
Getty Images
Use Angry IP Scanner to audit the network
Angry IP Scanner provides a network scanner alternative to Nmap that is simple, user-friendly and versatile across OSes. Scan types include ping scans, UDP scans and TCP scans.
IP address scanners are useful network administration tools that report IP-based devices on a network. Scanners provide information such as the number of devices, device configurations and network organization.
Scanners can report various types of information that is useful for network audits and documentation, usually displaying some combination of the following:
- MAC address.
- IP address.
- Hostname.
- Open ports.
- OS.
- Services.
Administrators use this information to gain a clearer picture of the network's organization.
Angry IP Scanner is a cross-platform scanner that simplifies the gathering and reporting of network information. Administrators appreciate it for being easy to work with, portable and extensible.
This article examines how to use Angry IP Scanner, including the process of installing the tool on Windows, Linux and macOS. It also explores how to run basic scans and customize results.
Angry IP Scanner vs. Nmap
The standard go-to tool for network scanning is Nmap, which is powerful and flexible. Nmap, however, can be overwhelming in its flexibility and options. While its Zenmap graphical interface is available and well laid out, Nmap assumes administrators work from the command line. Sometimes, Nmap is just overkill.
Enter Angry IP Scanner. Angry IP Scanner relies on an intuitive and straightforward graphical interface. The tool provides all the basic information at a glance in an interface that doesn't require tweaking or time to learn. It's a helpful tool for a quick but thorough look at a network, network segment or group of IP addresses. Its extensibility adds customization options, but it's good out of the box.

Install Angry IP Scanner
Angry IP Scanner offers four installation options: pre-compiled installers for Windows, Linux and macOS, plus the source code. The tool is open source and licensed under the GNU General Public License, version 2.
One benefit Angry IP Scanner offers is Java-based portability. The tool uses Java, and most of the pre-compiled installers include Java Runtime Environment.
Windows installation
From the Download section on the Angry IP Scanner homepage, select Windows. The two following installers are available:
- Windows installer. Installs the application, including the necessary Java Runtime.
- Standalone executable. Application executable that installs a separate Java Runtime of version 3.7.6 or higher.
MacOS installation
Installers are provided for older Intel-based Macs and the newer M1- and M2-based silicon Macs. Angry IP Scanner offers a downloadable bundle for either version, both of which include Java Runtime.
The first time you run a downloaded program on a Mac, it prompts you to allow applications other than those from the Mac store. This is standard with many Mac apps.
Linux installation
Angry IP Scanner provides DEB- and RPM-based packages for Linux devices. DEB packages run on Linux systems derived from Debian and use the Apt package manager. These systems include Debian, Ubuntu, Kali and similar distros. RPM-based installers run on Red Hat Linux-derived distributions, such as Red Hat Enterprise Linux, Fedora and others. A separate package for generic architectures, such as Raspberry Pi OS on Raspberry Pi devices, exists. Finally, there's a standalone JAR version.
You need Java 11 or newer on your Linux box.
Compile the source code
Clone the appropriate GitHub project to get the Angry IP Scanner source code and supporting files. You can also download the source code as a TAR file without using Git.
Because Angry IP Scanner is open source, numerous older versions are available if needed. I recommend using the most current version.
Perform a basic scan
Run the program after installation, and examine the interface. You can also launch it using the ipscan command. Angry IP Scanner uses fetchers -- a term for the type of information collected about target hosts. For example, the standard fetchers are IP address, ping time, hostname and ports. This is the information you can expect Angry IP Scanner to show you.

