
peach_fotolia - stock.adobe.com
How passwordless authentication aids identity security
Enterprise Strategy Group's Jack Poller discusses survey results on user authentication practices and explains the security benefits of passwordless methods.
Identity security remains a challenge for many organizations -- and weak forms of user authentication put them at risk of compromises and attacks, according to a 2023 survey of 377 IT, cybersecurity and application development professionals conducted by TechTarget's Enterprise Strategy Group (ESG). But newer passwordless authentication methods offer a better way of securing identities.
That's the view of Jack Poller, a senior analyst at ESG who covers identity and data security technologies. Poller co-authored a report on the survey titled "Passwordless in the Enterprise" that ESG published in September 2023. The report recommended that organizations make plans to deploy passwordless authentication if they haven't already done so.
As an interim step, it said they should also make multifactor authentication (MFA) mandatory for both workers and customers and implement stronger forms of MFA than most companies use now. Upgrading MFA approaches would at least improve password-based authentication while organizations develop a passwordless strategy, the report said.
In this Q&A, Poller discusses the survey results, how passwordless authentication can strengthen identity security and the current state of passwordless technology.
Editor's note: The following was edited for length and clarity.
Nearly nine in 10 respondents said practices for authenticating employee identities are critical or very important to their organization. But in the report, you wrote that securing identities is a challenge many organizations have yet to overcome. What are the issues that make it challenging for them?
 Jack Poller
Jack Poller
Jack Poller: We had a question on the challenges people face -- what's holding their organization back from optimizing its authentication strategy. A cybersecurity skills shortage is the biggest one. And higher priorities: 'It's important, but we've got better things to do,' which I've been arguing is dumb -- [cybersecurity] should start with authenticating identities. Also, a lack of development staff to be able to do it. And it isn't easy to integrate authentication across your entire platform environment.
Eighty-seven percent of respondents were completely or mostly confident that their organization would detect an attacker using a compromised account. But 45% said they knew accounts or credentials had been compromised in the past 12 months and 32% suspected they had been. And 59% of those respondents said such compromises led to one or more successful cybersecurity attacks. Do those results indicate that the confidence about detecting attackers might be overstated?
Poller: Yes, they are overconfident in detecting those particular types of attacks -- absolutely 100% overconfident. They keep getting attacked, and those attacks lead to successful compromises. Therefore, they're wrong about their ability to detect it. That, among other things, should be a red flag to say, 'You're doing something wrong -- fix it.'

Relative to other areas of identity and access management (IAM), 32% of respondents said they expected their organization to significantly increase spending on authentication over the next 12 months, and 50% expected a slight increase. Are those good numbers from your standpoint?
Poller: Relative to other areas of IAM, yes. Investing in tools that make it easier to do passwordless authentication and stronger MFA is always a good thing. At this point, most organizations have an adequate investment in managing their identities from an IT operations point of view -- i.e., when your company brings in a new application for you to use, it's no longer a challenge for them to get you access to that application by giving your existing identity permission. It's a well-understood problem. We know how to do that, and IT operations manages it very efficiently.
We now need to focus on the security side: How do we secure identities and access? And the very first step in that is focusing on the authentication piece. So, investing more in securing authentication versus identity management is good. I'm not going to make an argument that 32% of organizations is sufficient or insufficient. But until we've solved that problem, more is better because the numbers show we clearly have a big problem.
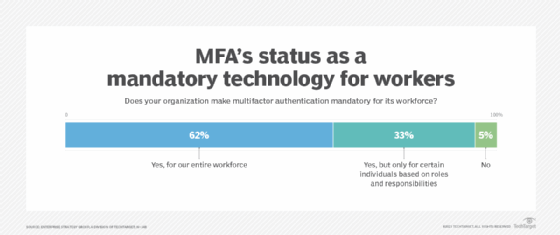
Nearly 40% of organizations that use MFA internally don't make it mandatory for their entire workforce or at all. Does that surprise you?
Poller: It surprises me, and it makes me upset. We have long known the issues with password-based authentication. We have also long known that MFA, done correctly, addresses a significant part of that. In the report, I call out that the organizations that do MFA tend to use the least secure methods of it: SMS- or email-based codes. I would much prefer that they go to time-based, one-time passwords and authenticator apps, and then eventually passwordless.
But yes, we know how important it is to do MFA, and we know how quickly it solves the problem. I'll give you an anecdote. I talked to the CISO of a financial services company that had an externally facing application with 30 million customers. They made MFA mandatory for their customers, and two weeks later, they saw a 98% reduction in the number of authentication attacks they observed. We know how successful it is. We should just be doing it.
