DNS attack
What is a DNS attack?
A DNS attack is an exploit in which an attacker takes advantage of vulnerabilities in the domain name system. When successful, they can hinder the functionality of DNS servers, redirect users to malicious websites without their knowledge or gain unauthorized access to an organization's resources, such as sensitive or confidential data.
What is the domain name system and how does it work?
To understand how DNS attacks work, it is important to first understand how the domain name system works. DNS is a protocol that translates a user-friendly domain name, like WhatIs.com, into the computer-friendly IP address 206.19.49.154. When an end user types the people-friendly domain name WhatIs.com into a client's browser, a program in the client's operating system called a DNS resolver looks up WhatIs.com's numerical IP address.
To do this, it first checks its own local cache to see if it already has the IP address for WhatIs.com. If it doesn't have the address, it queries a DNS server to see if it knows the correct IP address for WhatIs.com. DNS servers are recursive, which simply means they can query each other to either find another DNS server that knows the correct IP address or find the authoritative DNS server that stores the canonical mapping of the WhatIs.com domain name to its IP address. As soon as the resolver locates the IP address, it returns the address to the requesting program and caches the address for future use.
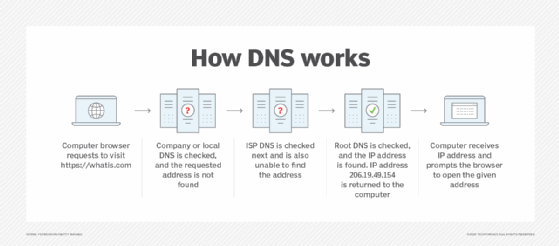
The user doesn't have to type or remember the IP address of every site. All they must do is type the URL in the browser bar or a search engine like Google. The DNS and the system's DNS resolver will work in the background to present the appropriate results.
How do DNS attacks work?
Although the DNS is quite robust, it was originally designed for usability, not security. For this reason, it is vulnerable to many kinds of DNS attacks, which are explored in detail in a later section.
To carry out an attack, attackers typically take advantage of two facts. One, organizations are usually unable to monitor the flow of traffic between remote clients and DNS servers; and two, the communication between clients and the three types of DNS servers happens in plaintext. This type of unencrypted communication creates a vulnerability that attackers can exploit.
Although the specific mechanics differ from one type of attack to another, most DNS attacks involve some kind of manipulation or exploitation of the DNS to benefit the attacker. Typically, threat actors execute such attacks by intercepting the DNS query sent by the client browser to the DNS resolver. They also send a fake response to the browser before the legitimate response arrives from the DNS resolver and authoritative DNS server -- one of the three DNS servers. Another popular attack strategy is to log in to a DNS provider's website with stolen credentials and redirect DNS records.

Types of DNS attacks
There are many types of DNS attacks that threat actors can execute:
Zero-day attack
A zero-day attacker exploits protocol stack or DNS server software that was previously unknown to the victim. Since the victim doesn't know the vulnerability exists, they wouldn't have taken an action to fix it, leaving a security gap that attackers can then take advantage of.
Cache poisoning
The cache poisoning attacker manipulates or corrupts a DNS server by replacing a legitimate IP address in the server's cache with that of a rogue address. By doing so, they can redirect traffic to a malicious website that mirrors the original site and collect information that might be sensitive or confidential, such as credit card numbers or passwords.
Since the DNS resolver stores the details of the bogus website, it continues to redirect users to that website, exacerbating the impact of the attack. Cache poisoning attacks are also known as DNS poisoning or DNS spoofing. Some attackers leverage cache poisoning attacks to initiate other attacks.
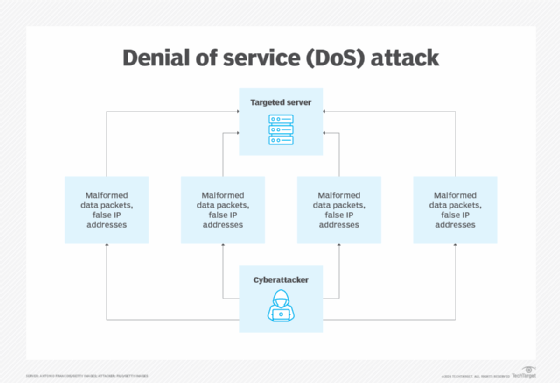
Denial of service (DoS)
In a DoS attack, a malicious bot sends more traffic to a targeted IP address than the site can handle. This traffic surge prevents the target from resolving legitimate requests, and legitimate users are prevented from accessing the site.
