IT audit (information technology audit)
What is an IT audit (information technology audit)?
An IT audit is the examination and evaluation of an organization's information technology, operations and controls.
What does an IT audit do?
Information technology audits determine whether IT controls protect corporate assets, ensure data integrity and are aligned with the business's overall goals. IT auditors examine not only logical and physical security controls but also overall business and financial controls that involve information technology systems.
Because operations at modern companies are increasingly computerized, IT audits are used to ensure information-related controls and processes are working properly. The primary objectives of an IT audit include the following:
- Evaluate the systems and processes in place that secure company data.
- Verify that IT controls are being regularly practiced and maintained.
- Determine risks to a company's information assets and identify methods to minimize them.
- Ensure information management processes are in compliance with IT-specific laws, policies and standards.
- Determine inefficiencies in IT systems and associated management.
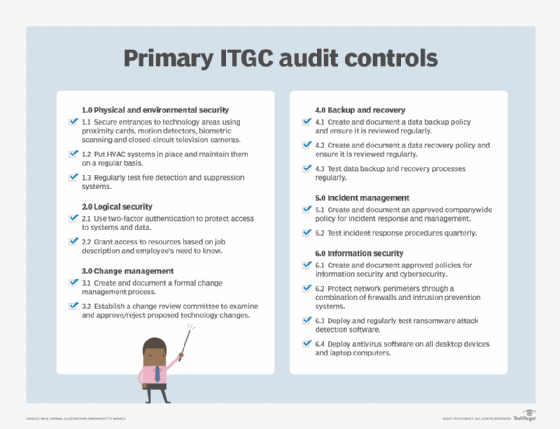
Why are IT audits important?
Considering how complex information systems and operations are today, IT leaders want to demonstrate that their IT infrastructures are running smoothly, performing according to business processes and expectations, minimizing cybersecurity threats, and in compliance with standards, regulations and other requirements.
Periodic audits ensure an IT organization is following accepted standards, best practices, regulations, legislation and other requirements. IT audits provide important evidence of such compliance to an organization's customers as well as regulatory and government agencies.
Audits are also beneficial because auditors are considered independent of the IT organization and are expected to examine controls carefully and impartially, identifying what is working and what is not, reporting their findings and providing recommendations for remediation. Savvy IT leaders recognize the importance of periodic IT audits as an important benchmark for validating what is working and what is not meeting expectations.
Who needs an IT audit?
Virtually any IT organization can benefit from periodic IT audits because they provide an independent assessment of how well IT systems are being managed, how their security resources are performing and how well IT controls are being handled. Audits can examine general IT controls or focus on specific attributes such as cybersecurity and environmental management.
What happens in an IT audit?
An IT audit uses a framework of general controls in several areas such as access control, physical access security cybersecurity, environmental management, risk management, operational performance, emergency response and disaster recovery. Auditors examine how well the IT organization complies with the aims and requirements associated with each control. They collect evidence in support of the controls and of how they are performed. In situations where a control is not being performed or is not being performed properly, auditors compile those findings into an audit report that lists the findings and recommended remediations. The report often includes an agreed-upon timeframe for resolution of the findings.
An IT audit generally has these steps:
- Secure approval. Senior management must approve the audit and its funding.
- Create a plan. Identify IT elements to audit and types of controls to examine as well as audit scope, objectives and timeframes.
- Start preparations. Determine who will perform the audit. It may be an internal IT audit team, the company's internal audit department or a third-party audit firm experienced in IT auditing. These are referred to as first-party, second-party and third-party audits respectively.
- Secure a work area. This can be a conference room set up for the audit team where they can conduct interviews, examine evidence received from the IT department and prepare audit work papers.
- Launch the audit. Brief the IT department team on audit discovery processes, expectations, timeframes, evidence types and interview schedules.
- Prepare work papers. These may be interview notes, computer screenshots, policy documents, procedures, various reports, prior audit reports and other relevant materials.
- Prepare and deliver the audit report. An audit report summarizes the controls examined, evidence obtained, analysis of IT department compliance with the controls, areas where controls were not achieved, and recommendations for mitigating deficiencies. The report usually has a proposed timeframe for remediating deficient areas.
The value of a certified IT audit professional
When preparing for an IT audit, it may be useful to ask if at least one of the auditors -- especially in an outside audit firm -- has an IT audit certification. One widely accepted IT audit credential is the Certified Information Systems Auditor (CISA), available from ISACA. CISA-certified professionals must pass a rigorous exam to obtain the designation and must annually submit evidence of continuing education and participation in relevant activities and organizations.
See six controls you need to address during an IT general controls audit, and learn how to conduct an internet of things audit for compliance. Explore best practices for backup audit preparation.






