
maxkabakov - Fotolia
Salesforce pushes forward with DNS security standard
A Salesforce-backed DNS security model to prevent downtime could become standard for multi-tenant cloud providers.
Salesforce is building a multi-provider DNS security model to ensure that an attack against one of its DNS providers won't mean significant downtime for Salesforce users.
The move could lead other large, global SaaS platform providers to adopt a similar business continuity strategy. Several large DNS providers are already implementing the model, said Shumon Huque, Salesforce principal software engineer, during DNSSEC vendor NS1's annual user conference.
The project, in the works for more than a year and led by Salesforce in conjunction with NS1 and DNS provider Verisign, could prevent the types of downtime problems other companies experienced in recent years. A 2016 attack on Dyn temporarily took down Twitter, Reddit, Spotify, GitHub and The New York Times for much of the eastern United States.
"It allows an organization to survive the complete and catastrophic failure of any single DNS provider with virtually no downtime," Huque said.
What's new in Salesforce DNS security
DNSSEC uses encryption to enable large websites, such as those hosted by cloud applications vendors, to build redundancies into their network to failover and maintain uptime if one DNS provider goes down. Current DNSSEC can accomplish this already in some situations.
Salesforce's DNS security model is predicated on multiple DNS providers agreeing on a combination of public and private encryption keys. Doing so adds advanced capabilities such as global server load balancing and dynamic response protocols in the event one of its DNS providers goes down.
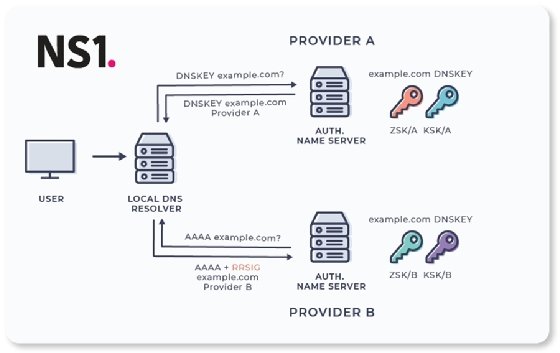
For Salesforce users, that means the site is less likely to go down in a given geographic zone when one of its DNS providers is hacked. But getting competing DNS vendors to agree on a standardized set of encryption keys is not a simple proposition, said Eric Hanselman, a 451 Research analyst.
"Salesforce -- because they know this is a key part of how they want to build their infrastructure -- is taking the lead and helping promote the acceptance of the standard," Hanselman said. "The trick is that you have a shared root of trust. Everybody is trusted independently, and they trust each other."
The Salesforce DNS security model is approved and will be published by the Internet Engineering Task Force as a request for comments, Huque said at NS1's Insight user conference. That, Hanselman said, typically means other companies will accept the model as a specification to enhance their own multi-vendor DNSSEC strategies.






