
kras99 - stock.adobe.com
Kali vs. ParrotOS: Security-focused Linux distros compared
Network security doesn't always require expensive software. Two Linux distributions -- Kali Linux and ParrotOS -- can help enterprises fill in their security gaps.
It's a wonderful time to be a Linux user: Today's distributions are full-featured, powerful and stable. From graphic design to student use to massive cloud VM hosts, Linux plays many roles in the modern IT landscape. How can a single distribution distinguish itself in such a competitive world? One way is through specialization and focus, and that's exactly the formula Kali Linux and ParrotOS have embraced.
If you currently hold a security-oriented role at your organization, each of these distributions warrants a close look. If you're an end user in today's world of identity theft and privacy violations, ParrotOS is especially intriguing.
Let's examine and compare these two security and privacy distros to help you decide which -- Kali Linux vs. ParrotOS -- is best for your use case.
In a nutshell, Kali Linux, focusing on penetration testing, audits and forensics, is one of the industry's best-known and respected security distributions. ParrotOS is an attractive option for privacy-minded end users.
Note that neither Kali Linux nor ParrotOS Security Edition is designed for new Linux users. They are purpose-specific distributions and assume a high degree of knowledge about the OS itself. More user-friendly choices for newer users include Ubuntu, Fedora Linux and Linux Mint. Consider one of these as your Linux daily driver, reserving your Kali or ParrotOS laptop for pen testing. BlackArch Linux is another great security choice.
Introducing Kali Linux
Kali Linux evolved from BackTrack, a Debian-based distro. It provides security professionals with more than 600 pre-installed pen test, forensics, testing and vulnerability scanning utilities. As with all open source software, you can use a Linux package manager to modify Kali as you see fit.
Let's examine how to use the distro.
Key features and tools in Kali Linux
One of Kali Linux's most important features is its preinstalled tool set. This approach saves users time by eliminating the need to construct a Linux distribution and manually install numerous tools. The deployment team also handles dependencies and configurations.
Specific Kali Linux features include the following:
- Debian-based architecture that is built on a standard, well-known and well-supported distribution.
- Flexible multiplatform support.
- Customizability for specific roles.
- Regular updates.
Kali Linux organizes its install applications by function, with the following categories as examples:
- Information gathering, including Nmap, theHarvester and WhatWeb.
- Vulnerability scanning, including Nikto and Lynis.
- Exploitation utilities, including Metasploit Framework.
- Wireless testing and attack tools, including Aircrack-ng and wifite.
- Password crackers, including John the Ripper, hashcat and Hydra.
- Network utilities, including netcat, tcpdump and Wireshark.
Install Kali
Kali is multiplatform, offering users a variety of deployment options, including the following:
- Installer images for bare-metal installations.
- VMs for virtualized environments.
- Mobile for Android devices.
- Cloud.
- Containers -- a portion of Kali's functionality is accessible via small portable containers.
- Live Boot -- Kali can be deployed without harming or replacing existing OSes.
- Windows Subsystem for Linux support.
- Arm processors -- flexible deployment on small appliance devices and modern systems.
Most users likely deploy Kali from bare-metal installer images or VMs. Pre-built images exist for VMware, Hyper-V, QEMU and VirtualBox. Other deployment options include Raspberry Pi, AWS, Azure, Docker and USB-based live boots.
Kali harnesses its open source roots. You can view and use the build scripts directly from GitLab, or if you have a specific need, you can add it to existing build scripts to construct your own version of Kali that works for you.
Kali documentation and community
Join the official Kali forum to discuss issues, ask or answer questions, and learn more about the tools. The community supports a Discord channel to chat with other Kali enthusiasts and developers. Kali also uses various social media channels -- among them Mastodon -- to communicate with users.
Kali documentation, meanwhile, is available on the official site. It's well organized in searchable categories, covering everything from containers to general information on specific tools.
For example, you might want to learn how to use Flatpak or snapd to manage software packages.
