What is a computer exploit?
A computer exploit, or exploit, is a program or piece of code developed to take advantage of a vulnerability in a computer or network system. Threat actors commonly use exploits to gain access to target systems, where they might introduce malware or take other actions, usually with malicious intent. When used as a verb, the term exploit refers to the act of successfully carrying out such an attack.
A computer exploit might target software, firmware or hardware. Many exploits take advantage of weaknesses in operating systems, applications or other software, including application plugins and software libraries. Upon learning of a software exploit, the product's vendor will typically issue a fix, or patch, that addresses the vulnerability.
Patches are sometimes applied automatically to software, depending on the type of software and how it's configured. For example, users on the macOS operating system can enable automatic updates on their devices. The OS will check for updates automatically, download them when available, and install them immediately or at a time convenient to the user. Users can also enable automatic updates for applications they install from Apple's App Store.
Not all patches are applied automatically. In some cases, users must specifically check for updates or respond to prompts in the application notifying them when an update is available. In some cases, users must download an update manually from the vendor's website. Failure to install a patch can leave a system vulnerable to exploits and the possibility of a security breach.
Exploits are not limited to software. For example, hackers might develop exploits that target the custom chipsets used in enterprise systems. Specialized chipsets don't always receive the same level of security reviews given to more widely distributed chipsets, so threat actors will specifically target them. Hackers might also target outdated device firmware that contains known security issues, relying on poor patch management practices to exploit the vulnerabilities.
Types of computer exploits
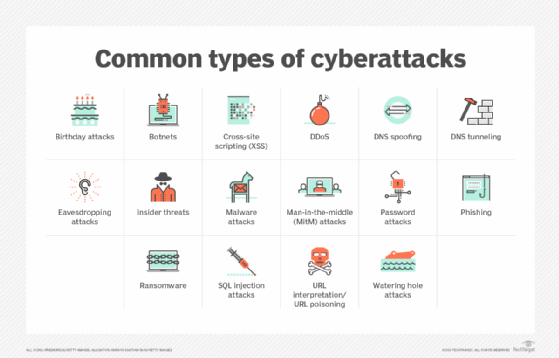
Security exploits come in all shapes and sizes. Although some techniques are used more often than others, threat actors can choose from a wide range of hacking methods. When carrying out their attacks, they might also take advantage of broken authentication code or security misconfigurations. Here's a sampling of some ways hackers might penetrate secure systems:
- Code injection. The insertion of malicious code into an application. The application executes or interprets the code along with legitimate code.
- SQL injection. With SQL injection, malicious code is injected directly into a SQL command, causing the database server to run the code.
- Cross-site scripting. With XSS, malicious code is attached to a trusted website in a way that it causes the user's browser to execute the code.
- Cross-site request forgery. CSRF is often used in conjunction with a social engineering campaign to trick a website's authenticated users to carry out detrimental actions.
- Denial of service. DoS involves flooding a computer or network with overwhelming amounts of traffic, preventing legitimate users from accessing resources or carrying out normal operations.
- Man in the middle. MitM attacks intercept and potentially alter communications between two endpoints, making it possible to capture sensitive data and manipulate outcomes.
Computer exploits can be categorized in multiple ways, depending on how they work and are carried out. For example, exploits might be characterized by the expected result of the attack, such as denial of service, remote code execution, privilege escalation, malware delivery or other malicious goals. They might also be characterized by the type of vulnerability being exploited, including buffer overflow, injectable code, lack of proper input validation, configuration weaknesses and other vulnerabilities
A common approach to categorizing exploits is to group them into two broad categories: known or unknown. A known exploit is one that has been identified, documented and, as is often the case, addressed through a security patch that eliminates the vulnerability. Exploits might be made public by the vendors that own the software, organizations or researchers that specialize in cybersecurity, or even the threat actors who carry out the attacks.
An unknown exploit, also referred to as zero-day exploit, is one that takes advantage of a zero-day vulnerability. A zero-day vulnerability occurs when a piece of software -- usually an application or operating system -- contains a critical security vulnerability of which the vendor is unaware. The vulnerability becomes known only when a hacker is detected exploiting the vulnerability. Once such an exploit occurs, systems running the software are left vulnerable to an attack until the vendor releases a patch to correct the vulnerability and the patch is applied.
How do exploits occur?
Although exploits can occur in a variety of ways, one common method is for threat actors to launch their exploits from malicious websites. The victims might visit such a site by accident, or they might be tricked into clicking on a link to the site through a phishing email or malicious advertisement.
Malicious websites are sometimes configured with exploit kits -- software toolkits containing multiple exploits that target browser vulnerabilities. Cybercriminals might set up a website specifically to deliver an exploit kit, or they might hack into a legitimate website to launch the exploit kit from there. Exploit kits usually target Java-based software, unpatched browsers or browser plugins. They're commonly used to deploy malware onto the victim's computer.
Automated exploits, such as those launched by malicious websites, are often composed of two main components: the exploit code and the shellcode. The exploit code is the software that attempts to exploit a known vulnerability. The shellcode is the exploit's payload that is delivered once the target system is breached. The shellcode gets its name from the fact that some payloads open a command shell to run commands against the target system, although not all shellcode actually opens a command shell.
Famous vulnerabilities and exploits
In recent years, many high-profile exploits have been used to commit massive data breaches and malware attacks. In 2016, Yahoo announced a hack that had occurred years earlier, resulting in a leak of the data of 1 billion users. The attackers gained access to users' email accounts because the passwords were protected by MD5, a weak, outdated hashing algorithm.
A well-known recent exploit is EternalBlue, which seized upon a flaw in Windows Server Message Block, version 1 (SMBv1). The U.S. National Security Agency developed the exploit to gain access to Windows computers. The NSA used it for over five years before it was made public by the Shadow Brokers group. Soon after, Microsoft released a patch for the SMB vulnerability. However, EternalBlue was later used in the WannaCry and NotPetya ransomware attacks, which took advantage of unpatched systems.
In September 2017, credit-reporting firm Equifax announced that it had suffered a massive data breach. Attackers had exploited a critical vulnerability in the Apache Struts framework, which was used in one of the company's web applications. Although a patch had been released earlier that year to address the flaw, Equifax failed to update its web app until after the attackers were detected.
In 2023, Microsoft reported that a Russian-based cybercriminal group, dubbed Storm-0978, exploited a remote code execution vulnerability in Windows Search as part of an espionage phishing campaign and ransomware attack. The group targeted government and defense organizations in North America and Europe.
This year, the Common Vulnerabilities and Exposures (CVE) reference dictionary published CVE-2024-4947, which describes a vulnerability in the Google Chrome browser that permitted a remote attacker to use a crafted HTML page to execute arbitrary code inside a sandbox. Not long after, the CSV published CVE-2024-5274, which details another Chrome vulnerability that permits the execution of arbitrary code inside a sandbox. CVE-2024-5274 is reportedly the fourth zero-day vulnerability Google had to patch in May 2024.
Companies must understand how they're being attacked to stop cybercrime. Learn about 16 common types of cyberattacks and how to prevent them.






