
Andrea Danti - Fotolia
Key steps to put your zero-trust security plan into action
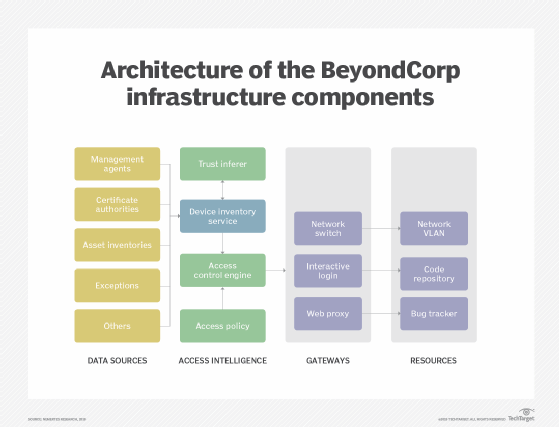
There are three key categories of vendor zero-trust products. Learn what they are, and how to evaluate and implement the one that's best for your company.
A zero-trust microsegmentation model for access control potentially has many benefits, but implementing this technology strategy requires significant planning and coordination across teams. The first decision that an organization will need to make is that of which technology to select in implementing zero-trust security. There are a number of vendors that offer microsegmentation tools, and there are many differences between the various products:
- Network-centric products: Well-known networking companies have begun to offer microsegmentation policy engines and enforcement controls within network switches and other connectivity platforms. The benefit of these products is usually a unified approach across that vendor's hardware and often other vendors' as well, as long as the network traffic crosses their switches. Drawbacks include vendor lock-in and costs, as well as some potential limitations in moving to cloud scenarios.
- Virtualization-specific products: Leading hypervisor providers may offer zero-trust microsegmentation platforms, as well. These benefit from deep integration with both the hypervisor and software-defined networking, but may not be as applicable to physical systems.
- Stand-alone zero-trust security software: This is software that has its own unique policy engine, as well as host-based software. While this option may be the most flexible in some ways across internal and cloud environments, it could also be prone to vendor lock-in and performance issues.
While looking at options, be sure to consider platform compatibility (some legacy systems or certain operating systems may not be wholly compatible), availability in cloud environments, and complexity or operational requirements for management and ongoing maintenance.
Putting a zero-trust security tool to work
Once the platform or tool of choice is selected, the next major planning element -- besides installation -- is policy design. Most of the leading providers of zero-trust security tools offer a form of "learning mode" that you can start out in, and that's definitely the right choice for almost all organizations -- enable the zero-trust engine and then monitor for what it sees. What you're looking to do is monitor what types of applications and services are communicating between systems and network segments, and map the communications to evaluate what is likely sanctioned and what might be malicious or unwanted traffic. When planning your policies, be sure to work closely with application, desktop and server operations teams to better understand what is actually running in your environment, as these teams will likely have a more accurate view of what communications should be in place. This way, you can build consensus on policy implementation before actually locking anything down.
At the same time, it's helpful to think about a "tagging" or "grouping" model that makes the most sense in your zero-trust security architecture. In other words, what systems are alike and which systems should be communicating as part of defined application workloads? Common grouping strategies include business units (systems owned or maintained by a specific group or functioning as part of a business group), platform or application similarity (all databases or Windows servers, for example), and sensitivity levels (all systems in scope for PCI DSS compliance or those handling financial transactions). Choosing sound grouping for policies will enable them to be implemented more quickly and effectively; it may also make the policy design and governance discussions easier, since you'll likely be working with existing teams that know how their applications should be functioning.








