
Gorodenkoff - stock.adobe.com
10 advanced incident response strategies for ITOps
Learn how to upgrade your incident response strategy with 10 advanced techniques that transform reactive security into proactive, resilient defense.
As organizations increasingly adopt third-party integrations, cloud services and hybrid models, their IT infrastructure becomes more challenging to protect. Traditional incident response strategies, while foundational, fall dangerously short of addressing complex threats and vulnerabilities. To stay ahead of the evolving risks, organizations must move beyond reactive measures and take a proactive, resilient approach to incident response.
This article presents 10 advanced strategies IT operations teams can use to transform incident response frameworks, equipping organizations to detect, contain and recover from threats more effectively.
Understanding incident response basics
Incident response is a structured approach to detecting, containing and recovering from cybersecurity threats, such as data breaches, malware infections and unauthorized access. The primary goals of an incident response strategy include the following:
- Minimize damage to systems, services and data.
- Maintain business continuity by limiting service disruptions.
- Reduce recovery time and associated costs.
- Preserve evidence for legal or regulatory purposes.
Building an incident response plan
An incident response plan should incorporate several baseline strategies to ensure readiness and resilience:
Prevention and protection
- Establish security baselines with regular updates.
- Deploy zero-trust network segmentation to prevent lateral movement during attacks.
- Develop risk mitigation playbooks for supply chain vulnerabilities and third-party risks.
Detection and analysis
- Use AI-based event detection to enhance threat identification and containment.
- Safeguard communications for incident management.
Recovery and continuity
- Maintain backup and restore processes combined with data redundancy to protect critical information.
- Design recovery sites (hot, warm, cold) tailored to business needs.
10 advanced incident response strategies
Beyond basic protocols, the following advanced approaches transform reactive security into proactive defense, building truly resilient environments.
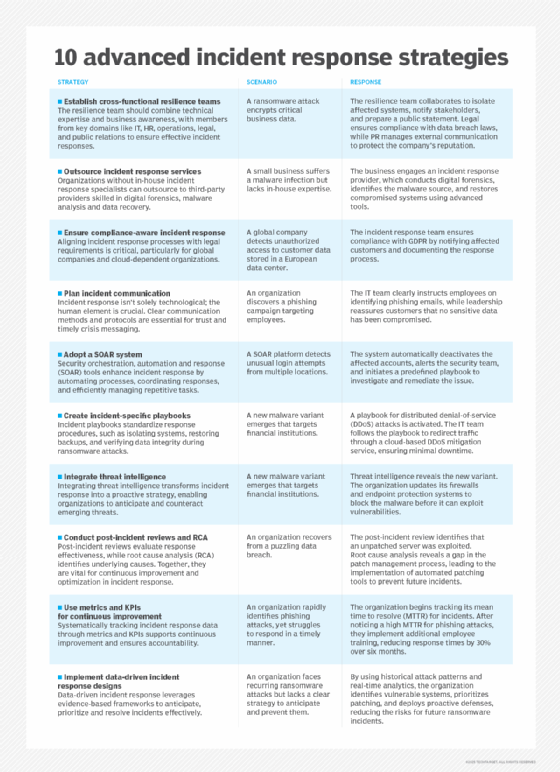
1. Form cross-functional resilience teams
Creating teams that combine technical expertise with business acumen can provide comprehensive incident responses. Members should represent key organizational domains, such as IT, human resources, operations, legal and public relations.
Key benefits include the following:
- Informed decision-making. Diverse perspectives align technical and business priorities.
- Thorough post-incident analysis. The team evaluates an incident's effect across domains for improved preparedness.
For example, during a ransomware attack, a cross-functional resilience team might respond in the following ways:
- IT. Isolates the affected systems and initiates recovery.
- HR. Communicates preventative guidelines to employees.
- Operations. Ensures business continuity by reallocating workloads.
- Legal. Advises compliance and ransom-related decisions.
- Public relations. Manages external communication to protect the company's reputation.
