What is operational risk?
Operational risk is the risk of losses caused by flawed or failed processes, policies, systems, people or events that disrupt business operations. Unlike financial and market risks, which stem from external economic factors, operational risk typically arises from within an organization. However, external factors beyond its direct control, such as natural disasters, power outages and cyberattacks, can also trigger operational disruptions and losses.
Employee errors, criminal activity -- such as fraud -- and physical events are among the factors that can trigger operational risk. Most organizations accept that their people and processes will inherently have errors and contribute to ineffective operations. In evaluating operational risk, practical remedial steps should be emphasized to eliminate exposures and ensure successful responses.
If left unaddressed, operational risk can cause monetary loss, competitive disadvantage, employee- or customer-related problems, business risks and business failure.
What are the types of operational risks?
Operational risks are categorized into types based on where they come from. Each poses unique challenges for organizations. Here are some key types:
- Process risks. Failures or insufficiencies of internal controls, processes or procedures cause these risks. Examples include incorrect invoice processing, incomplete compliance procedures and errors in order fulfillment or quality checks.
- People risks. These refer to potential losses resulting from human error, fraud, negligence and misconduct. Examples include employee fraud and other insider threats, vendor contract breaches, inadequate training and supervision, and reporting errors.
- Systems risks. These risks arise from failures or disruptions in IT systems or infrastructure. Examples include server outages, software bugs, failed data backups and loss of data integrity.
- Financial risks. This refers to monetary losses resulting from financial and business decisions that hinder an organization's ability to maintain sustainable business operations. Examples include cash flow shortages, ineffective investment strategies and counterparties failing to meet their financial obligations.
- External risks. These risks are threats and disruptions that originate from sources outside an organization's direct control. They include natural disasters, such as earthquakes, floods, hurricanes and pandemics. They also come from political and geopolitical external events, such as government policy changes, economic sanctions, civil unrest and disruptions affecting international stability.

- Supply chain risks. Third-party risks arise from dependence on vendors, partners and suppliers in the extended supply chain. Examples include vendor failures or delays, third-party data breaches and poor service delivery from outsourced partners.
- Legal and compliance risks. Potential breaches of law, regulations or internal policies cause these risks. Examples include regulatory sanctions, penalties for noncompliance with privacy laws and lawsuits stemming from contractual breaches.
What are the main sources of operational risk?
Operational risks arise from various sources and are typically categorized into four areas:
- People. Human error, fraud, inadequate training or poor decision-making can lead to operational failures.
- Processes. Inefficient, outdated or poorly designed workflows can result in delays, compliance issues or financial losses.
- Systems. Technology failures, cybersecurity breaches or software malfunctions can disrupt business operations.
- External events. Natural disasters, geopolitical instability, regulatory changes and supply chain disruptions are all events outside an organization that can affect business continuity.
What are the causes of operational risk?
The bigger categories of operational risk sources are people, processes, systems and external events, as previously mentioned. Within those categories, there are numerous specific causes of operational risks, such as the following:
- Natural disasters, such as earthquakes, hurricanes and wildfires.
- Worldwide health crises, such as the COVID-19 pandemic.
- Human-made disasters, such as terrorism, cyberterrorism and cybercrime.
- Embezzlement, insider trading, insider cybercrime, negligence and other workplace-related issues, such as sexual harassment, a hostile work environment and discrimination.
- Regulatory compliance violations, breach of contract, antitrust, market manipulation and unfair trade practices.
- Laws or regulatory requirements, such as the California Consumer Privacy Act and the European Union's General Data Protection Regulation.
- Failure to adhere to the company's policies or procedures or, conversely, a failure to enforce policies.
- Outdated or unpatched IT systems and software.
- Supply chain disruptions.
- Inefficient cloud use.
- Unfair or inconsistent work policies.
- Unsafe practices.
- Product defects.
- Human errors, such as data entry errors or a missed deadline.
- Poorly conceived or inefficient internal processes.
Examples of operational risks
The causes of operational risks discussed previously can result in the following outcomes:
- Enterprise-wide interruption, disruption or failure.
- Loss of systems control or data.
- Financial loss, including insurance claim denial.
- Safety hazards.
- Reputational damage.
- IT infrastructure damage.
- Customer churn.
- Employee churn.
- Employee shortage.
- Legal liability or regulatory fines for employees intentionally or negligently causing harm.
- Legal liability or regulatory fines for external bad actors causing harm.
- Competitive disadvantage.
