Zoombombing
What is Zoombombing?
Zoombombing is a type of cyber-harassment in which an unwanted and uninvited user or group of such users interrupts online meetings on the Zoom video conference app.
This disruption occurs when intruders gate-crash digital gatherings -- sometimes for malicious purposes, such as sharing pornographic or hate images or shouting offensive language -- without the host's permission.
The Zoom cloud platform offers video and audio conferencing, collaboration, chat and webinars via mobile devices, desktops, telephones and room systems and is the signature offering from Zoom Video Communications Inc., a publicly traded company founded in 2011.
Recognizable by its grid view that lets participants see everyone on a call at once, Zoom became popular because of its ease of use and installation, as well as its freemium pricing model.
With the COVID-19 virus outbreak in early 2020, demand for the Zoom video conferencing app surged to unprecedented levels as business meetings, classes and even family gatherings shifted online, and users sought ways to stay in touch virtually while social distancing.
As the number of Zoom meetings increased, reports of Zoombombing followed.
How Zoombombing works
In a March 2020 warning about Zoombombing, the Federal Bureau of Investigation (FBI) advised individuals transitioning to online meetings and classes to practice "due diligence and caution in [their] cybersecurity efforts." The FBI recommended keeping video conferences private and avoiding openly posting links to online gatherings on social media platforms, such as Twitter or Facebook. Hosts should provide links to specific invitees only, experts advised.
Conferences are vulnerable to Zoombombing when they are hosted on public channels shared over the internet through meeting URLs, making them easily accessible to unwanted trolling. If hijackers can figure out the correct URL or meeting ID for a public Zoom session, they can gain access to the meeting. A basic Google search for URLs containing "Zoom.us" can unearth unprotected links of meetings; plus, links to public meetings may be available on organizational pages on social media.
In addition, if Zoom screen-sharing privileges are not set to "host only," uninvited guests can share disturbing images or potentially malware. Also, a remote-control feature lets users take control of another participant's screen in a meeting. A user can either ask for remote control of another participant's screen, or the other participant can grant control to a user.
How to prevent Zoombombing
To avoid interruptions from Zoombombers, a conference host should use a one-time meeting ID and not a Personal Meeting ID -- a 10-digit number that someone could use to join the meeting without an invitation. Organizers should also require users to enter a passcode to join the call.
An additional protective feature is Zoom's Waiting Room, where the host must admit attendees. To activate Waiting Room, sign into the Zoom web portal, click Meetings and select a meeting topic or schedule a new meeting. Select Enable Waiting Room under Meeting Options.
Zoom has encouraged those hosting large, public group meetings to adjust their settings so that only they can share their screens. To ensure only the host of a meeting can share a screen, tap the Share Screen button, and select Advanced Sharing Options.
After the meeting has begun and all attendees are present, the host can lock the virtual room. Using the "More" menu to mute all participants as they enter and not allowing participants to unmute themselves can also help prevent disruptions. The host can remove participants by hovering over their names.
If a Zoom meeting is hijacked, users can let the company know. In a software update, the company added a "report a user to Zoom" button. This feature can produce a report to be "sent to the Zoom Trust and Safety team to evaluate any misuse of the platform and block a user if necessary," according to the company.
Zoom security updates
To help boost video conferencing privacy and security, users should employ the latest version of remote access/meeting applications, the FBI recommended.
In a January 2020 Zoom update, the company added password protection by default for meetings and disabled the ability to randomly scan for meetings to join.
In late April 2020, Zoom further tightened security with the release of new encryption and privacy controls to help prevent the hijacking of online meetings. The video conferencing platform now enables hosts to report a user to Zoom with a security button. Additionally, the app now sends users by default to a waiting room, where they must wait for approval to enter a meeting. A password is also necessary to enter all meetings.
In May 2020, Zoom upgraded its application encryption standard to Advanced Encryption Standard 256-bit Galois/Counter Mode. This adds a layer of privacy and minimizes the likelihood of video conferences being hijacked.
In the fall of 2020, Zoom settled a Federal Trade Commission complaint alleging the company had engaged in "deceptive and unfair practices" for years by falsely claiming to protect user communications with end-to-end encryption (E2EE).
Around that same time, the company added an E2EE option. In 2021, Zoom settled an additional class-action privacy lawsuit, denying wrongdoing but agreeing to compensate individual users and small business accounts for its allegedly false security claims.
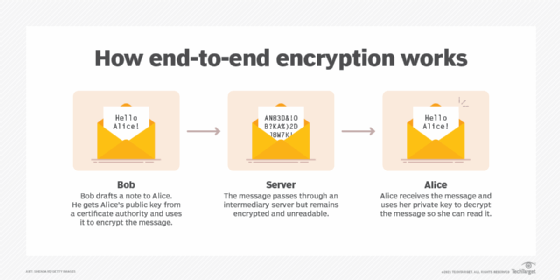
In addition to Zoombombing, the app was criticized for other vulnerabilities, including one in which a hacker could take control of a user's computer. Seeking to address security issues, Zoom has enhanced its bug bounty program to encourage security professionals to alert it to potential bugs. Zoom continues to issue patches as it uncovers new security vulnerabilities, and the company encourages users to keep their Zoom software up to date.
Zoom's success at addressing security and privacy issues will have a major impact on the application's success in the long run.
Another challenge Zoom faces is growing competition from Facebook, Google and Microsoft, as well as Cisco Webex, LogMeIn, GoToMeeting, BlueJeans and Arkadin Cloud Communications.
Editor's note: This definition was written by Corinne Bernstein in 2020. TechTarget editors revised it in 2023 to improve the reader experience.







