
Getty Images/iStockphoto
How to manage dependency risk in third-party ad tech
Ad tech risk management is now vital for IT, not just marketing. Organizations must address third-party code risks to protect their brand's performance, security and compliance.
Modern digital advertising relies on a complex web of third-party code, real-time actions and data-sharing services that few organizations fully understand or map end to end.
A single page load can trigger a cascade of tags, pixels, JavaScript libraries, iframes and server-side calls across various platforms for different teams. That complexity creates an ad tech supply chain where performance and risk are inseparable, and third-party ad tech dependencies can silently become production dependencies.
Now, ad tech risk management is becoming an IT responsibility, not just a marketing concern. Marketing teams may select and operate platforms, but IT leaders handle site reliability, security controls, incident response and data privacy compliance. When third-party ad tech dependencies run in the browser on high-traffic pages, they become production dependencies. They can slow the site, break page functionality, expand the attack surface or create unapproved data flows.
Recent security events show why this cannot be treated as a low-risk add-on:
- In 2024, the Polyfill.io supply chain compromise demonstrated how bad actors could alter a widely used third-party script source after ownership changes, exposing any site that still referenced it.
- In 2025, Microsoft reported a large-scale malvertising campaign it detected in December 2024, where redirects from illegal streaming sites led users to malware hosted on platforms, including GitHub. Attackers used multiple ad networks to spread malware to Android users, showing how bad actors can use the ad ecosystem as a distribution channel when controls fail upstream.
Third-party ad tech dependency risk tends to show up as a chain reaction. A tag or vendor issue can start as a marketing tech problem, but quickly become a site reliability incident, a security investigation or a compliance problem.
With the right governance and technical controls, organizations can maintain high marketing performance while reducing risk exposure across the ad tech stack.
Understanding third-party dependency risk in ad tech
In ad tech, third-party dependency risk refers to the potential for externally managed code or services to harm the business through performance regressions, security exposure, compliance gaps, operational downtime or brand damage. It includes everything the marketing organization adds to digital properties to acquire, measure and monetize audiences.
For CIOs and enterprise architects, ad tech risk management should start with a shared vocabulary across IT, security, marketing and legal teams.
The following categories represent the most common ways risk manifests.
Technical performance risk
Third-party scripts can slow down pages, as they add network requests, consume main-thread browser time and increase the likelihood of tag conflicts. Even well-optimized first-party code can be hindered by third-party JavaScript that loads late, loads inconsistently or works excessively during page interaction. Industry guidance and independent measurement both flag third-party scripts as a frequent cause of poor UX metrics.
Security risk
Any third-party script establishes an external trust relationship within the user's session. If a bad actor compromises a vendor or a dependency in its supply chain, malicious code can reach production pages without being deployed by the organization. The Polyfill.io compromise shows how a single shared script source can become a supply-chain event for many unrelated organizations.
Privacy and compliance risk
Ad tech often touches identifiers, cookies, device signals and behavioral data. Risk emerges when tags fire before consent, when consent settings are misconfigured, or when vendors collect more data than the business intended.
This is where data privacy compliance depends on technical enforcement, not just policy. If the consent model and tag model don't align, compliance gaps can appear quietly and persist for months.
Operational risk
Vendors have outages. They also push changes that can alter behavior, endpoints or data collection patterns. Google's own status reports show that even major platforms can experience multi-day incidents, and CIOs must plan for that risk in their monitoring and contingency playbooks.
Reputational risk
Customers tend to judge the brand, not the vendor, when pages break, performance degrades or data handling feels intrusive. Reputational risk also includes the downstream effects of the ad ecosystem itself, including user distrust and scrutiny from regulators or partners when the organization cannot explain what third parties do on its pages.
Governance models for ad tech dependencies
Governance for third-party ad tech dependencies works best when it resembles a streamlined version of third-party risk management, rather than a one-off marketing process. It should help marketing teams move quickly, while making sure every new tag, pixel or integration meets business standards for security, privacy, reliability and support.
A risk-based approach is important because not every tag carries the same exposure. Some simply measure page views. Others can access user identifiers, collect form data or open outbound connections to dozens of partners.
A practical model starts with shared ownership across four functions:
- Marketing and marketing technology teams own business intent, use cases and vendor selection.
- IT and enterprise architecture teams own implementation patterns, performance standards and change control.
- Security teams own third-party access risk, monitoring expectations and incident response alignment.
- Legal and privacy teams own data processing terms, consent requirements and compliance obligations.
An ad tech governance playbook should be a living document that defines how the organization onboards, reviews and retires ad tech. It should be short enough to use, but specific enough to enforce.
A strong baseline includes the following criteria:
- Approval workflow for new tags. Require a short intake and risk-tiered review so teams can't deploy higher-risk scripts without approval from the security and privacy teams.
- Periodic script audits. Run recurring audits to inventory tags, remove redundancies, retire unused vendors and confirm that consent and data flows still match the approved use case.