- Lack of long-term business continuity.
- Loss of business licenses in financial services.
How is operational risk measured?
Two things are generally required to measure operational risk: key risk indicators (KRIs) and data. Measurement, however, can be especially challenging when organizations are unable to integrate all the diverse types of data required to understand the organization's operational risk. This might be due to the absence of software that collects and analyzes data from different systems or to organizational fiefdoms that cause data silos, among other factors.
As organizations become increasingly digital and use more data, operational risk managers should continually monitor and assess risks in real time to minimize their potential effects.
What KRIs should businesses track? That depends on the industry in which they operate. For example, banks follow guidance from the Basel Committee on Banking Supervision, which lays out approaches for measuring operational risk and requires banks to allocate a certain amount of capital to cover losses from operational risk.
There are several ways companies can measure operational risk, though they aren't all ideal. They include the following:
- Monitoring KRIs.
- Using statistical techniques.
- Using scorecards.
- Performing scenario analyses in cooperation with risk management experts and line-of-business experts to evaluate the cost and probability of specific risks.
- Monitoring customer complaints.
- Internal evaluations where employees identify and assess risks within their departments.
- Examining regulatory fines from intentionally -- or, more likely, inadvertently -- failing to report or violating a mandate.
- Assessing brand reputational damage caused by the risk, such as a data leak or breach that exposes customer data to unauthorized parties.
- Modeling hypothetical risk events to understand their potential effects.
Basel III event categories
Basel III was developed in direct response to the 2008 financial crisis and went into effect in January 2023. It continues to refine regulations that strengthen the banking industry. Among these are the adoption of minimum capital requirements, new risk monitoring and review standards, and new use and liquidity requirements that aim to protect banks against risky lending practices.
Here are the seven categories of operational risk laid out in Basel III that help financial institutions classify and manage risks:
- Internal fraud. Misappropriation of assets, tax evasion, intentional mismarking of positions and bribery.
- External fraud. Theft of information, hacking damage, third-party theft and forgery.
- Employment practices and workplace safety. Discrimination, workers' compensation, and employee health and safety.
- Clients, products and business practice. Market manipulation, antitrust, improper trade, product defects, fiduciary breaches and account churning.
- Damage to physical assets. Natural disasters, terrorism and vandalism.
- Business disruption and systems failures. Utility disruptions, software failures and hardware failures.
- Execution, delivery and process management. Data entry errors, accounting errors, failed mandatory reporting and negligent loss of client assets.
Basel II was the predecessor of Basel III and was initially published in 2004 as a set of international banking regulations. Basel IV, also known as Basel III Endgame or Basel 3.1, is an enhancement to Basel III. It's currently being phased in and is set for full adoption by 2027.
How to identify and manage operational risk
Identifying and managing operational risk involves a structured approach to assessing vulnerabilities and practicing mitigation strategies. Here's a breakdown of the key steps most organizations should follow to identify and mitigate risk.
1. Risk identification
Operational risk management begins with identifying potential threats that might disrupt business strategy and objectives. Organizations should assess internal workflows, such as production, IT, human resources and customer service, to identify vulnerabilities. They also need to analyze historical incidents, including financial losses, data breaches and compliance violations, to recognize risk patterns.
Employee engagement through workshops and interviews also provides valuable insights into potential threats and past experiences. In addition, external factors -- such as industry trends, regulatory shifts, technological advancements and geopolitical issues -- must be monitored for emerging risks.
Scenario planning further aids in identifying possible disruptions and assessing organizational resilience to ensure a proactive approach to risk mitigation and preparedness.
2. Risk assessment
Risk assessment is a structured approach to evaluating risks based on their likelihood and potential effect. The process results in a prioritized list of identified risks that assigns ownership and outlines mitigation strategies in a risk register.
The risk assessment process could resemble an internal audit and should be guided by past audit findings for greater accuracy and strategic decision-making.
3. Risk mitigation
Risk mitigation involves addressing identified risks through four approaches:
- Transfer. Transferring risk shifts responsibility to another entity through mechanisms such as outsourcing or insurance. Responsibility can't be fully transferred. For example, cloud software contracts often include data breach insurance; vendors, on the other hand, usually provide System and Organization Controls reports to ensure security.
- Avoid. Avoidance strategies purposely steer clear of high-risk situations, such as selecting a more expensive but reliable vendor over a cheaper, unproven alternative.
