Top incident response tools: How to choose and use them
The OODA loop helps organizations throughout the incident response process, giving insight into the incident response tools needed to detect and respond to security events.
Security vulnerabilities exist in every network environment, and malicious actors are ready to exploit those weaknesses for ill-gotten gains. What an organization does to prevent and respond to tangible security events can determine its short-term future and long-term viability.
Implementing and using the proper incident response tools are critical to minimizing effects of security events and ensuring operations return to normal as quickly and efficiently as possible.
What are incident response tools and why are they important?
Incident response is the process of detecting security events and cyberattacks, taking the necessary steps for incident analysis and responding to what happened.
This process is a critical aspect of information security but is lacking in many organizations. Aside from having management buy-in and a documented incident response plan, one of the most important things an IT or security professional can do is use the best incident response tools to help prepare for and respond to security events.
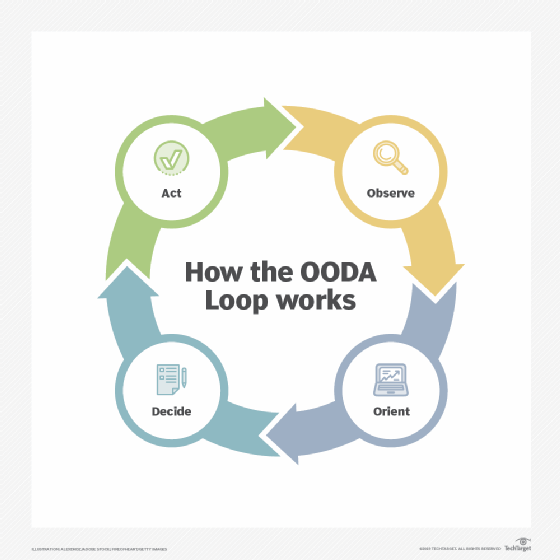
What tools does an organization need? It depends. Certain organizations follow the OODA loop, which can provide guidance on what tools are needed and when. A military-derived approach to incident response, the OODA loop is a methodology that involves following these four steps when confronting a threat:
- Observe. This is the visibility into network traffic, OSes, applications and more, which can help establish a baseline for the environment and provide real-time information into what's happening before, during and after a security event.
- Orient. This is the detailed contextual information and intelligence on the threats that exist and what attacks they're carrying out.
- Decide. This refers to real-time (proactive, happening now) and forensic (reactive, after-the-fact) information on threats and anomalous behaviors that can help security teams make informed decisions on how to respond.
- Act. These are the steps or actions to take to address the threats, minimize their risk to and effect on the business, and bring things back to normal.
The OODA loop isn't a set of incident response requirements, but an approach security teams can integrate with their existing incident procedures to minimize the effect security incidents could have on their organization.
Incident response sets expectations, details how things are done and uses the appropriate technologies to ensure procedures are properly addressed and enforced. This gives guidance on incident response tools and how they can help throughout the incident response process. The security team can use this information when selecting incident response software or services and provide insight into how the organization's overall security program can be improved.
Incident response tools and the OODA loop
Organizations need technologies that provide visibility and control in an automated and repeatable fashion to ensure the network remains resilient and preserves security. This goes for preventative measures, such as multifactor authentication and granular access controls, as well as reactive measures, such as monitoring, alerting and system quarantining.
Multiple tools can assist with response efforts across the OODA loop. Most tools fall into one of the following categories; certain tools can be used in multiple OODA loop phases:
- NetFlow and traffic analysis.
- Vulnerability management.
- SIEM.
- Endpoint detection and response (EDR).
- Security orchestration, automation and response (SOAR).
- Firewall, intrusion prevention systems (IPSes) and DoS mitigation.
- Forensics analysis.
- Awareness and training.
Let's look at each step in the OODA loop and which technologies fit into them.
Observe
This part of the OODA loop requires tools to create a baseline, establish what normal behavior looks like and discover anomalies. Given what's involved, this category encompasses the greatest number of tools:
- Data classification.
- Data loss prevention.
- Cloud access security brokers.
- EDR.
- Antimalware and antivirus.
- IPS.
- NetFlow software.
- Network traffic analysis tools.
- SIEM.
- Vulnerability analysis and management tools.
The more information you have, the better, which is why these types of tools are critical. They help security teams become familiar with their networks and determine what might be at risk before an incident occurs.
Orient
Tools used in this step in the OODA loop provide information and context regarding the severity of security events that have occurred. This helps with the scope and effect, which can lead to better decision-making in the next step. Consider the following tools:
- Threat research.
- Threat intelligence.
- Investigation tools.
- Response tools.
Decide
Incident response tools help security teams reach this step. But this phase of the OODA loop involves people, including security committee or incident response team members, as well as executive management, legal and other stakeholders.
