What is a passkey?
A passkey is an alternative user authentication method that eliminates the need for usernames and passwords. Rather than relying on old login methods susceptible to phishing or hacking attacks, keyloggers, data breaches and other security flaws, websites and applications can use passkeys to verify a user's login credentials. Passkeys are only stored on the user's device, so there is no password that could be intercepted by potential scammers.
Cybersecurity professionals have long stressed the importance of strong passwords to prevent security vulnerabilities. However, because web users often create weak passwords or reuse passwords, two-factor authentication (2FA) was developed. This adds a security checkpoint by confirming a user login with a phone call, text message or email containing a code sent to the user. The user then enters this code to complete the login process. Unfortunately, bad actors have found their way around 2FA and the standard login process. Because password technology is inherently vulnerable to phishing and other attacks designed to steal or bypass credentials, 2FA has only made things marginally more difficult for fraudsters.
How does a passkey work?
When a user attempts to log into a site that uses passkey technology, the site sends a push notification to the smartphone they used when they registered their account. When they use their face, fingerprint or personal identification number (PIN) to unlock their device, it creates a unique passkey and communicates it to the website they are trying to access. At that point, the user is logged in, all without their login information or biometric data being transmitted using a potentially insecure Wi-Fi connection or needing to be typed out.
Unlike 2FA, which uses Wi-Fi or other methods for user verification, passkeys use Bluetooth. Bluetooth checks to ensure the device logging in is nearby, further limiting the chances of a scammer or hacker accessing the user's account.
Passkeys, which are based on the Web Authentication API, only work for the website on which they were created. They are then stored on the user's device instead of on a physical or cloud-based server.
To date, Apple offers the most thorough explanation of how passkeys work within its tech ecosystem. Its iCloud Keychain service stores its cryptographic keys in a rate-limited way to prevent brute-force attacks. The keys are recoverable even if a user's devices are lost or compromised. Those new to the Apple world and setting up their first iOS device must set up 2FA first. To add a new device, the user needs their Apple ID password and the six-digit code sent to another trusted device or phone number using a push notification.
For example, an iPhone user would set up 2FA the first time they use it and establish their Apple ID. When they want to make a purchase or complete some other secure transaction, they must enter their Apple ID password and check their iPhone -- or whatever device they used to set up their 2FA authentication initially -- for the six-digit code sent to them. When they enter the code, the new device is added to what Apple calls the circle of trust formed by the iCloud Keychain. This circle acts like a chain, and the devices represent links added to the chain as they are set up.
When the user needs to log into a website on a computer they do not usually use -- regardless of whether it's an Apple, Google or Microsoft product -- with passkey technology enabled, the login screen on the website provides a quick response code for them to scan with their phone. With Bluetooth enabled on their phone and the phone within Bluetooth frequency range of the device they're trying to log in on, they will receive a push notification to use biometric identification or a PIN on their phone. Once they do that, their phone will give the website the all-clear and allow the user to log in.
The origin of passkeys
The passkey idea first took hold in 2009, when Validity Sensors -- acquired by Synaptics in 2013 -- and PayPal jointly developed the concept of using biometrics instead of passwords for online identification.
Along with several other tech leaders, they founded the FIDO (Fast Identity Online) Alliance, a web security collective, in July 2012. FIDO publicly announced its initiatives in February 2013. Google joined in April 2013. In February 2014, PayPal and Samsung launched the first public deployment of FIDO authentication with Samsung's Galaxy S5 smartphone. Users of the device could, for the first time, authenticate PayPal with a finger swipe and shop online without having to enter a password to complete the transaction payment.
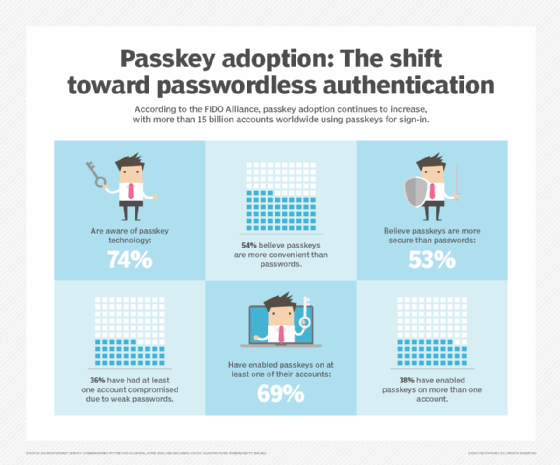
Is a passkey more secure than a password?
Because every passkey is unique, they tend to be more secure than passwords because they cannot be reused across multiple sites and platforms. And because passkeys are generated automatically, users do not need to rely on passwords that are either easy to remember -- and unfortunately, easy for others to guess -- or so complicated that they are easily forgotten.
