SIEM vs. SOAR vs. XDR: Evaluate the key differences
SIEM, SOAR and XDR each possess distinct capabilities and drawbacks. Learn the differences among the three, how they can work together and which your company needs.
Managing cyberthreats is one of the most important activities for organizations today. Fortunately, many different techniques and technologies are available to reduce the risk of cyberattacks. The following three widely used approaches are used to identify, assess, manage and resolve threats so that organizations can resume operations:
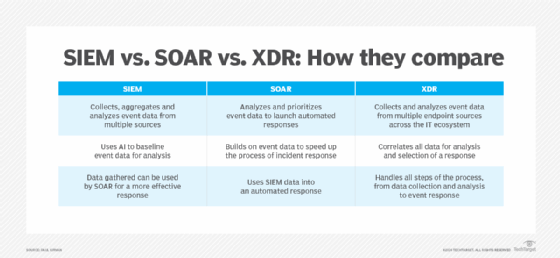
- Security information and event management. SIEM collects event log data, analyzes the data to identify suspicious activity and generates visibility to the event so that remedial initiatives can be launched.
- Security orchestration, automation and response. SOAR automatically analyzes data on an event and orchestrates the response so that security operations center (SOC) teams can resolve events more quickly.
- Extended detection and response. XDR provides threat hunting, identification of false positives and the creation of threat intelligence.
SIEM, SOAR and XDR technologies are all used to detect and resolve security events. SIEM gathers data and analyzes security incidents; SOAR, which handles automated incident responses, uses information from SIEM to fulfill its functions. XDR, though, may use SIEM data but it's an all-inclusive product that handles security events end to end.
This article compares and contrasts each technology and offers guidance on which approach(es) to use for comprehensive cybersecurity management.
What is SIEM?
SIEM builds on two fundamental elements: security information management and security event management. One of the important functions of SIEM is to help cybersecurity teams achieve compliance with key security standards and regulations. AI enhances SIEM capabilities by providing greater analytical capabilities for identifying suspected or actual cyberincidents. SIEM also facilitates the launch of security incident response activities.
A key activity of SIEM tools is the collection of security event data for current and future analysis. Each tool has rules for how events are analyzed and can evaluate threats by comparing them with a large database of previous cyberattacks.
This article is part of
What is threat detection and response (TDR)? Complete guide
The principal output from a SIEM system is intelligence regarding a security event that can be used to formulate and launch a suitable response, mitigation and recovery. Integrated dashboards provide real-time displays of cyberattack data for launching incident responses and establishing priorities for event response activities.
What is SOAR?
Automation of cyberattack response activities is one of the principal activities of a SOAR system. The addition of SOAR technology in SOCs greatly improves the efficiency of cybersecurity teams. While they may be focusing on a variety of security issues, the SOAR system is actively addressing identified security breaches, providing real-time data on how the mitigation is going. It also supports threat hunting, identification of false positives and the creation of threat intelligence.
The orchestration element gathers all relevant security tools and centrally manages them, which greatly increases the efficiency of event responses. It typically provides the starting point for launching the automation elements that actively go out and address the incident. The automation element uses numerous playbooks and other response tools to deliver the most effective response.
AI is also increasingly part of SOAR capabilities, as it can streamline the process of evaluating and selecting the best set of responses for a specific event.
What is XDR?
Considering the complex environment in use by IT organizations today, various platforms and services -- particularly cloud, multi-cloud and hybrid environments -- are in use. They provide a full scope of detection, analysis and response capabilities that range from office endpoint devices and networks to WAN environments and multiple offices within the IT ecosystem. AI is typically a key component in an XDR platform. XDR systems are quickly becoming a go-to solution for cybersecurity organizations and SOCs.
Similar to SOAR technology, XDR systems perform what may be considered a complete suite of cybersecurity prevention, detection, analysis and response activities. XDR can initiate automated incident response activities and provide end-to-end automated management of all detection, response and mitigation activities. It can also provide return-to-service activities that not only eliminate suspicious code, but also return systems to normal operations.
Key differences among SIEM vs. SOAR vs. XDR
Each of the three solutions described in this article contributes to the detection and resolution of security events. They differ in their various activities yet can also complement each other in the right configuration. The inclusion of AI capabilities greatly increases the usability of each approach and is likely to be a major component of systems into the latter part of the decade.
