What is a configuration file?
A configuration file, often shortened to config file, defines the parameters, options, settings and preferences applied to operating systems (OSes), infrastructure devices and applications in an IT context.
Software and hardware devices can be profoundly complex, supporting myriad options and parameters. In configuration files, IT and system administrators explicitly delineate appropriate settings and choices for their specific data center, cloud or user environment.
For example, a configuration file could specify where to store log files from an application via the storage path, which plugins are enabled in a given program, and color scheme and dashboard widget preferences for a user interface (UI).
How do configuration files work?
At start time, the application or other system opens, reads and parses the configuration file and applies each setting. Configuration options can be changed while the application runs, taking effect immediately or upon restarting when the configuration file is reread.
IT environments can use either a single or multiple configuration files for different system components. For example, a complex application might use separate configuration files for UI settings, network and storage parameters, and other aspects that must be set up for operation. However, using multiple configuration files can introduce management difficulties.
Configuration file formats and syntax
Plaintext configuration files used in Linux and Unix-based environments have extensions such as CNF, CONF, CFG, CF and INI. Early command-line OSes such as MS-DOS relied on a single plaintext configuration file with a SYS extension. Common modern configuration filename extensions depend on the prevailing file format or use CONFIG.
Some configuration files are meant to be human-readable, using plaintext formats compatible with any common text editor. The scripting language PHP uses a plaintext file named php.ini, and Microsoft Windows uses the desktop.ini file to configure how a folder is displayed.
Configuration files have largely adopted serialization formats such as XML, YAML and JSON to represent complex data structures in a way that is easily stored and parsed. Each file format has its nuances and permissions, so it's important to understand their specifics. For instance, when working with JavaScript, many programmers prefer to use JSON for configuration files.
The resulting filenames reflect this format -- for example, myapplication_configuration.yaml. With this setup, administrators can identify a modern configuration file by its name rather than its extension.
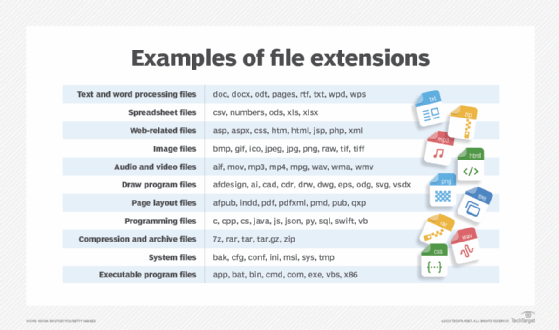
Types of content in configuration files
Configuration file content is often specific to the corresponding application or system but generally falls into one of the following types.
Comments
Comments are essential to configuration files but do not affect how the file behaves. Developers use comments to communicate intended behaviors and document important actions.
For example, the .ini file format uses hash symbols and semicolons to mark comments:
# This is a comment in a typical .ini fileFlags
Flags control which options are enabled and disabled in an application or system. Flags can be enabled with the numeral 1 or the word true and disabled with the numeral 0 or the word false.
For example, the following code from an Ansible configuration file uses True to mark a flag related to temporary files.
; allow temp files to be world readable
allow_world_readable_tmpfiles = TrueIn the following example, the configuration file specifies whether the name of each task appears in the standard output.
; do not send task labels to the display
display_args_to_stdout = FalseSettings
Settings assign constants to variable information, which enables the application to define operational parameters.
For example, an application might use the variable server to define the IP address of the application server and the variable port to define the communication port used by the server at the designated IP address:
; set the IP address and port for the application server
server = 192.1.2.62
port = 144Paths
Applications routinely access locations to load or save important information, such as log files or plugins. Although default locations exist, it is common to stipulate storage devices and folder locations via paths and specific filenames. The application uses the preferred paths denoted in the configuration file.
The following example shows a path describing the drive and folder containing a configuration file named dbsettings.ini.
; location of the database config file
database_setup = "c:\\programs\\new\\dbsettings.ini"Similarly, developers and administrators can use paths to delineate desired filenames. For example, a classic config.sys file can stipulate the location and name of the desired UI shell.
; the location and name of the UI shell in MS-DOS 5
shell = c:\dos\command.comKey-value pairs
Key-value pairs represent a simple way to store and retrieve configuration settings as pairs. Each key-value pair consists of a unique identifier (the key) and its associated value, which can be a string, number or other data types. The key-value pair is separated by either a colon or an "equals" sign.
For example, a key-value pair might appear as follows in a configuration file.
default_directory = /home/user/documents.Annotations
Along with comments, some configuration files can contain annotations -- metadata about the settings, including details such as when a setting was last modified, who made the change and what the reason for the change was.
Benefits of using configuration files
Configuration files boost the functionality, flexibility and manageability of software management systems. Key benefits of configuration files include the following:
- Separation of concerns. Configuration files enable developers to separate application logic from configuration settings. This separation makes it easier to manage and modify the settings or behavior of a program without altering the codebase.
- Improved security. Sensitive information, such as API keys and database credentials, can be stored securely in configuration files or environment variables, reducing the risk of exposing sensitive data in the code.
- Ease of customization. Users can easily customize application behavior by modifying configuration files. This flexibility is particularly useful in different environments where settings can vary, such as development, testing and production.
- Enhanced deployment and scaling. Configuration files simplify the deployment and scaling of applications. By keeping configuration data in separate files, administrators can quickly modify an application's behavior as it transitions from development to testing and then finally to production. This approach also facilitates scaling across multiple servers or environments, enabling each application instance to maintain its own configuration file.
Working with configuration files
People use various tools to create and edit different configuration files. Tools can help users find parameters within the file, convert to a different file format and accomplish other tasks.
Text editors such as Microsoft Windows Notepad and Linux GNU nano are some of the most common tools for editing human-readable files. Some text editors provide search and pattern-matching features to help users find and change content.
Other tools specialize in certain file formats. For example, JSON Editor Online for JavaScript is used to create and edit files in the JSON format, and Swagger Editor can convert YAML files to JSON. Additional editors exist for formats such as XML and TOML.
Best practices for managing configuration files
IT teams managing configuration files should set up a system of comments, testing, version control and backups.
The following best practices should be followed for configuration file management:
- Use comments to document important activities taking place within the file and write them in a way that others can understand.
- Test configuration files thoroughly to ensure that the application or system works as intended.
- Adopt a naming or version control convention that enables configuration file editors to track changes made over time, such as the introduction of a new path for storage and see who made those changes.
- Treat configuration files as critical and include them in backup schemes.
- Review and modify default security settings in configuration files as these settings can often be weak and might expose the application to vulnerabilities.
- Avoid using configuration files that are also executable, as this can create security risks and complicate configuration management.
- For applications with multiple instances or environment variables, a centralized configuration management system is recommended to maintain a single source of truth, simplifying changes across environments.
Discover how Puppet helps organizations manage configurations and streamline the DevOps process. Find out if it's the right fit for your needs.







