Wired Equivalent Privacy (WEP)
What is Wired Equivalent Privacy (WEP)?
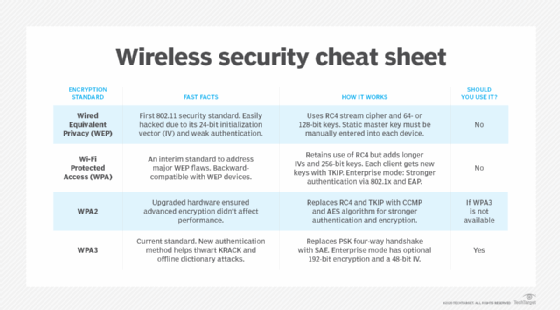
Wired Equivalent Privacy (WEP) is a security protocol, specified in the IEEE Wireless Fidelity (Wi-Fi) standard, 802.11b. That standard is designed to provide a wireless local area network (WLAN) with a level of security and privacy comparable to what is usually expected of a wired LAN.
The WEP protocol was introduced in 1997 but was plagued by several security issues. Standards bodies began discouraging its use in the early 2000s, as more effective standards were introduced.
WEP attempted to limit access to wireless network data in the same way wired local area networks (LANs) protect data. Users with physical access to the network access points are the only ones with access to wired networks. Wireless networks like Wi-Fi depend on encryption protocols like WEP to prevent unauthorized access to network data.
Physical security mechanisms protect a wired LAN to some degree. For example, controlled access to a building prevents outsiders from walking in and plugging their devices into the LAN. Outsiders can gain access to WLANs via the radio waves that connect to the network.
How does WEP work?
The Wired Equivalent Privacy protocol adds security similar to a wired network's physical security by encrypting data transmitted over the WLAN. Data encryption protects the vulnerable wireless link between clients and access points.
After WEP secures wireless data transmissions, other LAN security mechanisms can ensure privacy and data confidentiality. These include password protection, end-to-end encryption, virtual private networks and authentication.
The basic network security services the protocol provides for wireless networks include the following:
- Privacy. WEP initially used a 64-bit key with the RC4 stream encryption algorithm to encrypt data transmitted wirelessly. Later versions of the protocol added support for 128-bit keys and 256-bit keys for improved security. WEP uses a 24-bit initialization vector, which resulted in effective key lengths of 40, 104 and 232 bits.
- Data integrity. WEP uses the CRC-32 checksum algorithm to check that transmitted data is unchanged at its destination. The sender uses the CRC-32 cyclic redundancy check to generate a 32-bit hash value from a sequence of data. The recipient uses the same check on receipt. If the two values differ, the recipient can request a retransmission.
- Authentication. WEP authenticates clients when they first connect to the wireless network access point. It enables authentication of wireless clients with these two mechanisms:
- Open System Authentication. With OSA, Wi-Fi-connected systems can access any WEP network access point, as long as the connected system uses a service set identifier that matches the access point SSID.
- Shared Key Authentication. With SKA, Wi-Fi-connected systems use a four-step challenge-response algorithm to authenticate.
Drawbacks to Wired Equivalent Privacy
WEP is widely implemented and deployed, but it suffers from serious security weaknesses. These include:
- Stream cipher. Encryption algorithms applied to data streams, called stream ciphers, can be vulnerable to attack when a key is reused. The protocol's relatively small key space makes it impossible to avoid reusing keys.
- RC4 weaknesses. The RC4 algorithm itself has come under scrutiny for cryptographic weakness and is no longer considered safe to use.
- Optional. As designed, the protocol use is optional. Because it's optional, users often failed to activate it when installing WEP-enabled devices.
- Shared key. The default configuration for these systems uses a single shared key for all users. You can't authenticate individual users when all users share the same key.
These weaknesses doomed WEP. Most standards bodies deprecated the protocol soon after the Wi-Fi Protected Access (WPA) protocol became available in 2003.
WEP vs. WPA
The IEEE introduced Wired Equivalent Privacy in the 802.11 wireless networking standard in 1997 and then released WPA as a proposed replacement five years later. Efforts to fix WEP during its short lifetime failed to produce a secure solution to wireless network access. WPA2 formally replaced it in 2004.
WEP variants and improved versions of WPA include the following protocols:
- WEP2. After security issues emerged, changes to the IEEE specifications increased the WEP key length to 128 bits and required the use of Kerberos authentication. However, these changes proved insufficient to make WEP more secure and were dropped from the standard.
- WEPplus or WEP+. Agere Systems, an integrated circuit component company, developed this proprietary variant. WEP+ eliminated weak keys from the key space. However, fundamental issues remained, and only Agere Systems Wi-Fi products used WEP+.
- WPA. The first version of WPA increased key length to 128 bits, and replaced the CRC-32 integrity check with the Temporal Key Integrity Protocol. However, WPA still uses the RC4 encryption algorithm, and retained other weaknesses from WEP.
- WPA2. This WPA update added stronger encryption and integrity protection. It uses the Counter Mode Cipher Block Chaining Message Authentication Code Protocol, which incorporates the Advanced Encryption Standard algorithm for encryption and integrity verification of wireless transmissions. WPA2 comes in the following two modes:
- WPA2-Enterprise requires a Remote Authentication Dial-In User Service authentication server to authenticate users.
- WPA2-Pre-Shared Key is intended for personal use and relies on pre-shared keys given to authorized users.
- WPA3. The current version of WPA became available in 2018. It provides much improved security for wireless network users. WPA3 improvements include:
- stronger encryption in both enterprise and personal modes;
- improved authentication for personal mode; and
- perfect forward secrecy for personal mode communications.
How is WEP used?
Wireless hardware manufacturers implemented WEP in hardware, which meant updates to the security protocol had to fit into the flash memory of wireless network interface cards and network access point devices. This limited the scope of improvements that were possible with WEP and WPA. It also meant systems using older hardware could be vulnerable to well-known attacks.
Given the widespread deployment of inexpensive wireless devices and access points, WEP is still being used and will continue to be used until the obsolete hardware is retired. That means networking and IT professionals should be vigilant in identifying and replacing these obsolete devices.
Learn more about the protocols used to secure wireless networks in this overview of WLAN security standards.








