
Alex - stock.adobe.com
Boost security with Office 365 privileged access management
Understand how to thwart cyber attacks on privileged user accounts on Microsoft's collaboration platform to avoid becoming that next security breach statistic.
With great administrative power comes great administrative responsibility.
As more organizations have moved to Office 365, threat actors have also turned their focus to the collaborative cloud platform and attempt to gain admin access to the company's tenant. The centralized admin portal in Microsoft Office 365 manages all aspects of services under the subscription, but anyone with access to the administrative privileges can disrupt the organization. These problems can consist of account locking, disabling services, deleting company data and performing a data breach. With all that potential to do harm, administrators should take the appropriate measures to prevent a doomsday scenario where mishandled privileged access disrupts the organization to cause financial troubles or create legal problems.
For the sake of simplicity, this article will use Office 365 terminology rather than Microsoft 365. There is some confusion as to whether Office 365 still exists or if Microsoft renamed it. These are two distinct products that share many of the same features with the main difference being rights to Windows 10 Enterprise licensing and additional security and management features.
Back to basics: Common intrusion efforts
To lock down Office 365 privileged access management on your tenant, you need to be aware of the three popular methods threat actors employ to gain privileged access.
- Phishing campaign. Hackers send an email to a user with a link that redirects them to a fake Office 365 login page. If they enter their credentials, then the hacker can use them to gain access to the system.
- Trying leaked passwords. It's human nature to use the same password across multiple platforms. Hackers will attempt to sign into Office 365 using a password that was leaked online for other services to see if the targeted user uses the same password.
- Keyloggers and spyware. Another way hackers get access to admin passwords is to steal them from infected machines. If a user who happens to be an admin visits a website or downloads malicious code that installs malware, then the hacker can use a keylogger to collect passwords the user enters for different websites.
Just as there are multiple ways to steal passwords to gain access to the administrative portal of Office 365, there are also several security best practices to protect the tenant from these attacks. Some require very little effort but will impede credential hijacking and mitigate risk.
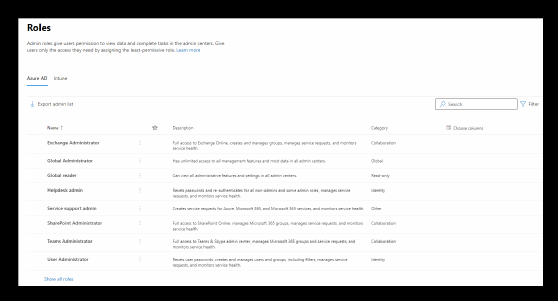
Learn to limit admin privileges based on role
The principle of least privilege states that rights to resources should be minimal and for as short a time as possible. In Office 365, the highest level of access in Office 365 admin portal is the global administrator role. IT should keep tight control over who has this role and understand there are other admin roles with lower privileges that might be enough to manage areas of the platform without giving the highest level of access.
The fewer users with the global admin role, the lower the risk to the organization. IT must define what specific permissions are needed for what services and then assign the proper roles based on those requirements through the least privileged role.
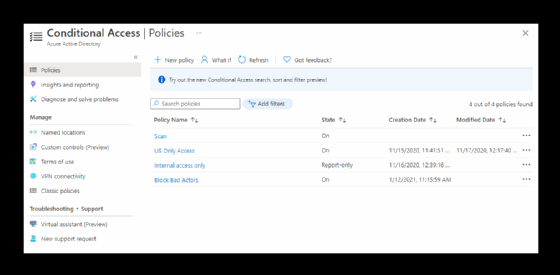
Use conditional access to prevent access by location
Conditional access is another option to reduce remote access attacks to gain access to user accounts with elevated privileges. With conditional access, the organization can block all sign-in attempts or enforce multifactor authentication (MFA) for anyone who tries to connect from another country. Any authentication attempts from known malicious IP addresses or locations known for cyber attacks will be prevented.
Administrators can set specific rules for locations that can authenticate to Office 365 and others that would either be blocked or require MFA. To use this functionality, the organization needs Azure AD Premium Plan 1 or 2 licensing for the Office 365 tenant.
MFA should be a requirement for users with admin rights
While it is recommended for every user in the organization to be verified with MFA, it should be mandatory for anyone in the IT team with elevated rights in the Office 365 portal. This extra layer of security will help prevent an intrusion if the first line of defense fails.
MFA for administrators is the first step to adopt stronger protections on Office 365. MFA ensures that when a user with elevated permissions signs into the portal, they have been verified with a certain degree of certainty. MFA is an option for all Office 365 plans and does not require the purchased of any additional security service or add-on.
Consider Microsoft's Privileged Access Management
Another security option that some IT administrators are adopting is the use of Microsoft Privileged Access Management (PAM). This feature is included with Office 365 Enterprise E5 and Microsoft 365 E5 subscriptions; for other subscriptions, you can purchase it as an add-on.
With PAM in Office 365, IT allocates temporary elevated access to users. PAM gives just-in-time access and just-enough-access. Using PAM ensures that no one user has admin privileges for an extended period, and a manager or supervisor reviews the access by before it is granted. This approach gets the organization prepared to implement zero standing privileges while it supports the requirements to administer the systems as needed.
The trend of security breaches that originate from leaked admin credentials means more companies should try to implement system protections and processes around who has admin privileges and for how long. If elevated permissions are only used by the appropriate users and also are taken away when they are not needed, then organizations can concentrate on other security areas to tighten protections and avoid being another cyber attack statistic.