Because passkeys use end-to-end encryption, not even the companies creating them can see or change them. Apple says its passkeys use public key cryptography and create two keys. One key is public and stored on the website's server; the other is private and stored on the user's device, so it is only accessible to that user.
This means that the private keys generated in each passkey pair are only stored on the user's device, not on any website's server, making it impossible for the user's login information to be discovered through a data breach or hacking attempt. A hacker could only access the public key, which would be useless to them because it would not grant access to the user's account information. Even if someone were to fall prey to a phishing link in an email or text message, the effort would fail because the passkey on the user's device would only work with the website that created it.
Companies that use passkeys
Awareness of passkey technology has accelerated. At the FIDO Alliance May 2022 conference, Apple, Google and Microsoft publicly announced a major initiative to promote passkeys as a passwordless authentication standard, and Apple followed through in June 2022 by announcing a new passkey feature. This feature debuted in iOS 16 and macOS Ventura, was integrated into the iPhone 14, and is part of subsequent releases.
The Apple passkey feature uses existing iOS technology powering its Touch ID and Face ID features. Websites that support passkeys enable users to create accounts and log in using their fingerprint or facial image instead of a password to authenticate their credentials. Apple passkeys use the iCloud Keychain password management system to back up passkeys and sync them across all a user's Apple devices. This means users can create a passkey for a website while on their phone and then use that same passkey to log in to that website later while using an iPad, for example.
Google passkeys use similar fingerprint and facial image passkeys on Chrome browsers, Android devices and Google accounts, including Gmail and Drive.
Microsoft includes passkeys on its Windows 10 and 11 operating systems through the Windows Hello program. This program enables users to log in with a PIN and biometric authentication, such as a fingerprint or a facial image. Passkeys are also available on Microsoft 365, Copilot and Xbox accounts. These services support passkey backups and device synchronization.
In addition to Apple, Google and Microsoft, hundreds of other companies -- including GitHub, Facebook, Instacart, Kayak, Verizon and Zoho -- use passkeys, and the list is growing.
The call for a passkey standard
Going forward, security professionals are advocating for implementing standards that will prevent or at least discourage vendor lock-in. The concern is about what happens with existing passkeys if a user switches from one vendor's product to another.
Some vendors have addressed this problem with workarounds. For example, Apple enables an existing passkey for an iPhone to be used on another device with Google Chrome running on either iOS 16 or later or on a Windows machine.
It remains to be seen if standardization efforts are successful, but creating new passkeys is so easy and almost entirely automated that users should be able to easily establish credentials on a new device from a different vendor.
The FIDO Alliance Design System and other methodologies published by the alliance should help encourage standardization.
Passkey use is growing
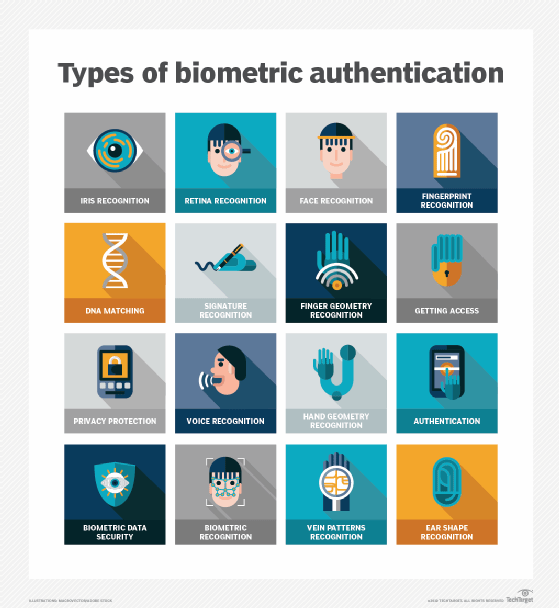
Much of passkey's underlying technology has already been integrated into everyday tech life, such as 2FA and biometric authentication that rely on a user's face or fingerprint to unlock a device or otherwise provide authentication.
Growing security vulnerabilities and password management issues are prompting many organizations to abandon password use in favor of passkeys. Users are also becoming increasingly frustrated with managing a multitude of different passwords, forcing a shift toward more secure alternatives like passkeys.
In September 2024 and April 2025, the FIDO Alliance Working Group commissioned a survey regarding passkey deployments worldwide. It found that 87% of the decision-makers surveyed have deployed passkeys at their organizations with 47% having rolled out a mix of physical security keys, cards and synced passkeys.
Learn how identity management and authentication compare as part of an identity and access management framework.