
Gorodenkoff - stock.adobe.com
Edge data protection tips and tricks
Edge computing is on the rise, and more IT teams are looking for ways to protect decentralized data. Our experts look at some ways to protect and store data generated at the edge.
Organizations now generate and process data in edge environments at higher volumes than ever before.
Tech research and advisory firm IDC estimated that 55.9 billion connected devices will generate more than 79 zettabytes (ZB) of data by 2025, up from 13 ZB in 2019. With an increase in work-from-home (WFH) structures and continued growth in data generated by IoT devices, edge data protection and storage of edge data continues to be a challenging area for IT teams.
Here are some tips from experts on how to properly protect, store and back up edge data.
Account for the increased risk edge computing brings
Edge computing, especially when supporting multiple IoT devices, can increase the potential attack surface for in-house or outside malicious attackers. Because edge devices operate outside of the central data center, their deployment can weaken the physical and network protection that devices within the data center have, according to Tom Nolle, president of CIMI Corporation.
Nolle conversely noted, however, that edge computing can benefit network security by providing local encryption. In addition, organizations that route their traffic to a company VPN can "improve monitoring and control of security."
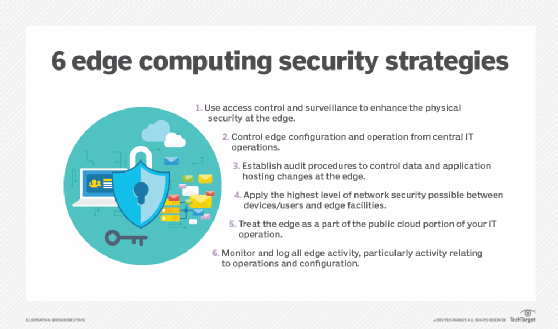
Organizations that want to employ edge data protection strategies can turn to several practices. Nolle recommended that the organization, as opposed to local personnel, should oversee edge configuration, log all edge activities, establish audit procedures to control data and application hosting changes, and fully secure the network connection to the edge. This can prevent "careless password control and operating errors," Nolle said.
IT departments can further ensure edge data protection by encrypting data and deploying firewalls and antimalware, according to technical consultant Robert Sheldon. IT teams can also implement intelligent storage devices to automize protection but should also monitor activity across all edge systems.
Craft edge data protection and storage plans for security and efficiency
Sheldon said there are certain actions all organizations should take when they manage or plan for storage at the edge and edge data protection. Consider the amount of data the organization generates, ensure data is encrypted at rest and in motion, and set up facilities and infrastructure to work within the constraints of an organization's bandwidth. Research edge storage systems -- such as fog computing, micro data centers and hyper-converged edge systems -- to determine which systems work best based on edge data protection and backup needs.
Different edge systems offer different capabilities, and organizations can adopt systems based on latency, scalability and storage requirements. For example, organizations that have larger edge workloads may turn to hyper-converged edge systems, which are easily deployable, while organizations running applications that cannot tolerate latency may turn to IoT gateways for IoT networks.
Organizations that have limited facility space can use computational storage to move processing to the storage system itself and alleviate some of the burden off of compute resources, Sheldon said. SSDs may be a better choice for smaller spaces instead of HDDs because they require less space, power and cooling.
Organizations with network bandwidth limitations can send only "cleansed and aggregated data" to a central repository, which can lead to better application performance. But organizations must also consider latency and may need to invest in higher-performing devices or intelligent storage technologies to "reduce administrative overhead."
Adjust edge storage practices for WFH models
Before the COVID-19 pandemic, roughly 20% of American workers worked from home, according to a Pew Research Center study published in December 2020. At the time of publication, 71% of respondents were working remotely -- a 355% increase from before the pandemic.
Employees working from home may become inclined to store their data directly on their device's hard drive, when they may have previously stored that data on an enterprise file server or in the cloud, according to technical writer and Microsoft MVP Brien Posey. However, many organizations do not install backup agents on personal devices, which leaves decentralized data susceptible to loss if a user's device gets compromised, or if their device's storage hardware becomes damaged.
There are numerous ways for organizations to properly back up and store user data. For example, use file sync-and-share software and then back up the contents of the shared data, Posey said. Have users save data in a specific location, and back up files that users save to that location.
With remote and hybrid working models likely to continue and even grow, it is important for organizations to educate users to recognize phishing attempts, which account for 90% of ransomware attacks, according to Veeam CISO Gil Vega. Give yourself a fighting chance to keep malicious attackers looking to encrypt, copy or steal data via edge devices from succeeding, Vega said.
Look inward and integrate edge into an overall storage strategy
Data storage can be difficult enough at the enterprise level, but producing data at the edge simultaneously produces more storage, security and backup needs. Take steps to determine how to incorporate edge data protection, storage and backup into an organization's overall strategy.
Sheldon said CIOs and other decision-makers within organizations should ask themselves a series of questions before implementing edge and multi-cloud environments. Learn how much data is generated, how long to retain data, how data will be moved from edge systems to other storage environments and how to plan disaster recovery strategies for the new systems or multi-cloud environments.