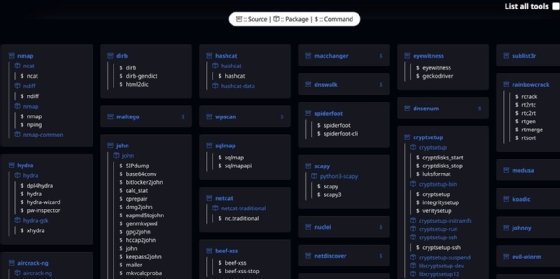
Kali provides an additional tool list that is far more comprehensive. It displays each of the 600-plus utilities that ship with Kali, organizing them by package so you can see how they're related. Each tool is linked to a main page that provides options, examples and use cases.
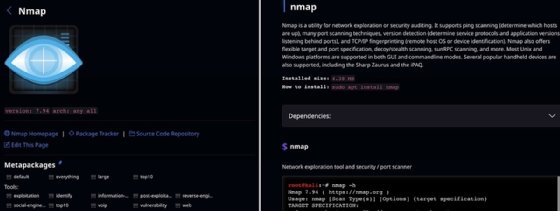
For example, Kali's Nmap entry has information about the network reconnaissance and security auditing tool.
What can you do with Kali?
Kali, with its laser-sharp focus, lets you dive deeply into the mysterious world of pen testing and hacker tools. It shouldn't be your distribution of choice for gaming or graphic design, but it's a great option for learning about today's most essential security tools, conducting security audits, and running penetration testing exercises in your environment.
Kali is a pretty simple choice for security professionals. Remember that Kali is not designed for those new to Linux. It assumes you're comfortable with the OS, CLI, software management, privilege management and other standard tasks.
Consider the Kali training site and the corresponding Kali Linux Revealed training and certification. Many options exist to help users learn more about Kali and its pre-installed tools.
Introducing ParrotOS
ParrotOS focuses on three areas: privacy, security and development. Most ParrotOS versions --encompassing security tools, privacy features and performance enhancements -- run on a variety of hardware and virtualization platforms. Like most Linux distributions, customization and freedom are key.
ParrotOS, created in 2013, is currently on version 6.3. It ships with more than 600 security and development tools. It might appear overwhelming, but ParrotOS boasts an active user community and strong documentation.
Key features and tools of ParrotOS
ParrotOS includes many standard features that make it attractive to security professionals and privacy-conscious users, including the following:
- Hardened kernel.
- Privacy-by-default settings.
- Disk encryption.
- Built-in developer tools.
Like Kali Linux, ParrotOS contains more than 600 pre-installed privacy and security tools. Examples include the following:
- Metasploit.
- Burp Suite to scan for web application vulnerabilities.
- Aircrack-ng to audit wireless networks.
- Wireshark to intercept network traffic.
- John the Ripper and Johnny to audit passwords.
- AnonSurf to route web surfing through TOR.
Choose a ParrotOS edition
ParrotOS comes in various flavors tailored to meet your specific needs. Begin by considering the available deployment categories, then select from among specific options within them.
The three primary categories are:
- Live. The complete OS, enabling a traditional installation or running from removable media without requiring a local installation. Includes Security, Home and Hack the Box (HTB) editions.
- Virtual. Optimized for VMware, VirtualBox and UTM virtualization environments. Includes Security and Home editions.
- IoT. Runs on Raspberry Pi 3, 4 and 5 hardware. Security, Home and Core editions.
Alternate categories include the following:
- Docker. Prepackaged Docker image. Security, Home and Core editions.
- Debian conversion script. Converts an existing Debian installation to ParrotOS. Security, Home and Core editions.
- WSL. Windows Subsystem for Linux deployment with growing support.
Within the categories are the following editions:
- Security. Designed for pen testing with the appropriate library of tools. It's probably not a great choice for day-to-day computing activities.
- Home. Emphasizes privacy and development for standard use, although you can install additional pen testing tools.
- HTB. Uses Pwnbox, a specialized version of ParrotOS, to provide a complete hacker tool set to attack HTB's cloud lab machines.
- Core. Contains only the base packages, enabling you to customize the installation from the ground up.

All editions include privacy, security and development features.
Install ParrotOS
Parrot offers a variety of installation options. Download the version you want, boot the system -- physical or virtual -- from the installation media and follow the installation wizard.
The installation documentation offers detailed guides for many deployment choices, including the following:
- Standard installation.
- Dual-booting with other OSes.
