and received from both nodes at the same time.
Examples of physical layer protocols
The physical layer is usually a combination of software and hardware programming. It includes a number of protocols that govern data communications on a network. Some examples of Layer 1 protocols are the following:
- 1000BASE-T Ethernet.
- 1000BASE-SX Ethernet.
- 100BaseTX Ethernet.
- Synchronous Optical Networking/Synchronous Digital Hierarchy.
- 802.11 physical-layer variants.
- Bluetooth.
- Controller Area Network.
- Universal Serial Bus.
Learn more about the OSI model, as well as how it's different from TCP/IP.





