cloud encryption
What is cloud encryption?
Cloud encryption is a service cloud storage providers offer whereby a customer's data is transformed using encryption algorithms from plaintext into ciphertext and stored in the cloud. Encrypted data is unreadable and essentially meaningless without its decryption key even when the data is lost, stolen or breached through unauthorized access.
Cloud encryption is almost identical to on-premises encryption with one important difference: the cloud customer must take time to learn about the provider's policies and procedures for encryption and encryption key management. A service provider's cloud encryption capabilities must match the level of sensitivity of the data being hosted.
IT admins regard data encryption as an ultimate safeguard to ensure the security of data. It's the confidentiality piece in the confidentiality, integrity and availability triad and mandated in many compliance and regulatory standards, such as Federal Information Processing Standards (FIPS), the Federal Information Security Modernization Act, the Health Insurance Portability and Accountability Act (HIPAA) and the Payment Card Industry Data Security Standard (PCI DSS).
How does cloud encryption work?
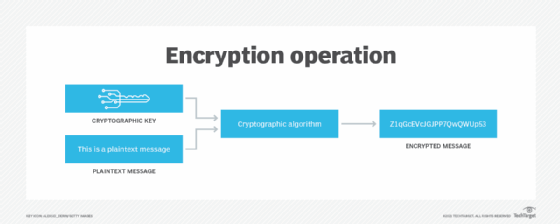
Cloud encryption platforms encrypt data when it's transmitted to and from cloud applications and cloud storage, as well as to authorized users in different locations. In addition, these tools encrypt data when it's stored on cloud-based storage devices. These measures prevent unauthorized users from reading data in motion as it travels to and from the cloud as well as files when they're saved in cloud storage.
This article is part of
What is cloud security management? Guide and best practices
Storage vendors, such as AWS, Dropbox, Google Cloud and Microsoft Azure, provide data-at-rest cloud encryption. The software handles encryption key exchanges and the encryption and decryption processes in the background, so users don't have to take any additional steps beyond having proper authorization and authentication to access data.
The process organizations follow to implement and maintain cloud encryption measures, includes the following steps:
- Assess needs. Organizations must assess how much sensitive information will be transmitted or stored and what security measures will be needed.
- Evaluate providers. The next step in the process is to evaluate providers selling cloud encryption tools to ensure the correct one is chosen.
- Implement client-side encryption. The first aspect to cover during implementation is client-side encryption, to ensure data is secure before it is transmitted.
- Secure encryption keys. This next aspect to cover ensures encryption keys are safe and adequately managed.
- Protect data in transit. Data must be actively protected when it travels between the client and the cloud provider.
- Train users. Employees must be trained to use cloud encryption systems correctly for compliance and to prevent liabilities to the organization.
- Monitor and maintain implemented systems. Once implemented, continuous upkeep is needed, which includes testing to ensure everything continues working properly and is up to date.
Benefits of cloud encryption
Cloud encryption offers numerous benefits for businesses relying on cloud storage services, including the following:
- Data security. Cloud encryption is a preemptive defense against data breaches and cyberattacks. With end-to-end data protection, threats are prevented whether data is at rest in a cloud storage platform or being transmitted between users.
- Fostering collaboration. Cloud encryption allows enterprises and their customers or clients to take advantage of the benefits of cloud collaboration services without putting data at unnecessary risk. Authorized users can share encrypted data without worrying about data breaches or cyber attackers.
- Ensuring authenticity and integrity. End-to-end encryption prevents unauthorized or malicious attempts to modify data, thereby ensuring data remains authentic whether it is residing on a storage resource or in transit.
- Compliance. Cloud encryption satisfies many customer and regulatory requirements for data privacy and security, such as those stipulated by HIPAA, FIPS and PCI DSS.
