Security observability vs. visibility and monitoring
Security observability, monitoring and visibility play different roles but together provide the tools to establish an all-encompassing enterprise security architecture.
As IT infrastructures become increasingly distributed and complex, cybersecurity administrators struggle to protect users, data, applications, systems and networks from attacks. Layers upon layers of virtualization, containerization and fabric overlays make it difficult for security teams to properly view their network, identify threats and remediate them in a reasonable amount of time.
Advanced security tools that incorporate AI and machine learning capabilities tout their ability to provide security clarity in first- and third-party infrastructures, as well as the various software-defined network layers. At the same time, confusion has mounted over the roles of security observability vs. visibility and monitoring. Some see the three terms as interchangeable, but there are distinct differences that can affect how these security tools and processes interact.
Monitoring alerts security teams
Security monitoring tools have been around for decades. A tool or a function within a larger monitoring toolset is typically configured by an IT security administrator to ingest various device or software logs, Simple Network Management Protocol polls and traps, event messages, NetFlow, packet capture and other streaming telemetry data.
Triggers are usually set up, so when a security monitoring tool processes an event that matches a specific circumstance or meets a certain threshold, an alert is issued. This alert is fielded by IT security staff to identify whether it is a valid security threat, determine the root cause of the security incident and remediate the threat.
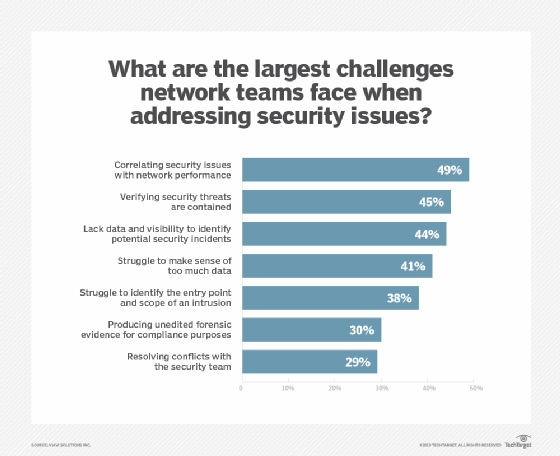
Security monitoring can be done at the host, system, application or network level. But traditional security monitoring tools take a large amount of administrator time to hunt down and resolve an incident using manual processes. The problem is magnified as infrastructures become more complex and more monitoring data is collected. Additionally, security incidents often generate alerts sourced from multiple security monitoring tools. These duplicated alerts can lead to security monitoring fatigue.
Observability provides intelligence and remediation
Security observability can help tackle monitoring fatigue. Observability platforms add intelligence to what is being monitored at a broad level to determine the true root cause of an alert and help administrators properly remediate it.
Advanced technologies such as AI, machine learning and automation help centralize, correlate and make sense of all the alert-induced noise produced by outputs from individual security monitoring tools.
Take a closer look at the security functions of observability:
- Verification of expected application performance. Performance thresholds can be set and will notify administrators when application performance dips below minimum levels.
- Behavior baselining and alerting when behavior veers from normal observations. Observability tools baseline normal infrastructure and traffic flow behavior and alert when that behavior deviates from a set threshold.
- AI-driven event and root cause analysis. AI can identify the specific hardware and software locations where an incident occurred and provide insights into how the issue is best resolved.
- Predictive analysis. Instead of reacting to infrastructure events that can cause application outages or performance issues, observability tools can identify areas of an infrastructure that should be addressed before any major incidents and outages occur.
- Network detection and response. NDR tools help provide full visibility across the entire data security lifecycle, starting from security event identification all the way to event resolution.
Visibility peels away the network layers
It's important to think of security visibility not so much from a technology point of view, but rather from the perspective of IT security teams. Visibility is all about the reach and depth that the existing set of monitoring tools and observability architectures can provide to security administrators in an easily digestible format.
Since networks are highly distributed, security visibility must be able to view all corners of the network under the purview of the enterprise -- the corporate LAN, WLAN and local data center, as well as remote sites across the WAN and private and public clouds.
Potential lack of network security visibility, for example, was prevalent in the early stages of the COVID-19 pandemic when employees were forced to vacate their offices and work from home. Security teams rushed to bolster their security monitoring and observability tools to increase visibility across the internet and at remote locations where users were accessing corporate applications and data.
The security visibility plane enables IT to peel away each software layer until it reaches the base foundation of the infrastructure. Monitoring tools ingest health and security information from virtualized servers, containers and network overlays. Additional monitoring also occurs on the physical hardware and host operating systems that form the foundation of the virtualized software platforms.
Different but equal
To highlight the role of observability vs. visibility and monitoring tools, a typical conversation between two IT security administrators about ways to more quickly resolve triggered security events will likely start at a granular level and broaden to a higher level.
In this scenario, specific tools would first need to be deployed and configured to monitor parts of the infrastructure. The problem with these tools producing overlapping and redundant alerts would then be addressed as well as ways alerts can be sent to a centralized tool to be intelligently analyzed and perhaps correlated to a single security incident.
Enter security observability. Monitoring and observability tools can be deployed in the LAN and data center, but what about public cloud scenarios? That's where security visibility comes in.
Observability vs. visibility and monitoring tools have distinct purposes yet play complementary roles in the overall enterprise security architecture.








