
Getty Images/iStockphoto
How do digital signatures work?
Digital signatures add a level of security to online agreements, which can prevent bad actors from impersonating other individuals or tampering with sensitive contracts.
To go paperless or speed up confirmation of legal and business agreements, organizations have long relied on digital signatures.
The market for digital signatures -- a highly secure type of e-signature -- is mature. Organizations can deploy these software tools across various use cases, said Viky Manaila, trust services director at Intesi Group and president of the Cloud Signature Consortium (CSC). Yet, there is no one-size-fits-all e-signature practice. Organizations must combine different types of signatures to meet various situations. For example, low-risk situations may only require a basic e-signature, such as "a simple scribble on a touchscreen," Manaila said.
However, more sensitive use cases require trust service providers to issue digital signatures. These secure e-signatures ensure signer authentication, nonrepudiation and document integrity.
Digital signatures vs. e-signatures
Organizations must understand the difference between digital signatures and e-signatures so they can implement a level of security that meets their needs.
An e-signature is a broad term that includes any signature a user sends electronically. Some e-signatures, such as those retail stores use for small transactions, don't require identity verification. However, other types, such as digital signatures, involve a strict authentication process.
The digital signature process uses public key infrastructure to prevent tampering and impersonation within digital communications. This process encrypts, or locks, a copy of an agreement with a private key before an organization requests another party to sign it. The tool then sends a corresponding public key -- with a digital certificate attached -- to the other party, and only this key can decrypt the locked copy. If the public key successfully decrypts the locked message, the signer knows the message came from the right person and hasn't been altered.
To create a digital signature, organizations typically use an e-signature system. E-signature systems offer digital signature capabilities, but they can also streamline workflows. For example, they can send reminder notifications to late signatories and assign roles to specific individuals.
What are digital signatures used for?
People can use digital signatures for anything with a signature requirement. However, organizations typically use digital signatures to validate important transactions. Those include the following:
- Real estate purchase and sale agreements.
- Sales contracts.
- Insurance agreements.
- Tax documents and forms.
- Construction change orders.
- Clinical trials.
- Loans.
- Mortgages.
- Leases.
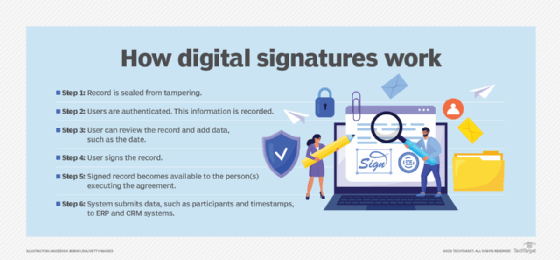
How digital signatures work
Digital signatures rely on digital certificates that trust service providers issue to signers. These providers are legal entities that use processes and tools in accordance with a national authority, such as the U.S. government or EU, to verify e-signatures' authenticity.
"The trust service provider verifies the identity of the signer prior to the issuance of the digital certificate using various mechanisms, [such as] near-field communication, automated video-based identity documents and biometric verification," Manaila said.
After the trust service provider verifies the signer's identity, it issues the digital certificate in the cloud. It stores the required cryptographic keys on a hardware security module (HSM) and protects it with two-factor authentication (2FA). These security measures let people sign documents and get digital certificates from any type of platform, device or smartphone, Manaila said.
Some countries issue electronic identification cards that store the owner's biometric data, such as their fingerprint or facial structure, on a chip. Citizens and organizations can use these cards to prove their identity online and quickly obtain a digital certificate.
How cloud affected the digital signature landscape
Before the proliferation of cloud services, organizations relied on physical devices, such as security tokens or smart cards, to protect their digital certificates with an HSM. This traditional approach posed implementation challenges. For example, the approach isn't user-friendly because it requires users to carry a physical device, Manaila said.
Cloud tools, on the other hand, store the cryptographic keys on the cloud provider's HSM so organizations don't need to track physical tokens or replace them over time. Cloud products are also more scalable and require no physical maintenance costs.
The digital signature landscape changed after the CSC standardized remote, cloud-based digital signatures with its open source API. This technology offers the following benefits:
- Generates remote digital signatures across desktop, web and mobile devices.
- Protects legally binding signatures with 2FA.
- Integrates with various ERP and digital transaction management systems.
- Reduces IT governance costs.
- Ensures compliance with e-signature laws in the U.S. and EU, such as the Electronic Identification, Authentication and Trust Services Regulation.
Security benefits of digital signatures
Digital signature technology can help organizations prevent bad actors from tampering with important transactions. Security benefits include the following:
- Links signer's identity to the signature.
- Makes the signer legally responsible for their actions.
- Securely stores the digital certificate's cryptographic keys on a certified HSM and protects them with 2FA.
- Offers access control to strengthen security.
- Can prove a signature's authenticity in court.
Despite these benefits, digital signatures also come with challenges. For example, they add an extra step into the e-signature process, so organizations should only use them in instances that require strict security. Also, users must learn to manage the required tools and processes, which requires training.