Cloud encryption challenges
It is important for data managers to be aware of common cloud encryption challenges. The main challenges organizations can encounter include the following:
- Performance and integration complexities. In the past, performance and integration concerns have deterred many from implementing encryption as a standard practice because it's often seen as too complicated or annoying for users who need to frequently access files from a variety of devices and locations. While today's systems are faster and easier to use, it's still important to trial run any platform to ensure it meets integration and usability requirements.
- Resource consumption. The encryption process is resource-intensive and adds time and money to everyday activities. As a result, it's important to monitor access times and resource usage levels.
- Risk of encryption key loss. The loss of encryption keys can render encrypted data useless; poor or inadequate encryption key management can put critical data at risk.
- Configuration. The biggest challenge is ensuring that the cloud encryption services are correctly configured. A dangerous gap in any data security strategy can occur when admins think data is encrypted, but configuration issues leave it unencrypted and vulnerable.
What are the two types of cloud encryption?
The two types of cloud encryption are symmetric and asymmetric encryption. Enterprises often use a combination of these two encryption methods to build a more comprehensive approach to cloud security.
Symmetric encryption
In symmetric encryption, a single key is used to encrypt plaintext and decrypt ciphertext. This approach is seen as beneficial due to its simplicity and speed. Additionally, specific symmetric encryption models such as the Advanced Encryption Standard are complex and difficult to hack. However, the downside is that if symmetric encryption is hacked and a cyberattacker gains unauthorized access to the encryption key, they can use it to expose and steal sensitive data.

Asymmetric encryption
The second approach to cloud encryption is asymmetric encryption, where sensitive information is encoded with a public key and then decoded by a separate private key. This obviously adds layers of security to cloud data, especially since private keys never need to be transmitted in a way that hackers could intercept and steal them. The drawback here is that the process isn't as quick and easy as symmetric encryption. Examples of asymmetric encryption include elliptic curve cryptography and the Digital Signature Standard.
Cloud encryption best practices
Security teams should map out the security requirements for any data that moves to and from the cloud to ensure continued compliance with the enterprise's security policy. This will help identify cloud providers that offer sufficient encryption options and services. Security teams need to answer the following three questions:
- What data requires encryption based on its data classification and regulatory compliance requirements?
- When does the data need encryption -- in transit, at rest and in use?
- Who should hold the encryption keys -- the cloud service provider or the enterprise?
All data in transit must be encrypted whenever it leaves an internal network, because it will invariably pass through an unspecified number of third parties. Sensitive data should be encrypted even during internal transmission. While most data in transit can be securely handled natively in web browsers and File Transfer Protocol software, it's imperative that all connections use a secure protocol. For example, data encrypted using HTTPS is protected by a secure sockets layer.
Virtual private networks and Internet Protocol security are other ways of providing protection for data-in-transit, but they also add complexity. Cloud access security broker tools provide security managers with a unified way to control and manage cloud resources and ensure users access them in accordance with the organization's security policies.
Sensitive data uploaded to the cloud should be encrypted on premises and backed up prior to its transfer to the cloud service. This ensures data will always be available and secure even if the account or the cloud storage provider is compromised.
Several companies offer strong disk encryption at the user and network levels. Protecting sensitive data in use might require full disk and memory encryption, but that might preclude some apps from being able to process the data, so strong access controls and limited access to specific data sets are essential alternatives.
Effective encryption key management is critical, encompassing everything from logging keys in a register to facilitating full lifecycle supervision. The keys themselves should be securely stored separately from the encrypted data, with backups off-site and audited regularly. Multifactor authentication should be implemented for both the master and recovery keys. Some cloud encryption providers offer to manage encryption keys which might be attractive to organizations that lack in-house skills and resources. However, regulatory compliance requirements might require some companies to internally hold and manage keys.
While there are challenges associated with cloud encryption, the standards, regulations and privacy requirements associated with it make it an essential cybersecurity control for most organizations. Cloud providers now offer a variety of platforms to fit a range of data center needs and budgets.
Defense-in-depth is another cloud computing security measure that can be used by itself or in combination with encryption. Learn how defense-in-depth works to provide public cloud data security.





