Chernobyl virus
What is the Chernobyl virus?
The Chernobyl virus is a computer virus with a potentially devastating payload that destroys all computer data when an infected file is executed.
Since many files are executed during computer use, the virus is able to spread quickly and infect those files.
The Chernobyl virus is most notably recognized as the first virus known to have the power to damage computer hardware. The activated viral strain attempts to erase the hard drive and overwrite the system's BIOS as well.
The Chernobyl virus was actually a variant of a parent virus known as CIH, the initials for the alleged author of the virus, Chen Ing-Hau, a computer engineering student in Taiwan.
CIH is sometimes referred to as a "space filler virus," referring to its ability to clandestinely take up file space on computers and prevent antivirus software from running.
It was named after the famous Chernobyl nuclear disaster that occurred in the Soviet Union on April 26, 1986.
When was the Chernobyl virus circulated?
The virus was detected as early as 1998, but its payload was first triggered on April 26, 1999 -- which was the 13th anniversary of the disaster at the Chernobyl nuclear reactor.
Although U.S. and European computer users were affected, especially students and some businesses, most of Chernobyl's damage was wrought in Asia and the Middle East.
At the time, CIH variants would activate on the 26th day of each month, while others did their damage on April 26 or June 26.
Users of Microsoft Windows 95 and Windows 98 operating systems with machines containing motherboards with the Intel 430TX chipset were the most susceptible to contracting the CIH virus.
Thus, users of DOS, Windows 3.x, Windows NT, Windows 2000, IBM or Macintosh computers were not considered at risk at the time.
After the initial spread, several variants of the CIH virus emerged behind it:
- CIH v1.2/CIH.1003 was the most common one and contained the string CIH v1.2 TTIT. It was activated on April 26.
- CIH v1.3/CIH.1010.A and CIH1010 contained the string CIH v1.3 TTIT. They was also activated on April 26.
- CIH v1.4/CIH.1019 is still circulating on a limited basis, contains the string CIH v1.4 TATUNG and can be activated on any day of the month.
How did the Chernobyl virus operate?
The Chernobyl parent virus, CIH, was spread via a portable .exe file format. It infected the host system by splitting its code up and inserting it into inter-section gaps within the infected files.
From there, it reassembled and routed its code segments in unused space within the P.E. header. This is how it earned its nickname, "Spacefiller."
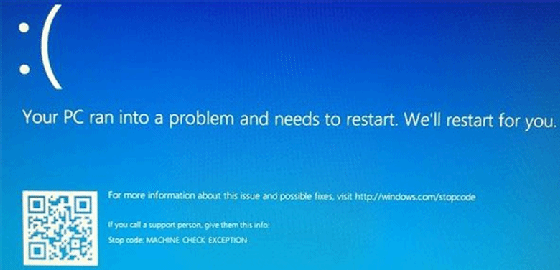
The first payload would then overwrite the first megabyte of the hard disk and delete the partition table, causing the infected machine to execute the blue screen of death.
The second payload would rewrite the flash BIOS chip by replacing critical boot code with junk code. When executed properly, the computer would then not restart at all. However, it would sometimes not work on certain machines.








