What is perfect forward secrecy (PFS)?
Perfect forward secrecy (PFS), also known as forward secrecy, is an encryption style known for producing temporary private key exchanges between clients and servers. For every individual session initiated by a user, a unique session key is generated. If the identifying certificate or one of these session keys is compromised, data from any other session will not be affected. Therefore, past sessions and the information within them are protected from any future attacks.
Without perfect forward secrecy, when a user initiates a communication session with a client, the entire conversation is encrypted based on the endpoint's special key. However, the endpoint uses the same special key to generate encryption for all its sessions, and if the key becomes compromised, so does all the information contained within each communication the endpoint has ever had.
With perfect forward secrecy, every communication session generates a unique encryption key that is separate from the special key and only lasts for the duration of the session. So, if an attacker were to compromise a user's special key, the communications would remain encrypted and secure. Similarly, if an attacker were to compromise the unique encryption key, only that specific session would be leaked.
Protecting data on the transport layer of a network, PFS has become a security standard for developers to implement into messaging services or websites that are dedicated to user privacy. Tools applying this feature can change encryption keys as frequently as every text message, phone call or page refresh. The Internet Engineering Task Force has published the Transport Layer Security standard to mandate perfect forward secrecy for all TLS sessions.
Why is perfect forward secrecy important?
Forward secrecy helps to protect against "record now, decrypt later" attacks. It is best practice to assume that all traffic going over a public network is being recorded, including anything transmitted by the internet or over wireless transmission. Without forward secrecy, every message to or from a specific endpoint might be protected by the same secret key. If that secret key were to be acquired by an attacker, either through hacking the endpoint or compromising the key, then all recorded past messages would be trivial to decrypt.
With forward secrecy, every message is protected by a different key. This means that if the long-lived certificate or key used in the initial exchange were stolen or cracked, it would not reveal any of the message contents. If the session key were cracked for a specific message, it would only reveal the contents of that message and not any others.
How does perfect forward secrecy work?
PFS involves several steps, typically including a handshake and a session key exchange.
- Handshake or authentication. One endpoint contacts the other. To confirm their identities, a long-lived secret is used. This might be a preshared key, password or public key certificate. This initial exchange is only used for authentication, and even though it can provide encryption, communication through this channel is not considered secure.
- Session key exchange. The two endpoints use a method to generate a shared secret or session key, without transmitting it. This is often done with key exchange algorithms like Diffie-Hellman or Rivest-Shamir-Adleman. This shared secret is used to encrypt the single message.
- Repeat key exchange. The key exchange is repeated for every new message. In some systems, keys for many messages are generated at once to prevent the need for active back-and-forth communication.
Heartbleed and perfect forward secrecy
Perfect forward secrecy became more interesting after the discovery of the Heartbleed bug that affected OpenSSL beginning in 2012. The vulnerability results from insufficient input validation in the utilization of the TLS protocol heartbeat extension.
Heartbleed is known as a buffer over-read vulnerability. It enables the user to read more data than allowed, leaking an entire chain of information up to 64 kilobytes. Attackers could abuse the Heartbleed bug to read private memory from the server, and if that private memory contained the secret key, they would then be able to decrypt all of that server's secure traffic.
While Heartbleed has been publicly disclosed since 2014, it proved the simplicity of an OpenSSL attack and sparked the conversation around temporary methods of key exchange. By adding forward secrecy, all past traffic could be assumed safe.
Perfect forward secrecy in use
Since its inception, perfect forward secrecy has become widely adopted by information providers and is known as a crucial security feature. Signal, a messaging protocol for end-to-end encryption found in WhatsApp, Google Allo messenger and Facebook conversations, popularized PFS. Known as the "double ratchet" system, the Signal protocol creates a new encryption key with every single message, giving both forward and backward security. Most recently, it also introduced a feature that enables messages to self-destruct.
In 2011, Google provided Gmail, Google Docs and encrypted search users with perfect forward secrecy by default. X, formerly Twitter, has offered perfect forward secrecy to all users since 2013. In 2016, Apple announced a new, mandatory protocol for all iOS apps requiring the use of App Transport Security, a security feature that uses perfect forward secrecy.
Forward secrecy in Wi-Fi
Perfect forward secrecy is a mandatory feature in the latest Wi-Fi security standard, Wi-Fi Protected Access 3 (WPA3). It was not a feature in earlier forms of consumer WPA, so all traffic could be decrypted by anyone with the shared secret. This made it possible for an attacker to record all the wireless traffic on a network and store it for offline attacks. Any attacker with the Wi-Fi password would be able to read all the wireless traffic.
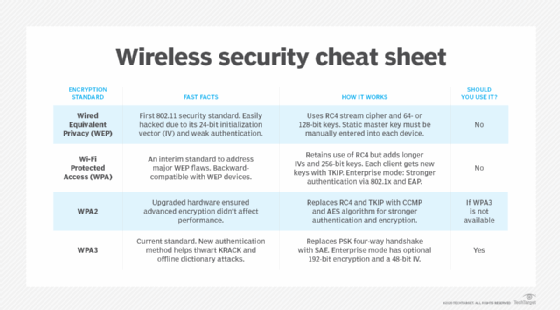
This is one reason why public Wi-Fi is considered extremely insecure. For example, anyone at a coffee shop with a shared Wi-Fi password using WPA or WPA2 could read all transmitted data between any device and the router.
As wireless networks have progressed, the protocols for securing them have evolved significantly. Learn about wireless LAN security standards and how to clearly distinguish the differences between WEP, WPA, WPA2 and WPA3.