
What is a rogue DHCP server?
Rogue DHCP servers can throw DHCP infrastructures out of balance. These servers cause numerous network problems but are easy to detect and remove with proper network management.
Dynamic Host Configuration Protocol infrastructures contain a potential pitfall: rogue DHCP servers. They aren't a common problem, but when one is present, it wreaks havoc.
Rogue DHCP servers are any DHCP devices that administrators are unaware of or aren't managing. They can be a serious security concern and a nuisance to users, causing significant connectivity issues for clients and becoming difficult for troubleshooters to detect.
Network service technicians and administrators benefit from recognizing the signs of a rogue DHCP server. This guide explains what a rogue DHCP server is and where one might occur, and it offers practical advice for detecting and removing it.
The role of a DHCP server
Most network environments rely on DHCP servers to lease IP address configurations to client devices. DHCP makes device management easier by setting standard options, such as DNS and gateway values. With DHCP, administrators don't need to perform tedious manual IP address configurations for most network nodes. However, static IP address settings are still standard for servers, routers and other infrastructure devices.
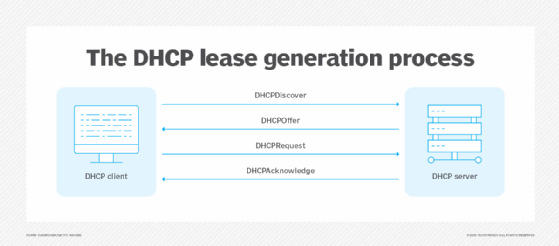
DHCP works by using the following four-step lease generation process initiated by client devices:
- Discover. The client broadcasts to find a DHCP server.
- Offer. DHCP servers offer an IP address to the client.
- Request. Clients request an IP address, usually from the first DHCP server to respond.
- Acknowledge. The DHCP server acknowledges the client's lease.
The IP address lease is temporary. Client devices periodically check in with the DHCP server to renew the lease.
Administrators create one or more IP address pools -- also called scopes -- on DHCP servers. The DHCP service offers addresses from these scopes along with specific information, such as gateway IP addresses, DNS server IP addresses and lease duration, among other options. Accurate scope configuration is critical; mistakes lead to disconnected nodes, isolated systems or duplicate IP addresses.
The problem with rogue DHCP servers
Network administrators carefully manage IP address settings for each subnet. A network diagram typically displays expected IP address configurations and which DHCP servers provide them.
Rogue DHCP servers are devices that lease IP addresses outside this management scope. Because IT doesn't manage these devices, they might issue incorrect IP address settings that interfere with normal network communications.
How rogue DHCP servers get introduced
Rogue DHCP servers are either deliberate and malicious or accidental. The following situations can introduce a rogue DHCP server into a network:
- A network technician installs a new router with an active DHCP service. Train staff to avoid adding devices with DHCP services enabled unless explicitly instructed to do so.
- A technician, user or malicious actor might deploy a wireless access point (AP) with an active DHCP service.
- A server administrator enables the DHCP service on a router without prior permission and without a complete understanding of the network's IP address structure.
Not all rogue DHCP server deployments indicate an attack on the network. Those who don't understand the ramifications or cannot see the entire network structure often deploy them by accident.
Rogue DHCP server issues
Rogue DHCP servers cause specific issues that have a tremendous effect on network connectivity and security, including the following:
- Incorrect IP address, subnet mask, default gateway and DNS server configurations.
- Duplicate IP addresses among nodes.
- Inconsistent network connectivity based on default gateway and DNS settings.
- Misconfigured or out-of-date client or DHCP server DNS registrations.
- DHCP scopes consisting of overlapping IP address ranges.
- Redirected connections for man-in-the-middle attacks or unauthorized network access.
Detecting and removing rogue DHCP servers
Detecting and removing DHCP servers to ensure reliable access to network services is critical.
Detecting rogue DHCP servers involves discovering the following issues:
- Numerous clients with incorrect or duplicate IP, default gateway and DNS server information.
- Client redirects to unexpected sites.
Various issues can lead to these problems, so begin rogue DHCP detection by having a full view of your network environment. Correlate help desk tickets and user complaints with data from log files, network performance tools, protocol analyzers and scanners. Combining these tools gives a complete picture of your network environment.
Confirm your legitimate DHCP servers have correct configurations, and check for any typos in the scopes. Accurate scopes and options ensure you can rule out configuration mistakes on the legitimate servers. Scan and analyze network services and protocols periodically to ensure all results fall within normal parameters.
Another indicator of a rogue DHCP server is increased DHCP traffic. Log files or network traffic analysis might reveal increased DHCP traffic. If you suspect a rogue DHCP server, tools such as Wireshark or tcpdump are invaluable for finding the device. These protocol analyzers intercept DHCP traffic and display source and destination MAC and IP address information. Also, consider scanning the network for DHCP services and unexpected network nodes with Nmap. These steps help narrow down which devices might be causing issues.
User feedback might also indicate a rogue DHCP server. Users who complain about slow connectivity, unexpected website redirects or failed access to online resources could be experiencing the effects of a rogue DHCP server.
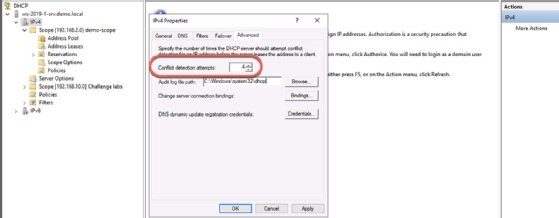
One short-term technique to alleviate duplicate IP address problems is to configure conflict detection attempts. This feature requires you to host DHCP on a Windows server.
Removing rogue DHCP servers can be as simple as turning off the device or disabling the service. Begin by making sure the device itself is legitimate. In other words, is the rogue DHCP server based on a mistake by an administrator or user on a valid device? Or is it the result of a malicious act by someone who connected the unauthorized device to your network?
If a malicious user deployed the rogue DHCP server, remove the device. This forces all DHCP clients to lease new IP addresses from the legitimate DHCP servers. Network teams should also watch for Address Resolution Protocol poisoning and web URL redirection issues. Review the policies that enabled the malicious or unauthorized user to deploy the server. There might be physical security problems or unrestricted network access, often through wireless networks.
Be sure to explain the issue to the user or technician if the rogue DHCP server configuration was accidental.
Preventing rogue DHCP servers
Windows Server offers ways to avoid rogue Windows-based DHCP. In an Active Directory environment, the enterprise administrator must authorize Windows Server DHCP services before they lease IP addresses. However, this feature doesn't avoid issues caused by non-Windows DHCP servers, such as those hosted by Linux, routers or wireless APs.
Damon Garn owns Cogspinner Coaction and provides freelance IT writing and editing services. He has written multiple CompTIA study guides, including the Linux+, Cloud Essentials+ and Server+ guides, and contributes extensively to Informa TechTarget, The New Stack and CompTIA Blogs.





