war driving (access point mapping)
What is war driving (access point mapping)?
War driving, also called access point mapping, is the act of locating and exploiting connections to wireless local area networks (WLANs) while driving around a given location. War drivers require a vehicle, a laptop or smartphone, a wireless Ethernet card set to work in promiscuous mode, an antenna and designated war driving software.
WLANs frequently have a range that extend beyond their designated areas. This means an outside user can intrude into the network, obtain a free internet connection and -- if the network is not properly secured -- possibly gain access to company records and other resources. Sometimes this user is benign, such as a security researcher or penetration tester, but more often than not, malicious users leverage war driving to prepare future cyber attacks.
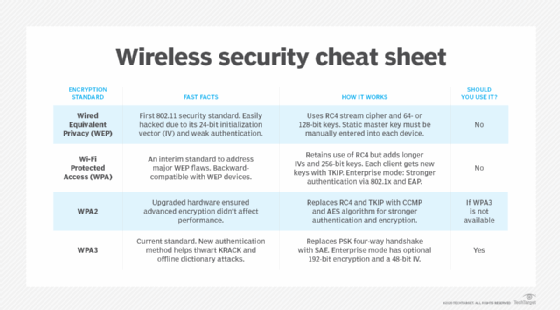
Attackers often automate the wireless network mapping task using software a GPS device. Many network vulnerabilities such attackers exploit come from weaknesses in the Wired Equivalent Privacy (WEP) algorithm. As more organizations go wireless, particularly with the rise in remote and hybrid employees, they become increasingly vulnerable to war driving attempts and following attacks.
Companies that have replaced WEP with the more secure WPA and WPA2 algorithms have less vulnerable Wi-Fi access points and are therefore safer from war drivers.
The emergence of war driving
The term war driving derives from an older, similar approach called war dialing. War dialing aimed to breach telephone systems by dialing multiple phone numbers in sequence to search for a working modem.
Modern-day war dialing involves using a software program -- known as a war dialer -- to automatically dial a large number of telephone numbers in order to find numbers with attached modems. A hacker simply enters an area code and the three-digit exchange of a phone number into the war dialer. The software then calls these numbers in sequence. When it finishes, the hacker receives a log of phone numbers with modems that answered the dialer's call, which they can then use to gain unauthorized access to the computer systems attached to those modems.
War driving is considered an evolution of war dialing. The term was coined by computer security consultant Peter Shipley in 1999 as part of a cybersecurity study. As part of the study, Shipley dialed every telephone number in five specific exchanges looking for at-risk modems. He found unprotected modems connected to personal computers, hotels and even banks, which meant that he could potentially gain access to vast numbers of vulnerable devices and the sensitive information stored on them.
In 2000, Shipley also found numerous vulnerable Wi-Fi networks in the areas he surveyed. He authored scripts to interface with his GPS device and read coordinates. These scripts enabled him to automatically plot Wi-Fi access points on a map, removing the requirement to write down physical locations when looking for unsecured wireless access points.
How war driving works
War drivers require four tools for war driving:
- Laptop or smartphone.
- Antenna.
- GPS.
- Vehicle.
The laptop or smartphone enables the war driver to remain mobile while searching for vulnerable Wi-Fi networks. A war driver typically mounts the antenna on top of their vehicle. As the vehicle moves, the antenna can pick up Wi-Fi signals from networks to find open ones.
Special monitoring software connects the device to a GPS receiver and the car-mounted antenna. It enables the attacker to decrypt Wi-Fi routers and capture network passwords. Examples of war driving software include the following:
- Packet sniffers.
- Traffic analyzers.
- Signal strength testers.
- Password crackers.
Once these components are all in place, the attacker then drives the streets of a city. Their laptop scans for unprotected 802.11 wireless networks and creates a database or log that maps the location of open, vulnerable networks.
Purpose of war driving
Malicious users such as hackers engage in war driving to steal sensitive information, such as personally identifiable information, IP or financial data. Their goal might also be to use one or more unsecured networks for criminal activity. Such activity may end up causing financial damage to the network owner, or they could be held liable for any fallout of that activity, such as a data breach, identity theft or ransomware attacks.
Ethical hackers and penetration testers sometimes engage in war driving to find security weaknesses in enterprise networks, then highlight these weaknesses to the organization to help them improve their overall security.
Companies have also used war driving for benign purposes. For example, Google conducted war driving for its Street View application. Google located LAN wireless hotspots and home WiFi networks by using recorded footage for Street View's interactive, online images.
Although the war driving process is not dangerous by itself, it can give hackers access to WiFi networks, which could then enable them to access devices on the network, install malware and steal sensitive or valuable information.
How to protect against war driving
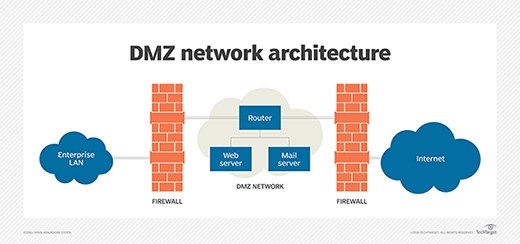
Companies that use wireless LANs must add security safeguards to ensure that only intended users have access to the network. Some of these safeguards include using a strong firewall and demilitarized zone (DMZ).
Other simple strategies used to protect enterprise networks from war driving include the following:
- Turning off the WiFi network when not in use.
- Shutting down wireless routers when not in use.
- Changing the router's default admin password to a strong, unique password.
- Using routers that enable WPA encryption.
- Configuring the router to not broadcast the SSID.
Learn best practices for wireless network security, compare breach and attack simulation vs. penetration testing and see 12 types of wireless network attacks and how to prevent them.