security information management (SIM)
What is security information management (SIM)?
Security information management (SIM) is the practice of collecting, monitoring and analyzing security-related data from computer logs and various other data sources. A security information management system (SIMS) can help automate this practice to reduce manual effort and improve the efficiency of both the SIM program and the organization's broader cybersecurity program.
Over the years, the separate practices of security information management and security event management have evolved into one combined practice called security information and event management, or SIEM.
The need for security information management
As the cyberthreat landscape expands, organizations are vulnerable to many kinds of security threats and risks. From viruses, malware and phishing scams to social engineering, DDoS attacks, cyberextortion and advanced persistent threats (APT), companies are at risk of a broad variety of cyber attacks. To protect assets from cyber attackers and prevent data breaches, companies need to deploy diverse security systems and controls.
There is clearly a need for these multiple systems for organizations adopting a defense‐in‐depth (DiD) cybersecurity strategy. DiD aims to balance any weaknesses in one security control with the help of the strengths of other complementary controls.
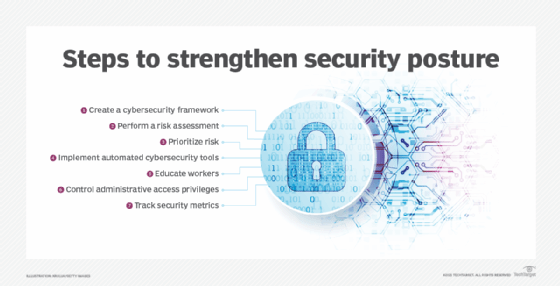
However, security professionals need to see a holistic and comprehensive picture from the data generated by all these tools. Only then can they take action to strengthen the organization's security posture. Security information management is intended to fill that need.
SIM enables cybersecurity professionals to access and analyze security information from numerous sources, including the following:
- antivirus software;
- intrusion detection systems (IDS);
- intrusion prevention systems (IPS);
- endpoint detection and response systems (EDR);
- file systems;
- proxy servers;
- firewalls;
- routers;
- servers; and
- switches.
SIM systems collate data from all these sources to provide actionable insights. They may also perform the following functions:
- monitor security events or attacks in real time;
- display real-time views of activities;
- translate event data from various sources into a common format, such as XML;
- aggregate and correlate data from multiple sources to create a comprehensive picture of the state of enterprise security;
- segregate data to help administrators differentiate between real threats and "false positives" (threats that appear real but are not);
- provide automated incident response;
- detect suspicious activities and send alerts to authorized personnel to take action; and
- generate reports to help leadership discern the organization's security posture.
Reporting in security information management
Reports are a critical part of any SIM program. A reliable SIM tool will generate regular reports, often in visual formats such as graphs or charts. Security personnel can use these reports to detect security events, identify suspicious behaviors, and detect and address ongoing threats.
The reports can also be used to assess the performance and effectiveness of the enterprise network's security controls. Over a longer period, SIM systems and reports enable organizational leadership to continually evaluate the company's security posture and make better decisions about additional security investments required to strengthen it.
Key processes in security information management
SIM is an ongoing, multistep approach rather than a series of linear, one-time steps. A SIM tool and program enables security personnel to gather, manage, optimize and use security data to identify threats and vulnerabilities, and take action to protect the organization.
In general, SIM involves these steps:
- data collection;
- data preprocessing and normalization;
- data analysis;
- incident identification; and
- incident response.
Data collection. As noted, SIM platforms collect security data from a variety of sources, including the following:
- gateway devices, such as routers and firewalls;
- network appliances, such as IPS, content filters and antivirus software; and
- application servers, web servers and database servers.
Basically, a SIM system collects and aggregates security data from any device or application that logs event information. That data is sent to the SIM platform via widely supported and common protocols such as syslog, Simple Network Management Protocol (SNMP) and Simple Mail Transfer Protocol (SMTP).
Data collection can also be performed by software agents that collect data from devices that don't forward event logs natively, like Windows Server. These agents are usually device-specific and create extra maintenance and management challenges for security teams.
Another popular data collection method is via application programming interfaces (APIs) that provide greater contextual detail for collected data but also add to the complexity of the SIM program.
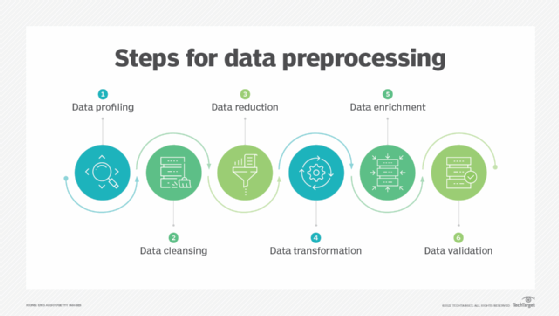
Data preprocessing and normalization. A SIM system may not be able to make sense of all received data, much less generate actionable insights or reports from it, so data preprocessing and normalization may be required.
Preprocessing typically involves file manipulation and data normalization to map data into an acceptable format that the SIM system can use to create reports and insights. Data from different sources (e.g., firewalls, antivirus appliances and content filters) is almost always formatted differently, making it harder for security teams to review the data or use it for further analysis or insights. Preprocessing and normalization modules extract and reformat data, ensuring that data from different systems all use a common frame of reference and identifier scheme.
One challenge during this stage is synchronizing all system clocks. Adding a timestamp to an event as soon as it arrives at the SIM appliance can help establish a common network time for better synchronization.
Data analysis. Most SIM systems provide data filtering and aggregation to separate relevant from extraneous data. Tools also correlate events of interest and assess incidents to provide guidance to security teams.
Filtering can be either, or both, positive and negative. Positive filters capture data about suspicious or known malicious events that should be analyzed further to mitigate impact and minimize damage. Negative filters eliminate known events that are not threats, such as false positives. SIM tools should also be able to capture anomalous events that don't fit neatly into the positive or negative category but nonetheless warrant further investigation.
Aggregation is part of the data analysis in SIM. In this step, events are further consolidated to provide an aggregate count that helps security personnel with further analyses.
Incident identification. After aggregating events and isolating the significant events, the SIM platform correlates events to determine the sequence and identify an attack pattern. Finally, it matches patterns to determine if there is a breach that requires initiating an incident response.
Incident response. SIM systems collect data from multiple sources, filter events based on relevancy and correlate data to generate actionable insights, all of which helps with incident response.
There are many incident response frameworks that organizations can use in their cybersecurity programs. In general, incident response is a cycle involving these key steps:
- detect the incident;
- contain the incident;
- eliminate or mitigate the incident;
- recover from the incident; and
- learn and adapt from the incident.
See also: benefits of a security operations center, key enterprise SOC team roles and responsibilities, building an effective security operations center framework and how security operations centers work to benefit enterprises.








