Cybersecurity vs. cyber resilience: What's the difference?
Companies need cybersecurity and cyber-resilience strategies to protect against attacks and mitigate damage in the aftermath of a successful data breach.
The volume and velocity of cyber attacks aren't slowing any time soon. Companies today need to be ready and able to protect their data in the event of an attack, while also being prepared to handle fallout should a system compromise occur.
Cybersecurity and cyber resilience are two terms used in this discussion. Read on to learn more about each and why both are crucial to any enterprise security strategy.
What is cybersecurity?
Cybersecurity is one of the most widely used terms in IT. It is defined in the following way: "Cybersecurity is the protection of internet-connected systems, such as hardware, software and data from cyberthreats. The practice is used by individuals and enterprises to protect against unauthorized access to data centers and other computerized systems."
Cybersecurity standards and frameworks specify how to prepare for and respond to attacks and vulnerabilities. A strong cybersecurity strategy and program greatly help affected organizations mitigate attack damage from data breaches; vulnerabilities; malware attacks, such as ransomware or phishing; insider threats; human error; and other attacks by malicious hackers. Prudent investments in cybersecurity software, hardware and perimeter protection systems -- for example, firewalls and intrusion prevention systems -- can turn a potential business-killing attack into an easily handled minor event.
What is cyber resilience?
Cyber resilience is a more recent term. Resilience is the ability of an organization to modify and adapt how it does business to quickly recover and resume operations following a security breach. A cyber-resilient organization can better respond to and recover from future security incidents. It can also resume normal business operations more quickly and effectively.
This might sound a lot like cybersecurity, and that's because it includes cybersecurity efforts. It also includes incident response, business continuity (BC) and disaster recovery (DR). These four components are traditionally siloed from each other. A union among them is critical to achieve cyber resilience.
How to align cybersecurity and cyber resilience
Organizations need to use cybersecurity and cyber resilience together to protect them from today's threats, malicious actors and disasters.
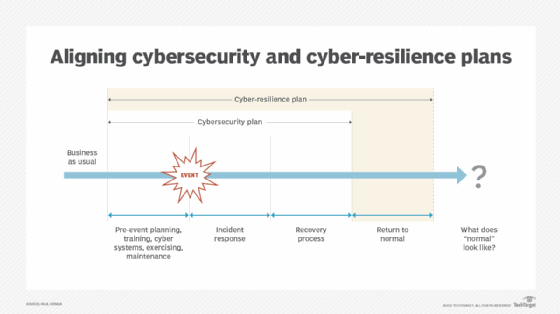
Cybersecurity is a core component to achieving resilience. It provides the foundation for a strong cyber-resilience program that incorporates the following:
- Cybersecurity systems, including specialized servers and network devices.
- Antivirus and antimalware software.
- Threat analysis software.
- Perimeter protection systems.
- Employees trained in managing cyber attacks.
- Senior management support.
- Regular security awareness trainings for employees.
- Periodic incident response exercises to ensure teams know how to manage cyber attacks.
- Policies optimized for cyber resilience.
- Procedures to specify how to handle cyber attacks from beginning to end.
A key element of a cyber-resilience strategy is to define normal business operations. A return to as close to normal as possible is the goal of a cyber-resilience program. The COVID-19 pandemic, for example, forced many businesses to adapt to new working conditions, with employees outside the traditional perimeter. Normal operations have thus changed to a hybrid work model for many. Regardless of what normal looks like, cybersecurity and cyber-resilience plans need to adapt to the new normal.
It's cybersecurity and cyber resilience, not cybersecurity vs. cyber resilience
Cybersecurity plans ensure organizations are prepared for cyber incidents and can quickly recover and resume critical affected systems and technologies.
But this might not be enough if business operations are affected in the event of a cyber attack. If an attack sabotages mission-critical applications, for example, it might take time to get replacement systems and their associated data in place. Mitigate these kinds of consequences via DR and BC plans. DR plans can help recover disrupted IT assets using a variety of techniques, such as cloud recovery services, data backup facilities, backup copies of critical systems and a supply of spare components. BC plans should support cyber-resilience plans by activating procedures to recover business operations.
Both cybersecurity and cyber-resilience plans should be deployed, documented, periodically exercised, regularly reviewed and updated. They can effectively complement BC and DR plans to create a program that keeps the business operating as usual, despite cyber attacks.