Feeders is the Angry IP Scanner term for IP address scan sources. The UI offers the three following feeder options:
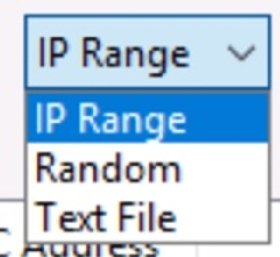
- Range of IPs. A predefined set of IP addresses for scanning specific segments or small networks.
- Random IPs. A random set of IP addresses within a range for basic audits.
- IPs from a text file. A list of IP addresses gathered from another tool or inventory.
Scan results are color-coded, making them easy to digest. Below are the color categories:
- Red. Dead hosts -- the target IP address is down or not responding to pings.
- Blue. Alive hosts -- the target IP address is active/busy and responds to pings.
- Green. Open ports -- the target IP address is up and shows open ports.
Click the Start button to initiate a scan. Angry IP Scanner is built for speed, but it is still beneficial to select a relatively small range of addresses during the learning process. Consider just a single segment -- one that you're already familiar with so you can recognize the devices Angry IP Scanner reports. You can interrupt a running scan with the Stop button.
Warning: While Angry IP Scanner is not marketed as a security tool, recall that your network security team might define IP scans as threats. Be sure you have permission to run such tools on the business network before initiating any scans.
Angry IP Scanner shows a summary after the scan results are complete.

Examine the results once the scan completes. You have two sources of information. The first is the basic list of results. This consists of whatever IP addresses and their status the scanner discovered. These results are displayed in a tidy column formation.

Second, select any individual result for some additional details. Again, Angry IP Scanner doesn't have Nmap's ability to delve into details, but most administrators don't need that depth for general scans. Details provided here include IP address, ping time, ports and MAC address.


Note that you can add your own comments to store additional host information.
Scan types with Angry IP Scanner
Angry IP Scanner runs different types of scans based on various protocols. Select the scan type from the Preferences menu.
Options include the following:
- Ping scans. Sends standard Internet Control Message Protocol echo requests.
- User Datagram Protocol (UDP) scans. Sends UDP connection attempts to ports.
- TCP scans. Sends port 80 HTTP connection attempts.
Save your results
Angry IP Scanner offers several options for saving scan results. You can save the entire scan or individual IP information. You can also save scan parameters, enabling you to repeat scans regularly without customizing them each time. It also enables immediate connections.
Export results
Save your complete scan results using the Export feature. From the File menu, select Export All, and save the results as a text file. Save results as a text file, CSV, XML or simple list. This is a great way to archive scans for future comparisons, showing how the population of a segment has changed over time.

You can also copy and paste an IP address or its details into a help desk ticket, documentation, presentation or other destination.
Favorites
Save your commonly used scans in the Favorites menu. This saves the IP address range and any specific parameters. The feature is helpful if you regularly scan individual subnets within your network. For example, maybe you check the business's guest network regularly to understand what devices are attached to it.

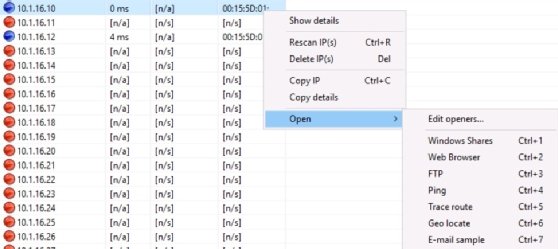
Open connections
Right-clicking an IP address result opens a menu that initiates HTTP, FTP, Server Message Block (SMB) and other connections to the selected address. This enables you to find a device via a scan and then connect to it immediately, which is a handy feature.
Use advanced features
Angry IP Scanner includes additional fetchers to extend the information it reports. Select these from the Tools menu.

This is a good example of why saving scans is useful. After you define exactly the scan you need, including additional fetchers, you can save the parameters.
When making a scan, you often know what specific ports you're interested in. Perhaps you already know you're looking for any web server or Windows device sharing folders via SMB. Define specific ports (protocols) to check using the Tools > Preferences > Ports interface. Doing so speeds up the scan, as the tool won't waste time investigating ports you don't care about.
Extend Angry IP Scanner with plugins
Developers can add Java-based plugins to Angry IP Scanner, which extends its functionality. These are delivered as JAR files and must be placed in the same directory as the ipscan binary, which is the Angry IP Scanner executable.
Wrap-up
Angry IP Scanner shines as an administrator tool. It's not a hacker tool or pen testing utility because it doesn't have the stealth capabilities of Nmap. It gathers the most useful information administrators are likely to need quickly and offers the ability to save those results. Its Java base makes it portable, and the ability to run on all three major platforms makes it versatile. The fact that it's open source is icing on the cake.
Install and use Angry IP Scanner today to understand exactly what devices and services are exposed on your network.