- Standardized contract language and service-level agreement expectations. Standardize terms for uptime, support, change notifications, security controls and subcontractor disclosure so external dependencies have enforceable expectations.
- Data minimization standards. Define what data can be collected, what is prohibited and what requires escalation, so tags capture only what is needed for the stated purpose.
- Breach and incident notification requirements. Set notification timelines and escalation paths, so security teams are informed quickly and can coordinate a response across groups.
With this playbook, IT governance for marketing technology becomes repeatable and measurable, and it creates a clean handoff to the technical controls that reduce day-to-day dependency risk.
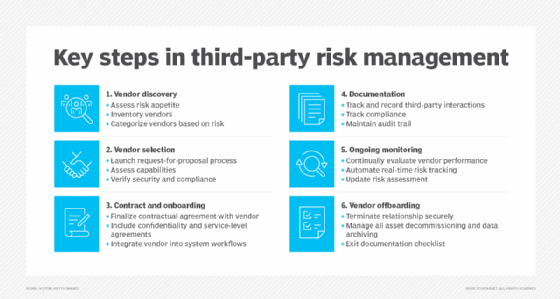
Technical controls to reduce risk
Once a governance model exists, IT teams can automate risk reduction through tooling and guardrails, without relying on someone to remember a checklist.
The most effective technical controls, listed below, focus on two components: limiting what third-party code can do, and simplifying problem detection and quick rollback when something changes.
Tag managers and container governance
Tag management best practices start with treating the tag manager like production code:
- Limit publish rights.
- Require approvals.
- Separate development and production workflows.
- Reduce or eliminate unrestricted custom HTML tags unless they are reviewed like any other code change.
Role-based access and strong authentication controls are easy wins, because they directly reduce the chance of an accidental or unauthorized tag going live.
Real-time script monitoring and rollback
Organizations should monitor third-party behavior in real user sessions, including which vendors load, the latency they introduce and whether errors spike after tag changes.
Teams should also have a rollback path that does not require a full site deployment. Third-party performance monitoring can help isolate which dependency causes regressions when marketing, analytics and ad services all change frequently.
Sandbox environment for vendor tags
IT teams should test high-risk tags in a controlled environment that mirrors production pages and consent behavior, so teams can validate performance, confirm data flows and observe unexpected downstream calls before release.
Limit permissions and isolate risky scripts
Browser controls like Content Security Policy can reduce exposure, restrict which script sources can run and narrow where data can be sent. These limits help contain the effect of a compromised or misbehaving dependency.
Integrity checks for third-party resources
Where feasible, security features like Subresource Integrity can ensure that a fetched script matches an expected version, providing a practical control against third-party resources that should not change silently.
Content delivery networks, failover and performance budgets
Organizations should include third-party limits in their site performance budgets, then enforce them with automated alerts and removal workflows when budgets are exceeded. This prevents tag bloat from becoming a long-term drag on digital experience.
Resilience in an evolving regulatory environment
Data privacy compliance is a moving target because requirements vary by jurisdiction, and enforcement is increasing, especially around tracking and cookie consent. For many organizations, that means operating against a patchwork of U.S. state laws plus stricter expectations in the EU. Privacy teams need a reliable way to track what changes and when they become enforceable.
At the same time, the third-party cookie roadmap remains unsettled. In April 2025, Google said Chrome would not introduce a new standalone prompt for third-party cookies and would maintain its current approach, while continuing work on other tracking protections and Privacy Sandbox-related efforts. That uncertainty increases dependency risk because identity, measurement and attribution vendors can change behavior quickly in response.
Resilience comes from treating consent and data controls as architecture:
- Keep a clear record of which tags collect what.
- Enforce consent signals consistently.
- Reduce vendor data access to what is required.
- Review high-impact ad tech decisions alongside broader risk management priorities.
Future-proofing the ad tech stack
Future-proofing starts with a clear vendor strategy. Consolidation can reduce complexity and shrink the attack surface, but it also increases concentration risk if one platform outage or policy change takes down a critical workflow.
The most durable approach is to standardize on a small set of core vendors, then maintain swap-ready alternatives for the few functions that are revenue-critical or high-risk: identity, measurement and ad serving. Ad tech M&A activity has remained active, which is another reason to plan for vendor churn and product consolidation.
AI is also reshaping ad delivery and campaign operations, including targeting, creative generation and optimization. That adds a new class of failure modes, such as off-brand outputs, brand integrity issues and decision logic that is harder to explain during audits or incidents, which makes governance and monitoring non-negotiable.
From an architectural standpoint, resilience comes from modular design:
- Isolate tags.
- Minimize data shared by default.
- Document dependencies.
- Make it possible to disable or replace a vendor without rewriting the site.
Griffin LaFleur is a MarketingOps and RevOps professional working for Swing Education. Throughout his career, LaFleur has also worked at agencies and independently as a B2B sales and marketing consultant.