What, then, are the potential benefits of passwordless authentication vs. MFA?
Poller: The big benefit is passwordless removes the human element -- the phishing and social engineering aspect -- out of the equation. No matter what we do with anything else, whether it's passwords only or passwords and MFA in some form, it's based on the concept of having a shared secret that a human knows -- and humans are fallible and we make mistakes. We're gullible and we're easily conned. While that's in the equation, the attackers will figure out a way to con people and get access to passwords and MFA codes and yada yada yada.
Passwordless is phishing-resistant. We don't want to say it's phishing-proof because somebody may find a way to phish somebody at some point on passwordless. But today we believe that passwordless authentication effectively eliminates the social engineering attacks.
Fifty-nine percent of the respondents that expect increased spending on authentication said adding or improving passwordless authentication methods is their top investment priority. Where are most organizations at this point on passwordless deployments? Is it still emerging?
Poller: Yeah, it's still emerging. But customer-facing passwordless authentication is ahead of workforce-facing authentication, and there are two reasons for that. The first reason is that the risk exposure is more visible on the customer-facing side. When a customer account gets phished, that customer's private data is immediately available. Typically, it's either payment data or health data that the attackers are after -- they get that data and then they sell it and/or exploit it immediately. There's a very clear, visible risk for organizations that they can address. It also reduces the friction [for customers] because MFA has friction associated with it.
The other reason the customer-facing side is ahead is the joint work by Microsoft, Apple and Google [announced in 2022] means that all modern devices and web browsers have the fundamental components necessary to do FIDO- and WebAuthn-based passwordless authentication. Before that support became available, everybody had to roll their own code, and it was very complex. Now that fundamental base layer exists everywhere you look for all these web-facing applications, so you no longer have to worry about it, regardless of whether you're developing on a mobile device or a web browser. It's easy for developers.
When you look at the workforce side, we're still dealing with a lot of legacy applications that may not even support MFA or single sign-on (SSO), so getting them to support passwordless is also a challenge. That's part of why the workforce side is behind, plus the first step is authenticating to the device, which for the workforce typically means a PC. Microsoft has Windows Hello, but not all the devices were quick with [support for] it, and not all organizations understand it or support it.
The reason I bring that up is Microsoft is pushing the next version of Windows 11 to be passwordless-based using Windows Hello with biometrics, and they're pushing very hard to eliminate passwords as quickly as possible. Microsoft manages umpty-ump-gazillion personal accounts, plus they see what organizations do on Entra ID in the cloud. Microsoft's data shows that when Microsoft controls the authentication process, they have three to five times better security outcomes than when an organization does, because Microsoft is focused on that. Very soon, we will see workforce-facing passwordless on the PCs, and then that will start pushing it into the organization and all the applications.
We'll also see that [IAM vendors] like Okta and Ping and all the identity providers, or IdPs, now have passwordless, and they'll start pushing that in to enable you to authenticate to the IdP and then from there push that data into an application that doesn't currently have the ability to support passwordless. They'll sort of proxy you in the middle.
To follow up on that, what's the current state of the tools and technologies that vendors are offering to support passwordless authentication? How mature are they?
Poller: I would say we're in version 1.0 of everybody's tool suite. When we talk about passwordless, there's FIDO authentication, and then there are things like biometrics, where it's face or fingerprint or voice recognition or whatever. Most of these applications, we've had them for roughly a couple of years at best. And we're only now getting to see the user experience with them and how users interact with passwordless and how easy or hard it is. Another year of this will feed into version 2 and version 3 tools, which will then become seamless and essentially invisible. We're not there yet.
And again, for many organizations, on the workforce side we have to coordinate authentication among cloud apps, on-premises apps and legacy apps that do or do not support MFA, SSO and passwordless. You have this huge mix, and for the next couple of years, the user experience is going to be suboptimal until we iron out all the bugs and figure out how to how to make everything work. It took us a couple years to get to where SSO just works and we no longer think about it.
What are your takeaways for user organizations based on the survey results?
Poller: My main takeaway is that authentication is still a problem for many, many organizations. We talked about some of the survey numbers -- organizations think they know what they're doing, but clearly the numbers show that they don't. We need to focus more on solving that authentication problem by implementing better forms of MFA and then moving as rapidly as possible to passwordless, because we know that identities are the primary source of data breaches. And by eliminating the identity risk, you drastically reduce the risk to the organization.
Read the full report
Enterprise Strategy Group subscribers can click here to access the research report on the survey covered in this Q&A.
Craig Stedman is an industry editor who creates in-depth packages of content on business intelligence, analytics, data management and other types of technologies for TechTarget Editorial.