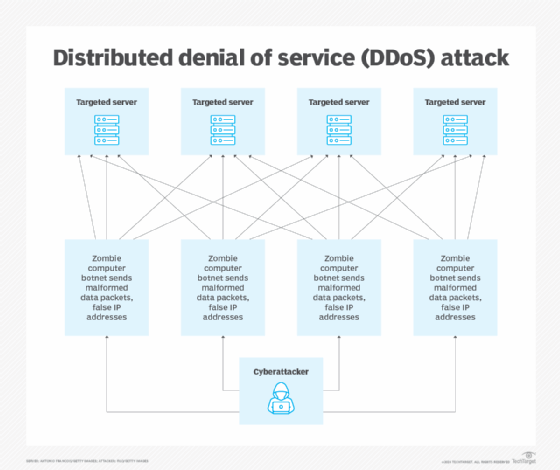
Distributed denial of service (DDoS)
A DDoS attack is like a DoS attack on steroids. To launch a DDoS attack, the attacker uses a botnet, which is a large network of malicious computers, to generate massive amounts of resolution requests to a targeted IP address. Like in a DoS attack, the target is flooded with fake traffic, making it unavailable to legitimate users.
The adversary can also amplify the attack by exploiting the DNS protocol by sending DNS queries -- using many spoofed IP addresses -- to many servers with open DNS resolvers. The more spoofed addresses and open resolvers they use, the more they can overwhelm the target server with traffic and limit availability to genuine users.
DNS amplification
A DNS amplification attack is a type of DDoS attack. To execute it, the attacker takes advantage of a DNS server that permits recursive lookups and uses recursion to spread the attack to other DNS servers.
Fast-flux DNS
In a fast-flux attack, the attacker swaps DNS records in and out at a very high frequency to redirect DNS requests and avoid detection. As a result, the victim struggles to track and block the malicious domain or domains.
DNS tunneling
An attacker sends data packets disguised as DNS queries to a remote server, which then sends DNS responses back to the attacker. This creates a tunnel that allows them to bypass firewalls and exfiltrate data from the network.
Impact of DNS attacks
Today, DNS attacks are very common. Most of them take advantage of the communication that happens between clients and servers. A single attack can have devastating consequences on the affected organization and its users.
For example, the company's website could become unavailable to users, harming its business outcomes. A DDoS attack against an e-commerce site can prevent users from making purchases, affecting the company's sales and revenues.
A DNS attack, particularly one that results in users being redirected to a malicious website, can affect the company's reputation. Further, it can lead to serious data breaches that can result in the loss of customer confidence, legal action and regulatory punishments.
Attackers also execute DNS attacks to install malware on enterprise systems. The malware can affect the performance of a system and the employees that use that system for their work. It can also cause some devices to become unusable, resulting in business downtime. Many types of malware allow adversaries to compromise or steal data, resulting in data breaches.
How to prevent DNS attacks
To defend against DNS attacks, experts recommend implementing multifactor authentication when making changes to the organization's DNS infrastructure. Operations personnel should also monitor for any changes publicly associated with their DNS records or any digital certificates associated with their organization. Another strategy is to deploy DNS Security Extensions, which strengthens authentication in DNS by using digital signatures based on public key cryptography.
To lessen the chance of a DNS attack, server administrators should also take the following steps:
- Use the latest version of DNS software.
- Deploy a DNS firewall.
- Consistently monitor traffic and all logs generated by the DNS resolver.
- Configure servers to duplicate, separate and isolate the various DNS functions.
- Regularly audit DNS zones and restrict DNS zone transfers.
- Harden recursive DNS servers with robust access controls.
- Implement network segmentation.
- Regularly patch and update -- or upgrade -- all systems.
Companies should understand what denial-of-service and distributed denial-of-service attacks are and how they work. Learn how DoS and DDoS attacks differ and the damage they cause.