- Accept. Acceptance weighs the cost of control against potential risks, such as installing new coffee makers despite the minor risk of burns, to prioritize employee satisfaction.
- Mitigate. Mitigation reduces risk likelihood by enforcing safeguards, such as using virtual private networks to prevent data leaks in remote work environments.
4. Control execution
After selecting risk mitigation strategies, controls are tailored to address specific risks. These controls, such as process adjustments, additional approvals and built-in safeguards, should be formally documented to ensure clarity and execution.
Whenever possible, preventive controls should take precedence, though detection measures might be necessary for risks that can't be fully prevented.
5. Ongoing control monitoring
Control monitoring evaluates the effectiveness and design of risk controls, ensuring any exceptions or weaknesses are promptly reported to management with corrective action plans.
Many organizations use continuous monitoring and KRIs to detect rising risk exposure, often through business intelligence tools. While banks commonly use KRIs for operational risk, they apply across industries, such as tracking customer satisfaction scores to identify training gaps or service inefficiencies early.
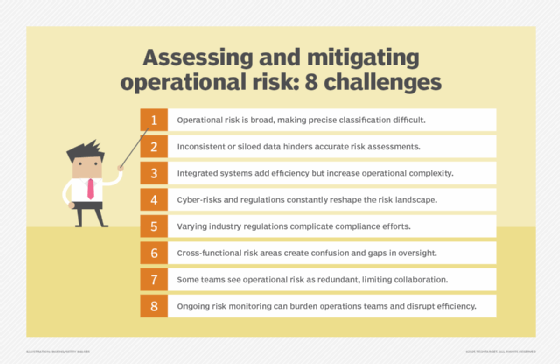
Challenges with assessing operational risk
Assessing and managing operational risk can be difficult due to its complex and often qualitative nature. The key challenges faced by organizations when assessing operational risk include the following:
- Defining scope and boundaries. Operational risk covers many factors, from human error to system failures. Because of its broad definition, pinpointing its exact scope can be difficult. Organizations might struggle to clearly distinguish operational risk from related risk categories, such as strategic risk or reputational risk. This situation can lead to overlaps in responsibilities or gaps in risk assessments.
- Incomplete or inaccurate data. The data required to assess operational risk isn't always available or accurate. Internal loss data might fail to capture near misses or external events, while information is often siloed or inconsistently reported across departments. Incomplete or inconsistent historical records complicate efforts to predict future risks with precision.
- Operational complexities. Operational complexity is growing in enterprises. Most organizations rely on integrated systems, such as enterprise resource planning platforms, cloud services and third-party application programming interfaces. While these technologies drive efficiency, they also introduce new layers of complexity, and failure in one component can cascade across the organization.
- Evolving threat landscape. According to the April 2024 Global Financial Stability report by the International Monetary Fund, the risk of extreme losses from cybersecurity incidents is rising. Emerging cyberthreats and regulatory changes constantly reshape the operational risk landscape. Organizations that rely on outdated risk assessment models might find themselves ill-equipped to respond to unforeseen challenges. Additionally, the expanding universe of operational risk types, such as risks linked to AI governance, remote workforce management and environmental factors, further complicates the assessment process.
- Compliance and regulatory challenges. Compliance requirements vary across industries and jurisdictions. Keeping up with evolving regulatory standards could also add more complexity to operational risk assessment.
- Overlapping risk functions. Because operational risk touches multiple areas within an organization, it frequently overlaps with other risk functions. This broadening definition can create internal friction, particularly when different teams perceive their responsibilities as duplicative. Risk management groups, such as compliance, cybersecurity and financial risk teams, might resist collaboration if they feel their roles are being encroached upon. A lack of clarity on ownership can lead to inefficiencies or gaps in risk oversight.
- Resistance from other risk functions. If operational risk assessments are perceived as interfering with established processes, risk owners might be reluctant to cooperate. This lack of alignment can hinder the organization's ability to build a holistic risk assessment framework and address risk, leaving operational vulnerabilities unaddressed.
- Burdensome monitoring and reporting. Operational risk assessment often requires ongoing monitoring and reporting, which operations teams can view as a burden. Employees responsible for managing daily processes might find that risk tracking takes time away from their core responsibilities. This pushback can lead to inconsistencies in data collection or reluctance to engage in proactive risk management practices.
Traditional risk management and enterprise risk management both protect organizations from potential threats, but they differ in their approach and scope. Discover the key differences between traditional and enterprise risk management and how each strategy shapes organizational resilience.