- Raspberry Pi.
- Virtualization platforms -- unified threat management on macOS, VirtualBox and VMware.
- Docker images.
With so many editions and virtualization and cloud choices, hardware requirements differ widely. Like other Linux distributions, ParrotOS runs on standard hardware platforms and offers backward compatibility with older hardware.
ParrotOS documentation and community
ParrotOS offers comprehensive, well-organized and straightforward installation and deployment information. It is powerful enough for expert pen testers, but its documentation is simple enough to appeal to new Linux users as well.
Parrot documentation also contains configuration information for working with a few core OS components, among them AppArmor, Nvidia GPU drivers and assistive technologies that permit users to customize ParrotOS' on-screen keyboard. Nmap and Wget information is also available.
Other sources of information include the ParrotOS blog and GitLab's open source repository for ParrotOS. Be sure to check for the most current information on packages, bugs, upcoming features and other developments.
What can you do with ParrotOS?
ParrotOS' feature set depends on the edition installed. Security Edition is most similar to Kali and is the likely choice for security pros. It assumes a high degree of comfort with basic Linux tasks, such as privilege elevation, data management, software management and networking. Home Edition is great for end users and might be a good place to start for day-to-day tasks, especially if you're new to Linux.
ParrotOS is also pitched as a viable developer platform, meaning it's not just oriented toward security professionals. It includes many built-in developer tools, and its privacy settings might be attractive to those creating applications in security-sensitive environments.
Kali Linux vs. ParrotOS: Compared
When comparing these two platforms, consider the following attributes:
| Kali Linux |
ParrotOS |
|
| Origin |
Developed by Offensive Security |
Developed by the ParrotOS community and led by the ParrotOS Security Team |
| Reputation and perception |
Required by many certification exams, well-known in the industry |
Less well-known |
| Target audience |
Advanced and professional users, including those pursuing security certifications |
Beginner to advanced users, depending on the edition |
| Available editions |
One edition with older versions readily available |
Multiple editions tailored by use |
| Default desktop |
Gnome, with options for KDE, Xfce, etc. |
MATE, with options for KDE, Xfce, etc. |
| Customization options |
Fewer available options due to its focus on professional security roles |
Additional options to enable day-to-day functionality for standard users |
| Performance and hardware requirements |
Heavier requirements, benefitting from good hardware |
Less stringent requirements and flexible for older systems |
Kali Linux and ParrotOS: Get started with both distros
Now that you're familiar with both distributions, let's get started using them.
First, download both distros and install them on VMs. I find VMs are the easiest way to work with new distributions, although you certainly can use the software on Raspberry Pi devices and standard installations. I suggest the ParrotOS Security version if you're also experimenting with Kali.
Once installed, here are a few exercises to get you rolling:
- Find a port scanner and conduct a scan of your local network.
- Look for a packet sniffer and capture some network traffic.
- Conduct a wireless scan to understand the wireless networks around you.
- Begin gathering information using open source intelligence tools.
- Begin integrating the OS into your daily security auditing tasks.
While you might already know -- or can guess -- what tools are likely installed for these tasks, searching around the two systems helps familiarize you with their layout and capabilities.
The secret to using Kali Linux or ParrotOS is to find the best tool for the job you intend to do. In this situation, Kali Linux is only designed to do one thing -- and it does it well. The ParrotOS Security version is certainly competitive. Parrot's Home option, however, provides standard users and developers with the privacy settings and nontracking features many of us want these days. That means your first question has to be: "Am I trying to do pen testing or security audits, or am I a regular user who does not want to be tracked?"
Editor's note: It is possible to use Kali Linux and ParrotOS both lawfully and unlawfully. It is up to you to ensure your usage is lawful. Get appropriate permission and approval before attempting a test, and handle the information obtained ethically. If you are unsure whether your usage is lawful, do not proceed until you have confirmed that it is -- for example, by discussing and validating your planned usage with your organization's counsel.
Damon Garn owns Cogspinner Coaction and provides freelance IT writing and editing services. He has written multiple CompTIA study guides, including the Linux+, Cloud Essentials+ and Server+ guides, and contributes extensively to TechTarget and CompTIA Blogs.