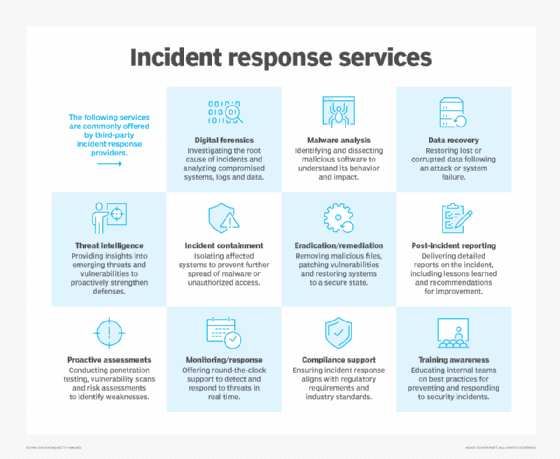
2. Outsource incident response services
Organizations lacking in-house incident response specialists can benefit from outsourcing to third-party providers. These providers offer expertise in digital forensics, malware analysis, data recovery and other areas.
Key benefits include the following:
- Access to expertise. Providers employ seasoned professionals and advanced tools.
- Cost efficiency. Small and medium-sized businesses can avoid the expense of maintaining full-time experts.
- Flexibility. On-demand services reduce pressure on internal teams.
3. Ensure regulatory and compliance-aware incident response
Organizations should align incident response processes with legal requirements, especially global companies and those relying on cloud services.
For example, a multinational e-commerce company that experiences a data breach involving customer information stored across multiple countries ensures compliance by collaborating with legal advisors. The incident response team tracks data locations to avoid sovereignty violations, notifies affected customers within required timeframes and reports the breach to relevant authorities, adhering to regulations like GDPR in Europe and CCPA in California.
Key benefits include the following:
- Data location awareness. Teams track data to prevent sovereignty violations.
- Penalty mitigation. Compliance-focused strategies reduce the risk of fines and reputational damage from mishandled data.
- Customer trust. Adherence to regulations builds confidence among customers and stakeholders.
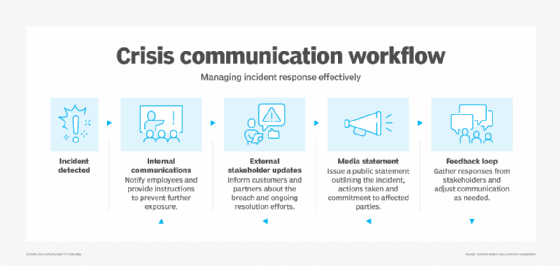
4. Plan incident communication
Not every aspect of incident response involves technology. The human element is just as critical. Clear communication methods and protocols are vital for maintaining trust, reducing uncertainty and facilitating timely messaging during a crisis.
Key benefits include the following:
- Trust preservation. Transparent and consistent messaging reassures stakeholders, including employees, customers and business partners.
- Reduced panic and confusion. Clear communication protocols help mitigate fear and prevent misinformation so that everyone involved understands the situation and their role in the response.
- Improved coordination. Strategic messaging can accelerate decision-making and the deployment of resources, such as personnel, hardware, funding and third-party partners.
- Enhanced reputational management. Proactive communication with external audiences, including the media, demonstrates accountability and professionalism, helping to protect the organization's public image.
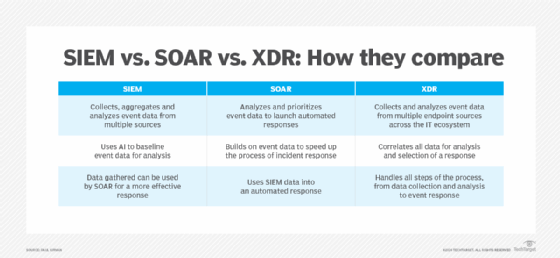
5. Adopt a SOAR system
Security orchestration, automation and response (SOAR) platforms extend automation benefits to incident response. These tools and frameworks enable organizations to streamline processes, coordinate responses and handle repetitive tasks efficiently.
Key benefits include the following:
- Process standardization. SOAR tools rely on effective playbooks to facilitate consistent responses across incidents.
- Efficiency. Automation reduces response times and minimizes human error in repetitive tasks.