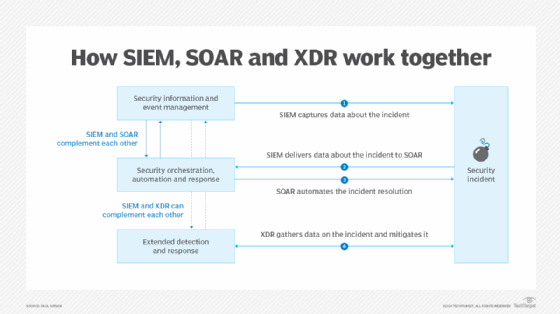
In practice, SIEM and SOAR tools complement each other, and XDR is a standalone product. However, the three tools can complement one another. SIEM gathers and analyzes event data, helps facilitate incident responses and provides data needed by SOAR to launch the automated response. Working together, they provide a solid end-to-end means for managing security breaches.
XDR is a newer, more powerful and all-inclusive solution for end-to-end security event management. But, when preparing for an automated response, it also uses the data that SIEM captures. It may share data with SOAR, but SIEM has the more complementary relationship. XDR's ability to address issues occurring in internal endpoints, as well as distant offices, cloud environments, multiple websites and complex networks, makes it an important go-to solution for SOC teams.
The inclusion of AI capabilities in each approach greatly increases their overall value to cybersecurity teams and SOCs.
Each option offers many benefits and supports cybersecurity teams and SOCs. And, because each system, properly configured, can automate the security event management process, SOC efficiency and productivity are increased.
10 steps to select tools
As noted earlier, the complementary nature of SIEM and SOAR systems means they are often paired. XDR may be a standalone solution, but combining the capabilities of all three tools makes good sense.
Consider the following steps when selecting your tools:
- Review and update your cybersecurity management requirements. Most organizations probably have some form of cybersecurity management and maybe a SOC, so the first step is to review security requirements in light of business needs and threat intelligence.
- Examine current security systems. If security systems, including the three described in this article, are being used, determine if they are sufficient for current and future needs.
- Secure senior management approval and budgeting. Brief senior company and IT management on plans for a change in cybersecurity management systems, and prepare a use case and an ROI analysis.
- Review and update cybersecurity strategies. Determine if existing strategies are sufficient. Also, determine if skill sets are sufficient or need to be expanded. Finally, determine budgetary considerations, especially when evaluating the cost of prospective software tools and third-party services.
- Check out security systems, especially SIEM, SOAR and XDR. In addition to a powerful platform, look for AI capabilities, easy-to-use dashboards, scalability, compatibility with existing platforms and overall performance. Examine multiple platforms, and consider blending two or all three of the tools discussed in this article. Don't forget to check out vendor capabilities and support.
- Establish a project team and plan. Identify a team of cybersecurity employees who can facilitate all aspects of the project. Create a project plan for each phase of the new system. Examine current policies and procedures. Include a risk assessment, if possible.
- Use a multiphase rollout, testing and acceptance process. If possible, install the new or updated system in phases to ensure that each step is tested and validated, bugs are fixed and each step has acceptance testing by the security department and SOC.
- Provide training, advice to employees and senior management. Arrange for training of security team members, ensure that the system is fully documented and try out various scenarios to see how the system responds. Provide timely alerts to employees about the new or updated system, and regularly brief management on progress.
- Ensure that maintenance and ongoing support are launched. Once the system is in production, conduct initial performance reviews to see how well it is working. Update security policies and procedures as needed.
- Launch monitoring and continuous improvement. Schedule periodic reviews to see how the system is performing, review any security events, update playbooks and procedures, and continually improve the system's overall performance.
However an organization decides to do it, managing cyberthreats should be one of its highest priorities. Luckily, today, there is a wide variety of techniques and technologies that are available to reduce the risk, including SIEM, SOAR and XDR.
Paul Kirvan is an independent consultant, IT auditor, technical writer, editor and educator. He has more than 25 years of experience in business continuity, disaster recovery, security, enterprise risk management, telecom and IT auditing.