During this step, critical business decisions are made, including what to do or not do in terms of response efforts. The most important piece goes back to the two previous steps -- observing and orienting -- to ensure teams have all the necessary information to make better decisions.
In the decide phase, teams might reference security policies, standards, contracts and compliance requirements to ensure they are doing what they said they were going to. The outcome of this step is coming up with a clear plan for remediation efforts. While there are no specific tools for this step, teams might have to go back and interact with incident response and related security tools, depending on the situation.
Act
This step is where things get done and when teams act on decisions made during the decide phase using incident response and security tools.
Tools used here include the following:
- Antimalware.
- Backup and recovery.
- Forensics evidence gathering and preservation.
- SOAR tools.
- Information and access systems.
- Patch management.
- Security awareness training.
SIEM and vulnerability management tools also might be used to ensure security threats have been eliminated and vulnerabilities addressed. Organizations using a change management system might need to use it to follow internal requirements and document what has been done.
How to choose the right tool for your company's needs
Each organization's incident response needs are unique. But just because an incident response tool seems to fit the bill now doesn't mean it will over the long haul. Many considerations must be made, and questions must be asked before investing time, money and effort into these products. Be sure to understand the challenges and risks the business is trying to address.
Rather than simply procuring incident response tools that may or may not be what the organization needs, the security team must determine what's best for the business. This involves asking questions, such as the following:
- What is the organization trying to accomplish? What requirements need to be met to reach these goals?
- What is the organization required to protect? What is it protecting it from?
- Does the organization need to protect the entire network or just a subset of critical systems?
- What challenges does the business currently have in terms of visibility, control and expertise that could be mitigated by the right tools?
- What type of reporting does the organization need for executive management, audit and so on? Will these tools help the security team meet these requirements?
- How will tools affect the business's current network complexity and security posture? Does the organization have the internal resources necessary to properly implement and administer these tools?
- How will security policies, standards and plans need to be adjusted? How will IT and security workflows and processes need to be adjusted?
- How will the organization measure success? Will the tools themselves help in that regard?
- How will incident response tools complement or hinder vulnerability and penetration testing efforts?
- What is the budget? Will it meet both the upfront and ongoing costs of these tools?
Whether a security team takes the OODA loop approach or not, over time, it will be necessary to tweak incident response tools and overall methodologies. As the security team discovers the patterns and nuances of network traffic and system behaviors, for example, it will need to fine-tune the tools in use to ensure they provide the information needed.
Teams will also need to determine if the data collected helps or hinders incident response decision-making. Teams might need to establish new security standards or adjust security policies and procedures accordingly, as well as update the organization's formal incident response plan as processes and tools evolve.
Top incident response tools to consider
Security teams can help ensure a successful incident response process by asking potential vendors the following questions:
- How will your product or service better protect the organization's network?
- How can your product save the organization time, effort and money?
- What are your product's components? What does each one do?
- Beyond security oversight and incident response, what compliance regulations does your product address?
- Can you provide use cases or specific case studies of how your tool has helped other organizations handle similar cybersecurity incidents?
- What versions of your product are available? Are they on premises or cloud-based?
- How does your company differentiate itself from its competitors?
Teams should ask for reference accounts in the organization's industry and talk to those people directly. They should also seek out trial versions or do an in-depth proof of concept with certain vendors to see how their incident response tool will work in their team's unique environment. Teams should also discuss ongoing support and training with prospective vendors and ask what key partnerships they have in terms of integrating with other security tools. Integrations are beneficial because they can take advantage of the organization's existing security technologies.
Security buyers looking for more information on incident response software and service providers should read our coverage on the following vendors, service providers and tools:
- AT&T Managed Threat Detection and Response.
- AT&T USM Anywhere.
- BAE Systems Incident Response.
- CrowdStrike Falcon Insight XDR.
- Cyderes Enterprise Managed Detection & Response.
- Cynet 360 AutoXDR Platform.
- Cynet CyOps.
- Datadog Cloud SIEM.
- Exabeam Fusion.
- IBM Security QRadar.
- KnowBe4 PhishER.
- LogRhythm SIEM.
- Mandiant Incident Response Services.
- NTT Managed Detection and Response.
- Secureworks Emergency Incident Response.
- Splunk Enterprise Security.
- Sygnia Incident Response.
- Trustwave Managed Detection and Response.
- Verizon Incident Response & Investigation.
- XMatters.
Editor's note: This article was written by Kevin Beaver in 2019. TechTarget editors revised it in 2024 for accuracy and to improve the reader experience.
Kevin Beaver is an independent information security consultant, writer and professional speaker with Atlanta-based Principle Logic LLC. With more than 30 years of experience in the industry, Beaver specializes in performing vulnerability and penetration tests, as well as virtual CISO consulting work.