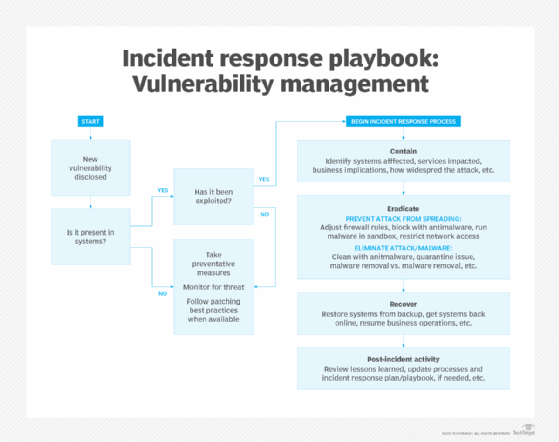
6. Create incident-specific playbooks
Incident playbooks standardize your organization's procedures for responding to various incident types. For example, a ransomware attack playbook might include steps to isolate affected systems to prevent the ransomware from spreading across the network and instructions for restoring systems from backups, decrypting files and verifying the integrity of restored data.
Key benefits include the following:
- Preparedness. Defining procedures in advance prepares teams to act during a complex crisis.
- Accountability. Clear roles and responsibilities outlined in playbooks make it easier to coordinate teams.
- Customization. Playbooks can be adapted to meet regulatory requirements, cybersecurity protocols or public relations needs.
7. Integrate threat intelligence
Integrating threat intelligence into incident response processes transforms them from reactive to proactive. For instance, by using real-time intelligence feeds, an organization can detect unusual activity patterns that indicate a potential phishing campaign targeting its employees. This enables the security team to prioritize the threat, implement preventative measures such as blocking malicious domains, and educate employees on recognizing phishing attempts -- all before attacks escalate.
Key benefits include the following:
- Proactive threat detection. Real-time intelligence enables organizations to identify emerging threats and vulnerabilities before they escalate.
- Improved decision-making. Access to actionable threat intelligence supports informed decision-making during incident response, enabling teams to focus on the most critical threats.
- Stronger collaboration. Sharing threat intelligence across teams and organizations strengthens collective awareness and fosters continuous improvement.

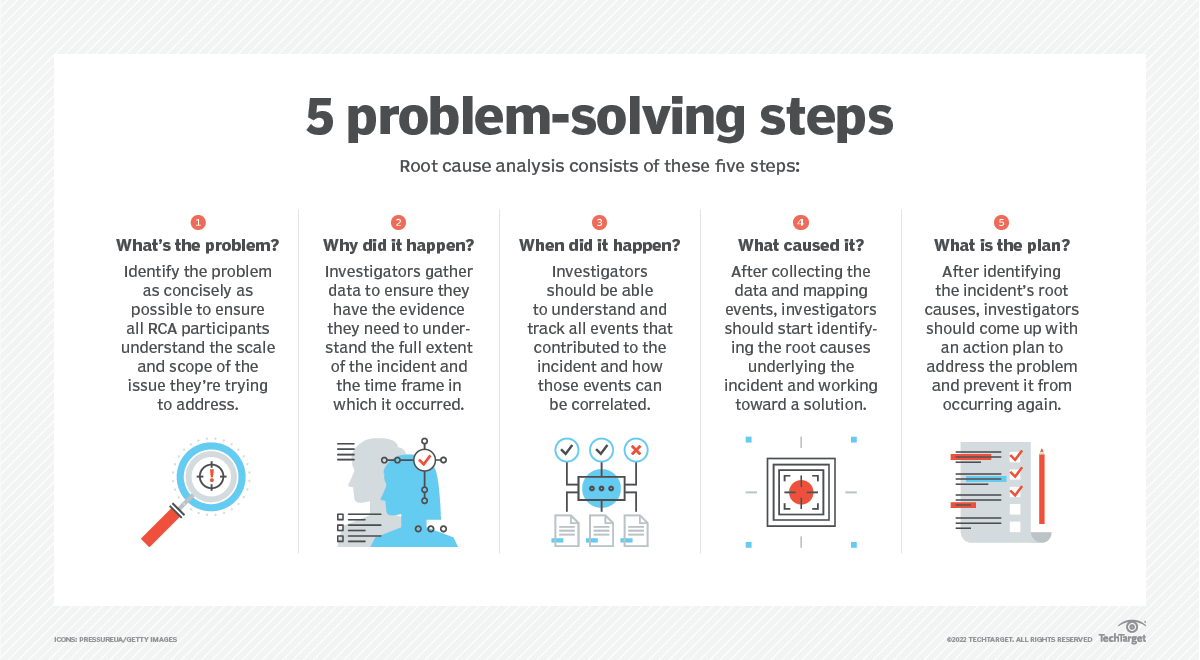
8. Conduct post-incident reviews and root cause analysis
Post-incident reviews evaluate an organization's response to a specific incident, while root cause analysis (RCA) systematically identifies the underlying factors that led to the event.
