What is a next-generation firewall (NGFW)?
A next-generation firewall (NGFW) is a network security device that combines traditional firewall capabilities with advanced features to detect and block sophisticated cyberattacks.
NGFWs are hardware-, software- or cloud-based. They offer traditional firewall features, such as detecting and blocking sophisticated attacks by enforcing security policies at the application, port and protocol levels, as well as the following advanced functions:
- Application awareness.
- Integrated intrusion prevention system (IPS).
- Identity awareness -- enabling user and group control.
- Bridged and routed modes.
- Ability to use external intelligence sources.
- Advanced threat remediation.
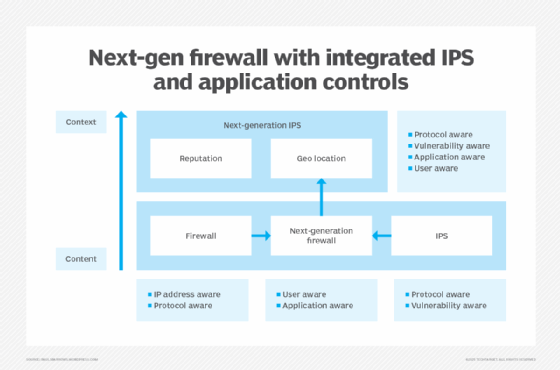
Most NGFWs integrate at least three basic functions: enterprise firewall capabilities, IPS functions and application control.
Like the introduction of stateful inspection in traditional firewalls, NGFWs bring additional context to the firewall's decision-making process. This context enables NGFWs to understand the details of web application traffic passing through them and to take action to block traffic that might exploit vulnerabilities.
Next-generation firewall features
NGFWs combine many of the capabilities of traditional firewalls -- including packet filtering, network address translation (NAT) and port address translation (PAT), URL blocking, and virtual private networks (VPNs) -- with quality of service (QoS) functionality and other features not found in traditional firewalls. These include intrusion prevention, SSL and SSH inspection, deep-packet inspection, reputation-based malware detection and application awareness.
These application-specific capabilities help thwart the growing number of application attacks taking place at Layers 4-7 of the OSI network stack.
Benefits of next-generation firewalls
The different features of NGFWs combine to create unique benefits for users. NGFWs can often block malware before it enters a network, something traditional firewalls could not do.
NGFWs are also better equipped to address advanced persistent threats (APTs) because they can integrate with threat intelligence feeds. NGFWs offer a low-cost option for companies trying to improve basic device security using application awareness, inspection services, protection systems and awareness tools.
Challenges of next-generation firewalls
NGFWs are not without difficulties. They can be complicated to set up and maintain, which could require additional skills and expertise from security teams. They might also create an overload of alerts, including false positives, which puts increased pressure on security admins.
NGFWs need to integrate with other security tools, which can increase complexity and create interoperability issues. NGFWs also require integration and constant updates, for example, with threat intelligence feeds, to combat new and evolving threats. The advanced features of NGFWs can also introduce latency and scalability problems.
Additionally, while NGFWs offer more protection than traditional firewalls, they often have higher acquisition, implementation and operational costs.
Next-generation firewall vs. traditional firewall
While both next-generation and traditional firewalls aim to protect an organization's network and data assets, they have several similarities and differences.
The main similarities include static packet filtering to block packets at the point of interface to network traffic. They also both provide stateful packet inspection, network and port address translations, and both can set up VPN connections.
One of the most important differences between the firewalls is that NGFWs offer deep-packet inspection that goes beyond simple port and protocol inspection by inspecting the data carried in network packets. Other key differences are that NGFWs add application-level inspection, intrusion prevention and the ability to act on data provided by threat intelligence services.
NGFWs extend the traditional firewall functionality of NAT, PAT and VPN support to operate both in routed mode -- in which the firewall behaves as a router -- and in transparent mode -- in which the firewall behaves like a bump in the wire when it scans packets -- while also integrating new threat management technologies.
Editor's note: Informa TechTarget editors revised this definition in 2025 to improve the reader experience.







