
Getty Images/iStockphoto
How to use Hashcat to recover passwords
This tutorial and accompanying video on using Hashcat for ethical password recovery covers installation, hash types, dictionary attacks and rule variations for security testing.
Ethical hacking often involves password theft. Red teams, for example, test passwords for policy weaknesses, common password use and password reuse across accounts. Blue teams test passwords for audits, compliance and digital forensics.
In many cases, passwords retrieved by ethical hackers are in an obfuscated format known as a hash, usually as part of a large database of every user on the compromised system or network. To read these passwords as plaintext, hackers need to use a process known as cracking, which requires a lot of processing power.
Many hackers use Hashcat among other password recovery and cracking tools. This easy-to-use tool uses a computer's GPU for resource efficiency and speed.
Follow along in this tutorial to learn how to use Hashcat.
Download and run Hashcat
Download the tool from the Hashcat site and extract it into a directory of your choice.
Launch the tool from the command line by navigating to the directory you extracted it to and typing the following command:
hashcat.exe –help
This populates a list of possible commands, but only a few of them are needed to get started.
How to crack passwords with Hashcat
Open the command prompt and use the following syntax:

The -m denotes the type of hash. Each has a unique code. View them by typing hashcat --help.
The next section of code -- example500.hash -- specifies the file that contains the hashes. This is extracted from whatever system has been breached and placed in the same directory from which you launch Hashcat.
The last part -- example.dict -- specifies the dictionary file. This is a list of common passwords that have been hashed using the same algorithm and compared to the passwords you are trying to crack to see if any of them match.
Using the above example, Hashcat cracked the password hash234. The top line shows the hash followed by the plaintext password.
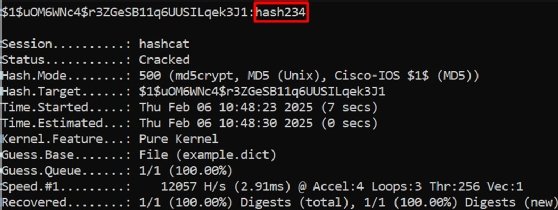
Cracking with Hashcat typically involves conducting dictionary attacks with large files, known as dictionaries, of common words. These dictionaries often include every word in the most-used languages, as well as names, places and any passwords that have appeared in previous data breaches.
Hashcat can run through a dictionary multiple times, adding variations which are known as rules. These automatically add elements, such as numbers and symbols, in certain places. For example, many users put a number at the end of a word to create their password, such as password1.
Rules also make common swaps, such as replacing the letter E with a 3 or a 0 for O. This is because people tend to choose passwords based on predictable words, places or names and put numbers or symbols in certain positions within those words, such as passw0rd. Likewise, many people use a capital letter at the start of their password, such as Password.
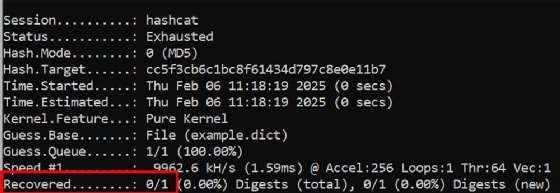
Let's run through an example of the dictionary rules. The default Hashcat syntax used above results in an unsuccessful crack attempt:
Use the following syntax to run Hashcat using a file that contains rules that specify common password variations:
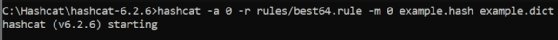
The -a 0 specifies the attack mode, which enables using rules, and the -r specifies the file containing the rules. Rules can be written manually or downloaded, and some are included in Hashcat's default rules directory.
Using the above syntax that enables rules, Hashcat can crack the password Hash234 because one of the rules specified swapping the first letter to uppercase:
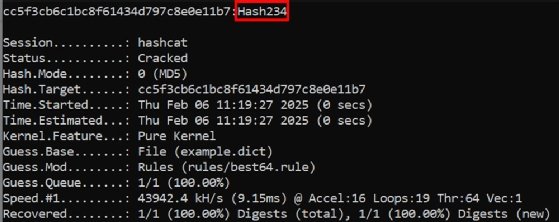
Hashcat is a powerful tool with many more options. These commands show the basic actions needed to crack most passwords for pen testing purposes.
Editor's note: It is possible to use Hashcat lawfully and unlawfully. It is up to you to ensure your usage is lawful. Get appropriate permission and approval before cracking passwords, and handle the information obtained ethically. If you are unsure whether your usage is lawful, do not proceed until you have confirmed that it is -- for example, by discussing and validating your planned usage with your organization's counsel.
Rob Shapland is an ethical hacker specializing in cloud security, social engineering and delivering cybersecurity training to companies worldwide.