For example, after resolving a security breach, an incident response team conducts a review to assess the effectiveness of its actions. The team discovers that communication delays affected response time. Through RCA, the team determines that unclear escalation protocols and gaps in training caused the delays. This insight leads to updated procedures and targeted training sessions, ensuring faster and more coordinated responses in the future.
Key benefits include the following:
- Learning opportunities. Teams gain insights into what worked well and what needs improvement, fostering a culture of growth and resilience.
- Identification of root causes. RCA reveals the fundamental reasons behind incidents, such as process failures, human errors, security gaps or unanticipated vulnerabilities, enabling targeted mitigation strategies.
- Prevention of recurrence. Organizations can use RCA insights to shape new measures that prevent similar incidents in the future.
- Improved team collaboration. Post-incident reviews promote open discussion among team members, strengthening communication and coordination for future responses.
9. Continuous improvement via metrics and KPIs
Systematically tracking incident response data through metrics and KPIs drives continuous improvement and accountability.
For instance, by monitoring mean time to detect (MTTD) and mean time to resolve (MTTR), an organization identifies that the detection times for specific incidents are longer than expected. Further analysis reveals that outdated monitoring tools are contributing to the delay. With this insight, the organization upgrades its tools and provides additional training for its response team, resulting in faster detection and resolution times.
Common metrics include the following:
- Mean time measurements. Including MTTD, mean time to acknowledge and MTTR.
- Incident volume. The total number of incidents handled.
- First touch resolution. The number of incidents resolved on the first attempt.
- Ticket reopen rates. The frequency of incidents resolved on the first attempt.
- System, service and network uptime. The availability and reliability of critical infrastructure.
- Customer satisfaction survey results. Feedback from customers on incident handling and resolution.
Key benefits include the following:
- Realistic goal setting. Establishing baselines and defining targets helps organizations set achievable expectations and measure progress.
- Identification of weaknesses. Metrics pinpoint areas of vulnerability or inefficiency, enabling focused improvements.
- Accountability and auditing. Progress tracking ensures teams remain accountable and provides evidence for audits and compliance reviews.
10. Implement data-driven incident response designs
Data-driven incident response designs use evidence-based frameworks to anticipate, prioritize and resolve incidents efficiently.
For example, a security operations center (SOC) analyzes historical data to identify patterns of incident types. The data reveals that phishing attempts spike during specific times of the year, such as tax season. The SOC responds by implementing proactive measures such as targeted employee training and enhanced email filtering during high-risk periods.
Key benefits include the following:
- Systematic decision-making. Data-driven designs rely on metrics and KPIs, ensuring responses are guided by factual evidence rather than assumptions or incomplete information.
- Improved incident prioritization. Historical data and trends analysis enable organizations to prioritize incidents based on their potential impact and urgency.
- Enhanced preparedness. Evidence-based frameworks help organizations prepare for a broader range of incident types, including those that are difficult to predict.
- Continuous optimization. Integrating data-driven designs into continuous improvement initiatives ensures that incident response processes adapt to emerging threats and evolving organizational needs.
Upgrading an organization's incident response strategy
A foundational incident response plan is a great starting point, but building on it with advanced measures is crucial to staying ahead of evolving threats.
By incorporating automation, AI, enhanced communication protocols, compliance-focused processes and incident-specific playbooks, companies can proactively strengthen their preparedness for complex events. These enhancements minimize downtime and service interruptions while ensuring a more resilient and efficient response to future challenges.
Damon Garn owns Cogspinner Coaction and provides freelance IT writing and editing services. He has written multiple CompTIA study guides, including the Linux+, Cloud Essentials+ and Server+ guides, and contributes extensively to Informa TechTarget, The New Stack and CompTIA Blogs.








