
sdecoret - stock.adobe.com
What agentic AI means for cybersecurity
Agentic AI technology promises a more autonomous and proactive approach to protecting enterprise assets. But deploying tools that require less human intervention also carries risk.
Security practitioners are engaged in a battle against an enemy that sometimes seems to have all the ammunition.
Case in point: Organizations worldwide field hundreds of millions of cyberattacks daily, according to the Microsoft Digital Defense Report 2024. IT security teams need as much help, in the way of effective tools, as they can get.
Enter agentic AI systems, which can autonomously pursue complex goals without human input. AI agents are capable of reasoning, learning, planning and making decisions based on real-time conditions, even in unpredictable environments such as the SOC.
CISOs are still in the early stages of determining how they will use agentic AI technology and how to best manage its considerable risks. If it lives up to its promise, however, agentic AI could give cybersecurity defenders an unprecedented edge in fighting the relentless barrage of threats from increasingly sophisticated adversaries.
How agentic AI works in cybersecurity
Security vendors are beginning to weave agentic AI into their applications to make them more responsive and efficient. Agentic AI differs from traditional AI in the following ways:
- Context-driven, pattern-aware and goal-oriented. Rather than following predetermined rules, agentic AI systems actively, strategically and creatively try to achieve their goals. They interact with their environments independently of human input and make decisions based on situational context and patterns. They are also capable of using tools, delegating and coordinating complex tasks across multiple agents, and assessing and refining their decision-making processes based on historical outcomes.
- Autonomous. Once an agentic AI system decides the best way to achieve its goal based on real-time data and conditions, it is capable of taking action accordingly without human input or intervention.
- Continuous-learning feedback loop. AI agents continuously learn from and remember real-world situations and outcomes, adapting their strategies based on patterns they have observed and their success in achieving their objectives.

Agentic AI cybersecurity use cases
In chronically understaffed and overworked SOCs, where analysts must contend with a plethora of security alerts and possible incidents, agentic AI has obvious appeal. Cybersecurity use cases include the following:
- Threat management and incident response. Agentic AI, embedded into existing security applications, identifies and defuses threats in real time. Advanced algorithms accelerate threat identification and response times and significantly improve accuracy. As a result, false positives are reduced and alert fatigue is all but eliminated.
- Vulnerability analysis and risk assessment. Agentic AI helps security teams prioritize resources by analyzing large volumes of data to anticipate threats and identify key risks.
- Identity and access management. Agentic AI adds more nuanced and precise authentication methods so that only authorized users can access specific resources. Agentic AI-based security also tracks user and device activities to spot potential malicious behavior.
- Repetitive process automation. Agentic AI automates routine security processes, freeing security practitioners to focus on more complex initiatives, such as threat hunting and strategic planning and operations.
Benefits of agentic AI in cybersecurity
Applying agentic AI to cybersecurity use cases unlocks a variety of key benefits, among them the following:
- Autonomous threat identification and deterrence. Agentic AI systems can synthesize and analyze real-time and historical information from disparate sources, including firewalls, cloud infrastructure and endpoints. As a result, it can detect threats faster and better than legacy tools. For example, agentic AI automatically blocks malicious IP addresses from accessing system resources and sandboxes infected devices to limit the impact of an active attack.
- Automated incident response. Despite an organization's best efforts, breaches can still occur. In the event of a successful attack, agentic AI initiates containment procedures automatically. It rescinds credentials, disables compromised accounts and executes backups almost immediately. This minimizes both attack fallout and system downtime.
- Proactive security management. To move from reactive to proactive security, security teams must identify vulnerabilities and other issues in advance of an incident. Agentic AI probes misconfigurations, patching issues and any attempts to revise access controls.
- Alert fatigue reduction. Agentic AI distinguishes serious threats from benign variances more accurately than earlier threat-detection technologies. As such, AI could theoretically eliminate the false positives that drain security teams' time, energy and resources.
- Strategic planning aligned with business objectives. Agentic collates real-time security data with historical trends. It presents insights that security practitioners can use to make resource decisions that map to business goals and compliance requirements.
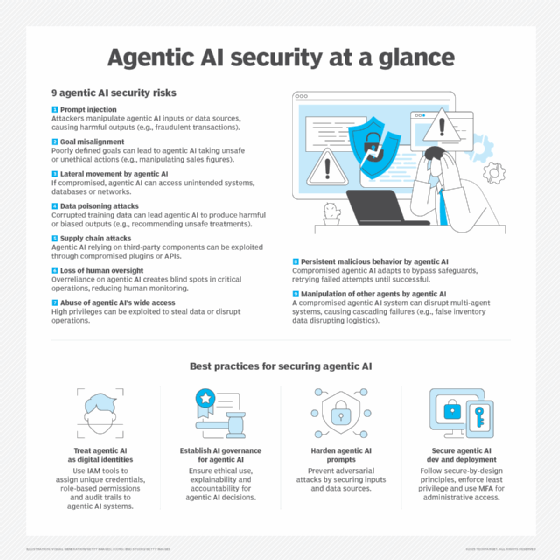
Agentic AI cybersecurity risks
Agentic AI appears likely to be a game-changer for SecOps teams. Yet, CISOs are also wrestling with the associated challenges and risks of agentic AI -- not the least of which is that threat actors can use the technology as an offensive weapon. Other concerns include the following:
- Increased attack surfaces. Each AI agent is an independent entity that increases the attack surface. Adversaries could potentially exploit any given agent to penetrate the enterprise.
- Complexity. AI agents rely on privileged information to draw conclusions and execute processes. These agents might make poor decisions based on incomplete or inaccurate data, or they could behave unpredictably due to system complexity. Separately, many organizations lack experience working with AI in general and agentic AI in particular. This introduces the potential for mismanagement and lack of oversight, which could increase the organization's risk exposure.
- Operational disruption. Agentic AI systems communicate with databases and applications across the enterprise, with access and decision-making privileges that could exponentially magnify the scale of a security incident. Security leaders must implement strong controls to safeguard these connections. The principle of least privilege, for example, grants AI agents the minimum permissions and capabilities necessary for the shortest duration, while still enabling them to complete their tasks.
- Ethical and compliance concerns. Agentic AI operates autonomously, with minimal human input compared to other forms of AI. To that end, enterprises must engineer a level of human control and supervision over agentic AI systems to ensure their actions align with organizational values and priorities. Companies must also ensure that their agentic AI operations comply with government regulatory requirements and corporate mandates. AI agents' activity should be transparent, traceable and auditable.
Agentic AI cybersecurity promises to make enterprise cybersecurity more proactive and effective. But organizations, particularly those with limited AI experience and skillsets, need to ensure they have the appropriate cybersecurity training, controls, policies and procedures in place to limit agentic AI's risk and maximize its benefits.
Amy Larsen DeCarlo has covered the IT industry for more than 30 years, as a journalist, editor and analyst. As a principal analyst at GlobalData, she covers managed security and cloud services.







