software patch
What is a software patch?
A software patch or fix is a quick-repair job for a piece of programming designed to resolve functionality issues, improve security or add new features.
Throughout its lifetime, software will run into problems called bugs. A patch is the immediate fix to those problems. IT or end users can often download a patch from the software vendor's website. But the patch isn't necessarily the best fix for the problem, and the product's developers will often incorporate a more complete remediation when they do the next upgrade or full release of the software.
The creator of the patch usually develops and distributes it as a replacement for, or an insertion in, compiled code -- that is, in a binary file or object module. Larger operating systems (OSes) often provide a special program to help IT manage and track patch installations. The collective effort within an organization to identify, schedule and distribute patches is known as patch management.
Types of software patches
Software patches generally fall into three categories. A single patch can fall into more than one category, however. These software updates include bug fixes, security updates and feature updates:
- Bug fix patches. These correct problems in the software, help the software run more smoothly and reduce the likelihood of a crash.
- Security patches. These address known security vulnerabilities, making the software more secure.
- Feature patches. These add new functionality to the software. For example, Microsoft, at one time provided feature updates twice a year for the Windows 10 OS.
How patching works in different devices
Software patches are platform dependent. A patch for a PC application wouldn't be suitable for use on a device running Apple iOS. Given the variety of device types in most organizations, it's common to use an automated patch management tool that supports PCs and a variety of mobile OSes.
This practice is commonly referred to as centralized patch management. An IT asset management tool is used to identify devices that require patches, assess their patching status and then distribute patches to relevant devices. This tool can also create reports so IT departments can keep track of patches over time.
Why patches are important
Bug fix patches resolve functionality issues and are a key part of vulnerability management. Feature updates give the software additional capabilities.

A security patch is particularly important because it addresses known security risks and vulnerabilities. When a vendor releases a security update, it alerts the hacker community that a vulnerability exists in that piece of software. At that point, hackers begin actively looking for ways to exploit the known vulnerability and for unpatched copies of the software to exploit. The sooner an organization installs a security patch, the faster it's protected against the associated vulnerability.
How to find out what software patches to install
Vendors often offer information on software patches and updates for their applications and devices. Devices can have patch updates appear under a settings option that a user can easily access or that includes a pop-up alert. An application might be programmed to automatically install or check for updates, and some vendors give their customers the choice to receive them automatically. Notifications also play a crucial role in reminding users of patches that need to be installed.
In the case of optional updates, such as enhancements to functionalities and new features, a user can search a vendor's website to find them. Checking a vendor's website ensures an update is retrieved from a trusted source and not an untrusted one, such as an unsolicited email. Verified websites will have detailed information on the update to determine its veracity and also might have other users' feedback to point out any issues.
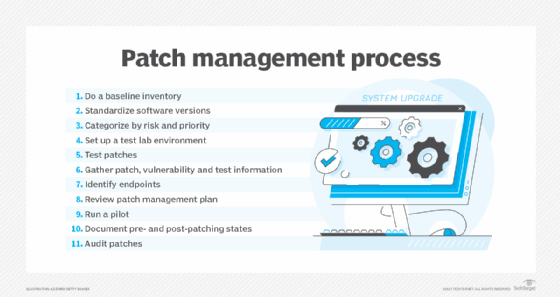
Patch management best practices
There are various best practices for patch management. They include the following:
- Scheduling. Admins should set schedules that ensure new patches are regularly identified and applied quickly.
- Collaboration. Different technical teams, such as cybersecurity and software engineering groups, should work in tandem to implement patches and decide which technologies and procedures are used. Every person involved should be delegated clear roles and responsibilities.
- Disaster recovery workflows. Update management processes might run into issues in the event of downtime caused by outages or connectivity issues. Disaster recovery workflows are key to knowing what the backup plans are in these instances.
- Automation. Patch management software can be set to do automatic updates, simplifying patch distribution to various apps and devices an organization uses. Automatic deployments of patch updates can be performed weekly or more or less frequently, depending on an organization's needs.
- Patch prioritization. When there are many patches required, prioritizing critical updates first reduces the likelihood of cyberattacks such as malware or ransomware or other security breaches.
- Management flexibility. Admins typically want to administer new patches in a timely manner. However, if applying patches interferes with employees' work, admins must be flexible so employees can complete critical tasks first before deploying patches. This, along with many other considerations, should be reflected in their security policies.
- Testing patches. Testing must be performed rigorously to ensure patches don't present issues or cause disruptions.
The difference between manual and automatic updates
The difference between automatic updates and manual ones revolves around both efficiency and the amount of control or customization that developers have over each. Automatic updates require little thought or effort on the part of developers. However, there's a potential for them to end up proving to be unnecessary or even detrimental if applied incorrectly without supervision. While modern OSes typically offer the capability to automatically apply updates, development teams might choose to perform certain ones manually.
With a manual update, a person controls the process. They're usually used when there is an overriding reason to have that control. For instance, manual updates are used when feature updates need to be tailored to the way a system is set up and to avoid compatibility issues.
The downside of a manual patch management process is that the person doing the update has to search for and take the time to perform the update. The automatic approach, on the other hand, is better for security updates to ensure important updates happen quickly enough to prevent vulnerabilities from being exploited.
Patch management policies and patch automation software
Many organizations have patch management policies that stipulate how to evaluate and apply patches. Such policies usually designate the time frame within which IT must apply the patch and how to test the patch to ensure it won't cause problems -- such as compatibility issues -- for the organization.
There are numerous options for automating patch management. Microsoft, for example, provides a free tool called the Windows Server Update Services (WSUS), which automates patch management for Microsoft software.
Windows Update, a free maintenance and support service, can automatically download and install patches for the Windows OS and other Microsoft software. However, there are some advantages to using WSUS. For instance, WSUS gives administrators control over which patches Windows Update applies. It also saves internet bandwidth, because it downloads each patch once and then distributes it throughout the organization, as opposed to each PC downloading it individually.
WSUS is only capable of managing patches for Microsoft products. Microsoft and various third-party applications offer other patch management options that can automate the patching processes of non-Microsoft software.
IT's role in distributing patches
IT departments must regularly monitor communications from their application and device vendors for patching alerts. IT is responsible for patch testing and distribution. It also performs periodic audits to determine if any devices are missing patches. Some organizations outsource these tasks to a managed service provider.
Patch managers must be aware of how the update process could disrupt business operations. They should prioritize patches, applying the critical ones quickly while strategically scheduling less critical patches.
Software platforms generally automate patch management. However, if this automation software stops functioning for some reason, IT would have to step in and fulfill this role. Effective workflows should document these emergency procedures with clear roles for IT departments. Finally, if issues arise with patches, IT must oversee troubleshooting them.
Organizations looking for new ways to simplify and streamline patch management have many platform options. Explore these platforms in detail.






